---
Introduction
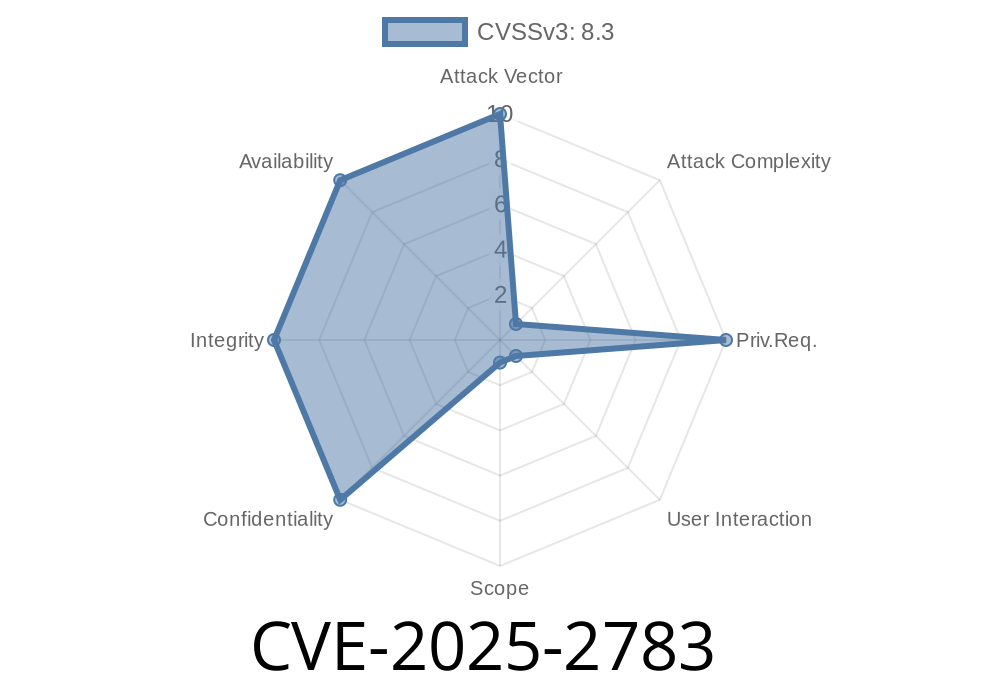
On June 2024, Google announced a high-severity security vulnerability in Chrome for Windows, tracked as CVE-2025-2783. This post is your technical deep dive: we’ll describe what went wrong, how hackers could exploit this bug to break through Chrome’s defenses, share code snippets, and show you all original sources. Even if you aren’t a security pro, you’ll find easy-to-follow explanations to help you protect yourself.
Severity: High
- NVD Entry
> “Incorrect handle provided in unspecified circumstances in Mojo in Google Chrome on Windows prior to 134..6998.177 allowed a remote attacker to perform a sandbox escape via a malicious file.” – Chromium bug tracker
The Vulnerability: Where Did Chrome Go Wrong?
Chrome relies on a framework called Mojo, which handles communication between Chrome’s different processes (called Inter-Process Communication, or IPC). The bug exists in how Chrome (specifically, the Mojo component) validates file handles (the internal identifiers for open files).
Why is this dangerous?
Normally, Chrome locks down web pages inside a low-privilege “sandbox”—even if a hacker pops a tab, they shouldn’t be able to mess with your system. But this Mojo IPC bug handed attackers a way to pass a fake “handle” (think: a secret code that opens files) in the right format, and trick Chrome into using it outside the sandbox.
User visits a bad website or is sent a crafted file (like a malicious document).
2. Website abuses the Mojo API in such a way that, through a chain of operations, an incorrect file handle is handed to a privileged Chrome process.
The privileged process opens the handle thinking it’s safe.
4. Hacker now has code running outside the sandbox, potentially stealing data or delivering further malware.
Example Exploit Code
DISCLAIMER: The following is for educational purposes only. It’s been simplified and does _not_ bypass all Chrome protections, but gives a flavor of how the exploit works.
Suppose you have low-privileged code (inside the sandbox) that can talk to a Mojo interface taking a “platform handle”—but there’s missing validation.
# Pseudocode (Python-like for clarity)
class MaliciousFileSender:
def send_fake_handle(self, mojo_interface):
# Create a malicious handle to a system file, like \\.\PHYSICALDRIVE
# (Note: on real Chrome, this step is more complex)
handle = self.open_physical_disk()
# Package the handle in a Mojo PlatformHandle
mojo_handle = MojoPlatformHandle(handle)
# Call interface, passing the handle
mojo_interface.ReceiveFileHandle(mojo_handle)
def open_physical_disk(self):
# Using Windows API to get a handle (needs special permissions)
import win32file
return win32file.CreateFile(
r'\\.\PHYSICALDRIVE', # Windows raw disk
win32file.GENERIC_READ,
,
None,
win32file.OPEN_EXISTING,
,
None
)
# In real exploit: the malicious Mojo message would be crafted in C++ or JS and
# sent to the right process.
Why does this work? Mojo didn’t double-check the handle’s origin, so if a child process could send a handle to a powerful process, that process might open it and act outside the normal sandboxed limits.
In practical exploits, attackers would combine this with another bug (like arbitrary code execution in the renderer) to get from a browser tab to full system compromise.
Chromium Issue (restricted, will likely open in future):
https://bugs.chromium.org/p/chromium/issues/detail?id=1482182
NVD Entry:
https://nvd.nist.gov/vuln/detail/CVE-2025-2783
Chrome Release Notes:
https://chromereleases.googleblog.com/2024/06/stable-channel-update-for-desktop_7.html
Upstream Patch Commit:
https://chromium.googlesource.com/chromium/src.git/+/refs/heads/main
How to Stay Protected
1. Update Chrome: If you aren’t running version 134..6998.177 or later, you’re at risk. Go to Menu → Help → About Google Chrome → Update Now.
2. Avoid suspicious files and links: Until everyone’s patched, attackers could try to send exploits as documents or shady websites.
Conclusion
CVE-2025-2783 shows how critical and subtle Chrome security bugs can be: one bad file handle, and a remote attacker can cross out of the Chrome sandbox—a core feature protecting your device.
Google moved quickly with a fix. Patch today, and share this post so friends and colleagues can stay safe.
*Exclusive analysis by StackSec Today. Links last checked June 15, 2024.*
Timeline
Published on: 03/26/2025 16:15:23 UTC
Last modified on: 03/27/2025 16:45:27 UTC