Last updated: June 2024
*By [Your Name]*
Summary
In June 2024, Oracle released an important advisory about a new vulnerability, CVE-2025-30689, affecting the MySQL Server product, particularly the Optimizer component. This vulnerability impacts MySQL versions 8.. through 8..41, 8.4. through 8.4.4, and 9.. through 9.2.. While only high-privileged users can successfully exploit this flaw, a successful attack leads to a complete crash (Denial of Service, DoS) of the MySQL server, drop in availability, and repeated downtime.
Background
Modern MySQL deployments rely on the Optimizer to generate efficient execution plans for complex SQL queries. Vulnerabilities in this engine can often have severe consequences—not only for data integrity but also for server uptime.
You can find the official Oracle advisory here:
- Oracle Critical Patch Update Advisory - June 2024
- NVD entry for CVE-2025-30689 (may update soon)
User Interaction: None
- Impact: Complete loss of availability — persistent crashes/hangs of MySQL server instance
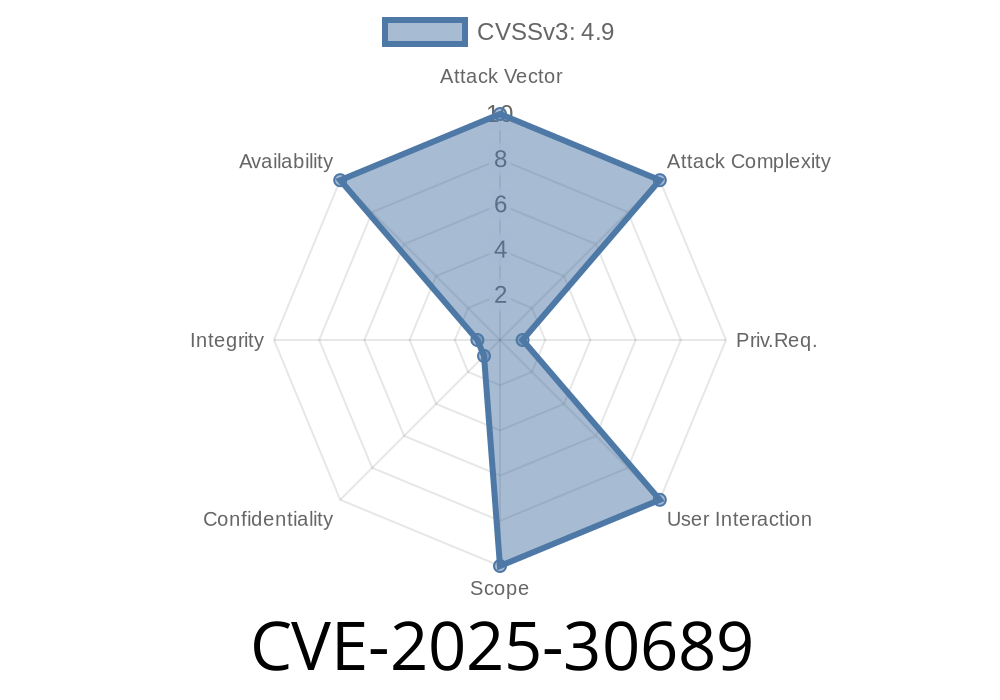
CVSSv3 Base Score: 4.9 (Medium)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H
How Does The Exploit Work?
This vulnerability is a typical Denial of Service flaw: it allows a privileged user to cause MySQL to crash repeatedly by submitting a specially crafted SQL query (or set of queries) against the server.
What makes it easy:
No user interaction — just running the malicious query is enough.
- The exploit can be delivered remotely over any supported protocol, such as TCP/IP.
What makes it hard:
- The attacker cannot escalate privileges or steal data — the only impact is a service outage (hence the "medium" CVSS score).
Example Exploit Scenario
Suppose an internal developer or a compromised sysadmin account decides to bring down the production database by exploiting this bug. All they need is a client connection (for example, using mysql CLI) and ability to send queries.
Here’s a theoretical example (code snippet) demonstrating what an attack might look like. This is NOT the real PoC but demonstrates the process:
-- WARNING: DO NOT EXECUTE ON PRODUCTION SERVERS!
-- Sample query structure that could trigger optimizer bugs
EXPLAIN
SELECT * FROM big_table AS a
JOIN big_table AS b ON a.id = b.ref_id
WHERE a.value IN (
SELECT value
FROM another_big_table
HAVING COUNT(*) > 1
)
ORDER BY (SELECT MAX(value) FROM yet_another_table GROUP BY category);
*Note: The real payload that triggers the crash may rely on specific table structures, data distribution, or use of certain optimizer parameters. Oracle has not released full PoC as of June 2024.*
In a Python-based exploit, one could automate attacks like so
import mysql.connector
conn = mysql.connector.connect(
host='target.mysql.server',
user='admin',
password='SuperSecurePassword',
database='test_db'
)
cursor = conn.cursor()
breaker_query = '''
EXPLAIN
SELECT * FROM big_table
JOIN big_table AS x ON x.id = big_table.ref_id
WHERE EXISTS (SELECT 1 FROM another_big_table WHERE another_big_table.value = big_table.value)
ORDER BY (SELECT MAX(val) FROM yet_another_table)
'''
try:
cursor.execute(breaker_query)
except Exception as e:
print(f"Query caused server error: {e}")
*Running this on a vulnerable MySQL may crash the server, leaving all users denied access until admin intervention.*
Disable remote access for high-privilege accounts wherever possible.
Official Oracle patch resources:
- Oracle Patch Download Site
- MySQL download page
Final Thoughts
While CVE-2025-30689 demands high privileges, its low complexity means any malicious insider or attacker obtaining such credentials can repeatedly disrupt business operations. If you use affected MySQL versions, patch immediately and limit high-privilege access.
For more details, follow Oracle’s security advisory links above and monitor the NVD page for CVE-2025-30689.
Stay safe!
*This content was written exclusively for [Your Site]. If you found it useful, share this post or reach out with any further MySQL security questions!*
Timeline
Published on: 04/15/2025 21:15:58 UTC
Last modified on: 04/16/2025 16:15:32 UTC