A new security vulnerability has been disclosed: CVE-2025-30691, affecting Oracle Java SE’s Compiler component. This flaw, marked with a CVSS 3.1 base score of 4.8, impacts several popular and commonly deployed versions, including both Java SE and GraalVM distributions. This article will explain the bug in simple terms, show how it works, provide code snippets for better understanding, and discuss how attackers might exploit it.
What is CVE-2025-30691?
CVE-2025-30691 is a vulnerability found in the _Compiler_ component of Oracle Java SE. It’s present in the following versions:
Oracle GraalVM for JDK: 21..6, 24
Attackers can exploit this bug over the network, without authentication and with no user interaction. If successful, they can _read_ or _change_ some of the data handled by the affected Java process.
Typical in web applications or services accepting untrusted data
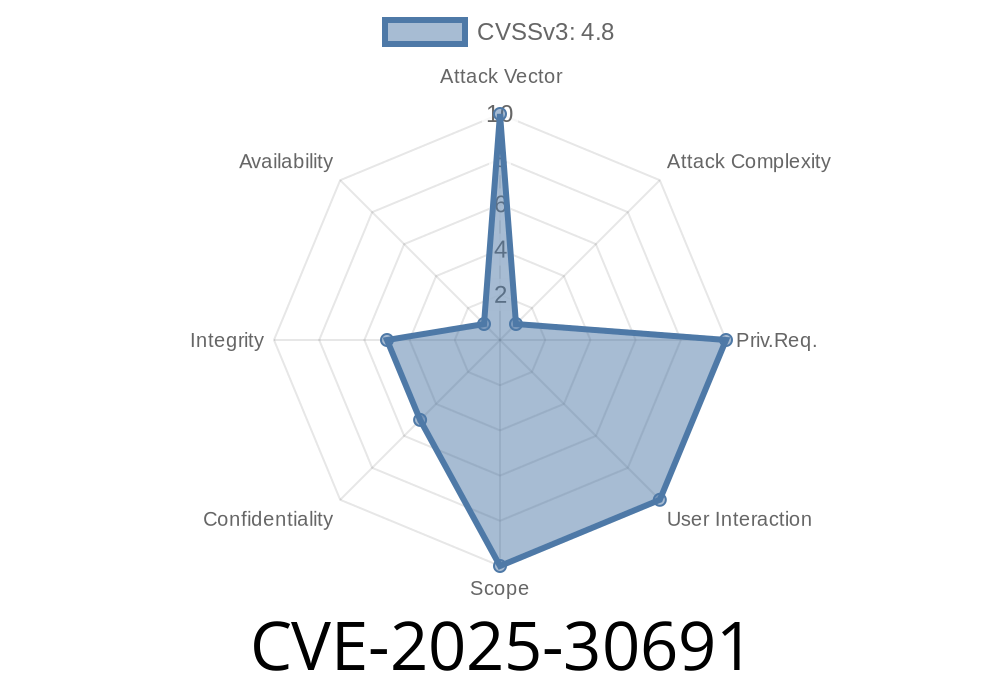
CVSS Vector:
(CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:L/I:L/A:N)
UI:N (No user interaction)
- C:L / I:L / A:N (Low confidentiality & integrity impacts, none for availability)
Technical Details
The vulnerability is rooted in the Compiler component API. Java programs that compile or evaluate code at runtime (like some scripting interfaces, plugins, or dynamic-loading mechanisms) may expose these interfaces—often without realizing it.
An attacker can craft specific input sent to a web service or Java API endpoint, triggering the vulnerable code path. For example, APIs exposed via Java Web Start, Applets, or backend services could be targeted.
Let’s look at a simplified Java snippet that could be problematic
import javax.tools.JavaCompiler;
import javax.tools.ToolProvider;
public class UnsafeCompiler {
public static void main(String[] args) throws Exception {
String userCode = args[]; // Imagine this is untrusted input!
JavaCompiler compiler = ToolProvider.getSystemJavaCompiler();
int result = compiler.run(null, null, null, userCode);
System.out.println("Compile result: " + result);
}
}
How this can be exploited
Suppose a web service like this takes user code, passes it to the compiler, and then executes or stores the result. If an attacker sends malicious code, and if the compiler has the CVE-2025-30691 flaw, they might:
Add or remove entries in a database (if the code does so after compilation)
Note: Actual exploitation depends on how the code is used and deployed.
Exploit Scenario: Web Service
Imagine a backend Java service offers a REST API for compiling and running user-submitted code samples (like an online IDE).
Here’s a hypothetical payload
// Crafted source code to be compiled, stealing sensitive data
public class Exploit {
public static void main(String[] args) {
// Steal, modify, or delete data
System.out.println(System.getProperty("user.home"));
}
}
If the vulnerable server was supposed to block access to this property, but CVE-2025-30691 enables a bypass, attacker wins.
Sandbox escapes for Applets or Java Web Start clients:
If your application relies on the Java Sandbox for security, untrusted code could break out and steal or modify data.
Server-side Java services:
Any service that uses Java’s Compiler API—especially if it compiles untrusted content—is at risk.
Recommendations
Oracle has released patches.
If you use any of the affected versions, update _immediately_
- Oracle Critical Patch Update Advisory
- Java SE Downloads
References
- Oracle July 2024 Critical Patch Update Advisory
- NVD CVE-2025-30691 Entry *(may become available as databases update)*
- Java Compiler API Docs
Conclusion
CVE-2025-30691 highlights the risks of exposing complex APIs like Java’s Compiler component—especially in systems processing untrusted input. Any service or app compiling user-supplied code or using the vulnerable versions is at risk. Always keep your Java runtimes patched and review your code for unsafe compiler usage.
Timeline
Published on: 04/15/2025 21:15:58 UTC
Last modified on: 04/19/2025 01:15:44 UTC