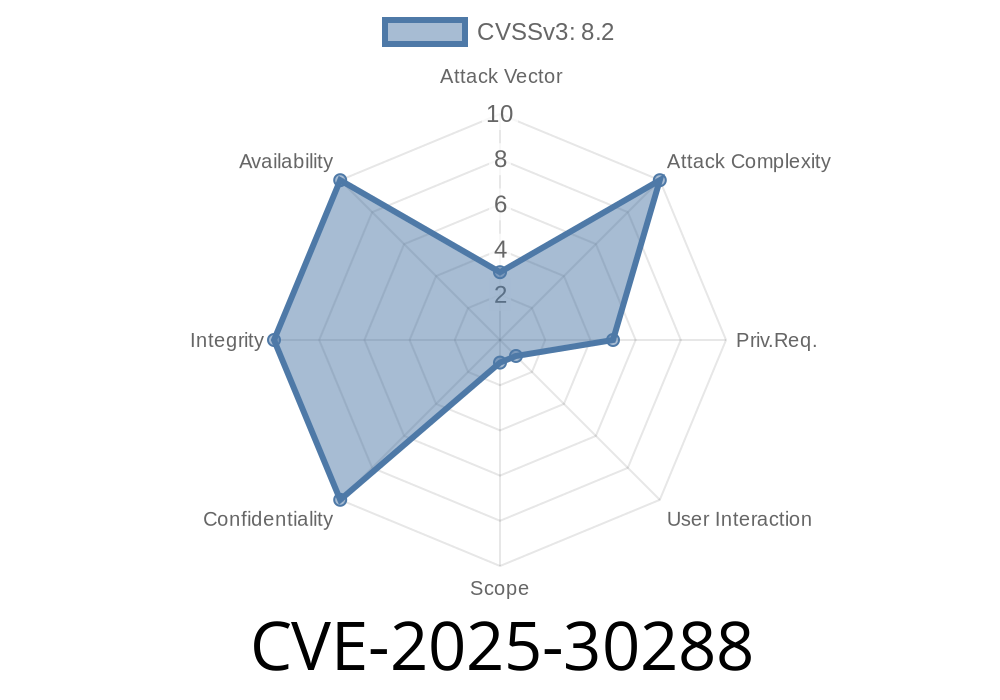
In early 2024, a major vulnerability was disclosed in several versions of Adobe ColdFusion, tracked as CVE-2025-30288. Security teams everywhere are scrambling to understand what’s affected, how it works, and what they can do about it.
In this post, I’ll walk you through a simple explanation of CVE-2025-30288, show you how an attacker could take advantage using sample code, and share resources and patch info you need to stay secure.
ColdFusion 2025. and earlier
It’s classified as an Improper Access Control issue. In simple terms, that means the software doesn’t properly check what users are allowed to do. A local attacker with low privileges (so not a total outsider, but someone with some access) can potentially skip over security features and run code they are not supposed to.
The real danger here is that the attack can let a bad actor *bypass protection* and execute their own code within the ColdFusion server – under certain conditions we’ll explain.
*Already* have a low-privilege account on the target system.
2. Get a user (the "victim") to perform some action inside the ColdFusion app. This could be as simple as clicking on a link or uploading a certain file.
3. The scope of permissions involved is *changed*. Thus, the attacker can evade regular user separation and get code running in a way developers did not intend.
The vulnerability arises because the access controls implemented by ColdFusion don’t strictly enforce who can access specific features – especially around script execution or administrative-like actions.
Let’s go step by step with a simplified scenario
1. The attacker uploads a crafted .cfm file (or abuses a predictable file upload flaw) to a shared directory, possibly made available by the app.
The file includes malicious CFML (ColdFusion Markup Language) code.
3. The attacker tricks a legitimate user into interacting with the file (e.g., by clicking a link or opening a resource).
4. Due to improper access controls, the server runs the attacker’s code with the target user’s privileges.
Example: Exploit Code Snippet (Malicious CFM Payload)
Below is a sample of what a malicious CFML payload could look like. *Do not use this code in production!*
<!--- badfile.cfm: Executing arbitrary OS command through CFEXECUTE --->
<cfset user_input = GetPageContext().getRequest().getParameter("cmd")>
<cfexecute name="cmd.exe" arguments="/c #user_input#" variable="output" timeout="5">
</cfexecute>
<cfoutput>#output#</cfoutput>
If the attacker uploads badfile.cfm to a vulnerable directory and then gets a legitimate user to visit:
http://yourserver/badfile.cfm?cmd=whoami
…the server would run the whoami command and display the output. The permissions used to run the command depend on the user context the attacker manipulates.
4. Why Is User Interaction Needed?
This bug isn’t purely automatic: user interaction is required. The attacker can’t just exploit this over the network; a victim has to be tricked into taking some action that triggers the vulnerable path, like:
Using a compromised template provided by the attacker
That’s why this bug is rated as local and requires social engineering. But once the attacker is successful, the impact is serious.
5. How Can You Protect Your ColdFusion Server?
Adobe’s security bulletin for this flaw:
- Adobe Security Bulletin for ColdFusion (APSB24-17)
Patch Now: Adobe has released hotfixes and patches for supported ColdFusion versions. If you’re running any of the affected versions, install the latest available update *immediately*.
6. References and Further Reading
- NIST NVD Entry for CVE-2025-30288
- Adobe Security Bulletin (APSB24-17)
- ColdFusion Administrator Security Best Practices
7. Conclusion
CVE-2025-30288 is a prime example of how even non-remote access issues can open serious doors for attackers when combined with social engineering, weak access control, and a little creativity.
If you work with ColdFusion, take this one seriously, patch as soon as possible, and review your server access and upload policies. Don't wait for attackers to find that one tricked user.
Timeline
Published on: 04/08/2025 20:15:26 UTC
Last modified on: 04/21/2025 18:33:41 UTC