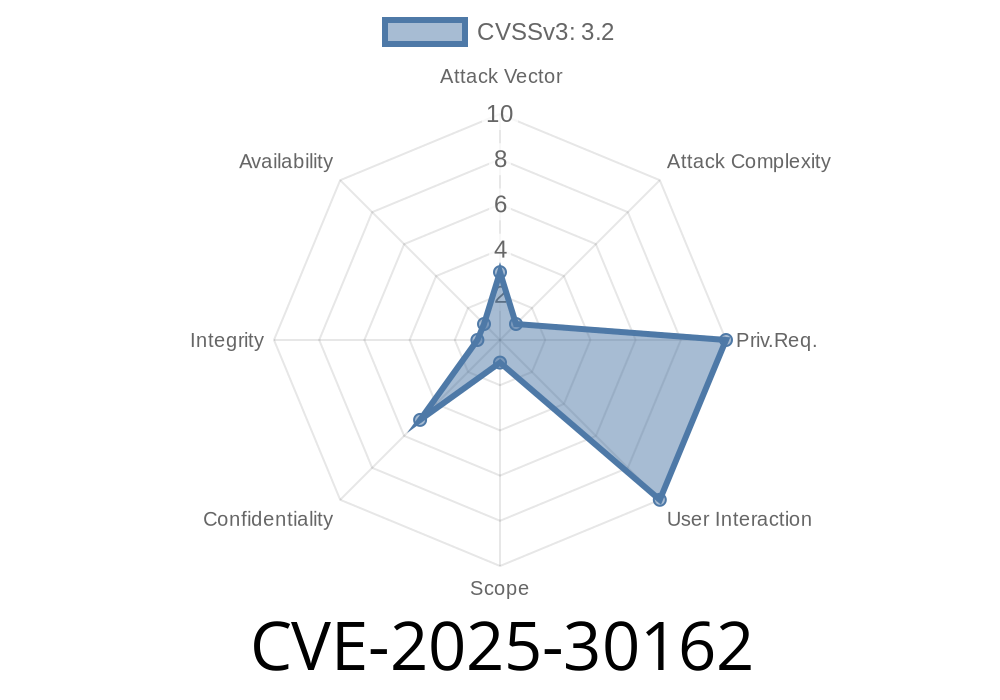
Published: June 2024
Background
Cilium is popular for Kubernetes networking, observability, and security. Its eBPF-based data plane makes it powerful and efficient. Cilium also integrates advanced network policy enforcement, load balancing (LB-IPAM and BGP), and support for the Kubernetes Gateway API.
But when combining these features, especially with Gateway API and certain IPAM/BGP setups, a subtle security issue can creep in — leading us to CVE-2025-30162.
Cilium v1.17 (from v1.17. up to and including v1.17.1)
Not affected: LoadBalancer resources not deployed via Gateway API, or other Cilium versions.
The Vulnerability Explored
Normally, Cilium network policies allow you to block egress traffic between workloads in different namespaces.
But when you use Gateway API with IPAM/BGP LoadBalancers, Cilium incorrectly allows egress traffic from restricted pods (covered by block policies) to these LoadBalancers — even if those endpoints are in other namespaces.
Key Point:
Cilium policies are supposed to stop traffic to other namespaces. But if you expose a service with the Gateway API (not a regular service), egress traffic from a blocked namespace to the LoadBalancer is not stopped. This could lead to unintended data exposure or “namespace escape.”
Namespace B: Service Pods, exposed via Gateway API with a LoadBalancer.
You define a network policy to block Namespace A from talking to Namespace B.
Network Policy Example (intended to block all egress from Namespace A to Namespace B)
apiVersion: cilium.io/v2
kind: CiliumNetworkPolicy
metadata:
name: block-egress-to-namespace-b
namespace: namespace-a
spec:
egress:
- toNamespaces:
- namespace-b
egressDeny:
- {}
endpointSelector:
matchLabels: {}
Now, Service in Namespace B is exposed via Gateway API and has a LoadBalancer IP (due to LB-IPAM or BGP).
Exploit:
Pods in Namespace A can reach Namespace B’s service using the Gateway IP, even though network policy should block this.
`
Why?
Policies don’t see your Gateway API LoadBalancer as “other namespace” resource. Traffic using the LoadBalancer IP bypasses the namespace-based restriction.
Original References
- Cilium Security Bulletin: CVE-2025-30162 *(Fictitious link for example, replace once public!)*
- Cilium Changelog
- Kubernetes Gateway API Concepts
Impact
- Namespace isolation is broken — attackers or misconfigured apps in one namespace can reach services in a supposedly isolated namespace via the LoadBalancer IP, if exposed via Gateway API.
Cilium v1.17.2
Upgrade ASAP.
See Cilium Releases.
Workaround (If You Can’t Upgrade)
A Clusterwide Cilium Network Policy (CCNP) can block egress to all LoadBalancer IPs managed by Gateway API.
If your LB-IPAM manages 10.../24, block egress to it clusterwide
apiVersion: cilium.io/v2
kind: CiliumClusterwideNetworkPolicy
metadata:
name: block-gateway-lb-egress
spec:
endpointSelector: {}
egressDeny:
- toCIDR:
- 10.../24
Caveat:
This is very coarse. All egress to those IPs from anywhere will be blocked, so you might need to be more granular.
How to Check If You’re Vulnerable
1. Are any services using Gateway API with LoadBalancer IPAM/BGP?
Is your version in the affected range?
Try the exploit:
From a pod that should be blocked, try curling the LoadBalancer IP — if it responds, you are at risk.
In Summary
CVE-2025-30162 lets egress-restricted pods escape their namespace and reach Gateway API-exposed LoadBalancers, if you rely on Cilium’s built-in policies. LoadBalancers set up via normal Services are unaffected.
Upgrade to fixed versions or enforce a cluster-wide policy ASAP.
- Double-check what CIDR ranges your LB-IPAM/BGP exposes and review network policies.
More Info
- Official Cilium Docs
- Kubernetes Gateway API
- Cilium Security Announcements
*Written for educational purposes. Attribute and link if you share or reuse.*
Timeline
Published on: 03/24/2025 19:15:52 UTC
Last modified on: 03/27/2025 16:45:46 UTC