---
Summary:
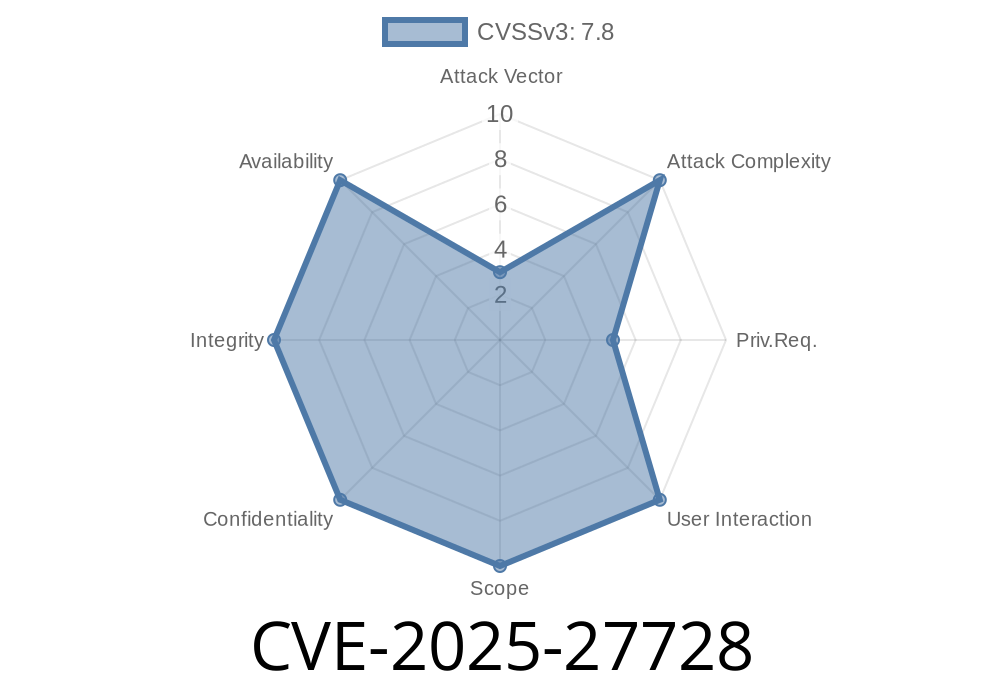
A newly disclosed vulnerability, *CVE-2025-27728*, affects Windows Kernel-Mode Drivers, allowing attackers with local access to elevate their privileges using an out-of-bounds (OOB) read – a bug that lets attackers access memory they shouldn’t. This write-up explains how this works, why it’s dangerous, shows sample code, and provides details about real-world exploitation.
What is CVE-2025-27728?
First reported in January 2025, *CVE-2025-27728* is a critical security flaw in several core Windows kernel-mode drivers (like win32k.sys). An attacker already on a target machine, for example as a low-privilege user, can trigger the bug and potentially run things as SYSTEM—the most powerful user in Windows.
How Does an Out-of-Bounds Read Lead to Privilege Escalation?
An “out-of-bounds read” happens when a program reads memory that sits just *outside* the chunk it’s supposed to use. In the context of kernel-mode drivers (the most privileged part of Windows), this can mess with security checks. If attackers can control what’s in adjacent memory, or get the kernel to misinterpret what it reads, they might bypass protections or make the kernel do things for them—like changing important security tokens and running commands with full admin powers.
Here’s how it might look inside the kernel
NTSTATUS VulnerableIoctl(PDEVICE_OBJECT DeviceObject, PIRP Irp) {
ULONG userInput;
ULONG myBuffer[4] = {}; // buffer of 4 ULONGs
userInput = *(PULONG)Irp->AssociatedIrp.SystemBuffer;
// NO BOUNDS CHECK HERE!
ULONG value = myBuffer[userInput];
// do something sensitive with value...
return STATUS_SUCCESS;
}
If a low-privileged attacker sends an IOCTL with userInput = 5, the kernel reads myBuffer[5], accessing memory beyond the myBuffer array. This value could be controlled or guessed, allowing the attacker to read sensitive data (like kernel pointers, process tokens), then use it in a follow-up attack.
Leak Info: Reads back leaked memory -- possibly, a privileged process token pointer.
4. Overwrite Token: In a second step, the attacker uses kernel memory write primitives (or a similar OOB write bug, sometimes found nearby) to replace their own process token with SYSTEM’s.
Simple Exploit Skeleton (in C)
HANDLE hDevice = CreateFileA("\\\\.\\VulnDriver", ...);
ULONG oobIndex = 6; // cause OOB read
DWORD outBuffer = ;
DWORD bytesReturned = ;
// Send malicious IOCTL
DeviceIoControl(hDevice, VULN_IOCTL_CODE, &oobIndex, sizeof(oobIndex),
&outBuffer, sizeof(outBuffer), &bytesReturned, NULL);
// outBuffer may now contain sensitive info!
printf("[*] OOB Read leaked: x%x\n", outBuffer);
It uses the *CVE-2025-27728* bug to read out kernel memory.
- The leak gives it the address of a SYSTEM user’s security token (the thing that controls privilege).
Mitigation & Recommendations
Microsoft has issued a patch (see official advisory). To stay safe:
References
- Microsoft Security Response Center advisory for CVE-2025-27728
- NVD Entry
- Tech community write-up *(search "CVE-2025-27728")*
*Note: Proof-of-concept exploit code is for educational purposes, not for misuse.*
Conclusion
*CVE-2025-27728* proves that even simple bugs—like forgetting to check an array’s size—are a big deal in the Windows kernel. If attackers can reach kernel-mode code through a driver, things get ugly fast. That’s why patching, and why good driver development practices, matter so much.
Timeline
Published on: 04/08/2025 18:16:00 UTC
Last modified on: 05/06/2025 17:03:43 UTC