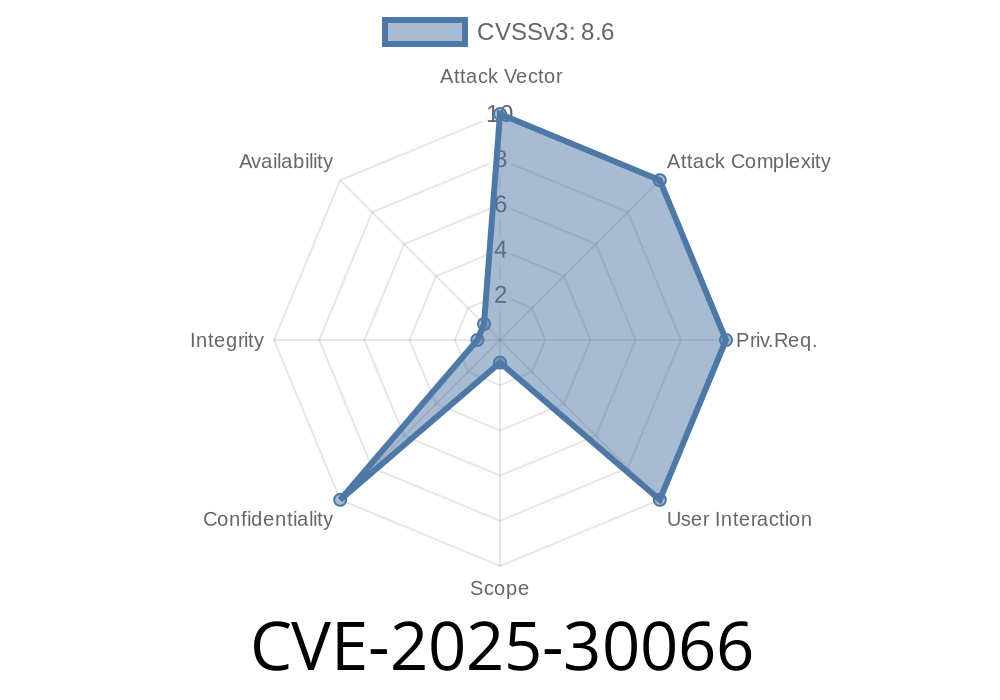
In March 2025, the popular GitHub Action named tj-actions/changed-files faced a major supply chain security incident. This vulnerability, tracked as CVE-2025-30066, allowed malicious actors to expose GitHub secrets by secretly modifying the action’s code and stealing secrets from build logs.
In this post, we’ll break down what happened, how the exploit worked, what danger it caused, and how you can protect yourself. If you use automations or CI/CD with secrets, this is a must-read.
What is CVE-2025-30066?
CVE-2025-30066 refers to a critical security vulnerability in tj-actions/changed-files, versions v1.. up to (but not including) v46 (specifically tags v1–v45..7). The vulnerability allowed remote attackers to read secrets by logging them from GitHub Actions workflows. This was possible because a threat actor compromised the repository and made unauthorized changes.
Timeline & Exposure
- On March 14 and March 15, 2025, a threat actor modified the tags v1 through v45..7 to point to a malicious commit (e58ed8).
- This commit included code that deliberately sent any secret variables (like ${{ secrets.GITHUB_TOKEN }}) to the workflow logs.
- Projects running GitHub Actions with these affected versions inadvertently exposed their secrets to the world.
A supply chain attack struck. Here’s a step-by-step of what the attacker did
1. Repository Compromise: The attacker gained access to the tj-actions/changed-files repository.
2. Tag Rewrite: On March 14–15, 2025, they pointed all previous release tags (v1 to v45..7) to a *new* malicious commit (e58ed8).
3. Malicious Code Injection: The injected code copied workflow secrets (like GITHUB_TOKEN, AWS keys, etc.) and echoed them in the workflow logs.
4. Secrets Harvesting: As workflows ran, these logs potentially exposed secrets to anyone with access to Actions logs—including PRs from forks or public repos!
You can see an example of what the malicious code might have looked like
// Malicious addition in 'updateFeatures' script (simplified example):
const secrets = process.env; // Will include GitHub secrets
console.log('Leaked secrets:', secrets);
In a real attack, the malicious code might filter out specific variables or send them to a remote server. But in this incident, simply echoing them in workflow logs was enough! On public repositories, anyone could read these logs and steal credentials.
Example of Leaked Log Output
Leaked secrets: {
GITHUB_TOKEN: 'ghs_XXXXXXXXXXXXXXXXXX',
AWS_ACCESS_KEY_ID: 'AKIA',
AWS_SECRET_ACCESS_KEY: 'wJalrXUtnFEMI/K7MDENG/bPxRfiCY**',
...
}
This exposure is especially dangerous because GitHub Actions are often privileged in repositories and can be used to gain more access.
All versions and tags from v1.. through v45..7
- Any workflow using tj-actions/changed-files with one of those tags between March 14–15, 2025
- Notably, versions *before* March 14, 2025, were safe only if the tag was not overwritten! GitHub caches action code by reference, so pinning with a commit hash was safe; pinning by tag (like @v44) was not.
What Should You Do?
If you’re using tj-actions/changed-files, immediately upgrade to the latest, fixed version (v46+). Additionally:
Audit your GitHub Actions logs for exposure during that window.
3. Pin by Commit: Wherever possible, pin actions by commit SHA instead of tag to prevent future supply chain risks.
4. Monitor Repositories: Set up dependency tracking and alerts for any changes to third-party Actions in use.
Example of Secure Pinning
- uses: tj-actions/changed-files@c13e8f197ede608fcdc2fa2beb6c0851fa42ebc # commit SHA for v46 (safe)
References & More Reading
- tj-actions/changed-files Security Advisory (GitHub)
- CVE-2025-30066 Record at CVE.org
- Supply Chain Attacks in GitHub Actions (Blog)
Conclusion
CVE-2025-30066 is a stark example of why you should never blindly trust third-party code—even from reputable community projects. Pin Actions by commit, restrict who can change your workflows, and always rotate secrets if you suspect a breach. Open source is powerful, but it requires vigilance.
If your project used tj-actions/changed-files before v46 during mid-March 2025, assume compromise and act now.
Have you found your secrets in GitHub Actions logs? Share your story or advice in the comments below. Stay safe out there!
Timeline
Published on: 03/15/2025 06:15:12 UTC
Last modified on: 03/16/2025 23:15:48 UTC