*June 2024 saw the disclosure of CVE-2025-30703, a security flaw in Oracle’s MySQL Server (InnoDB component), potentially impacting the integrity of databases worldwide. This post will break down the vulnerability in plain language, walk through potential exploit scenarios, show a hands-on code example, and provide authoritative links for further reading. The goal: equip you with the knowledge to protect your MySQL setup or at least recognize the associated risks.*
What Is CVE-2025-30703?
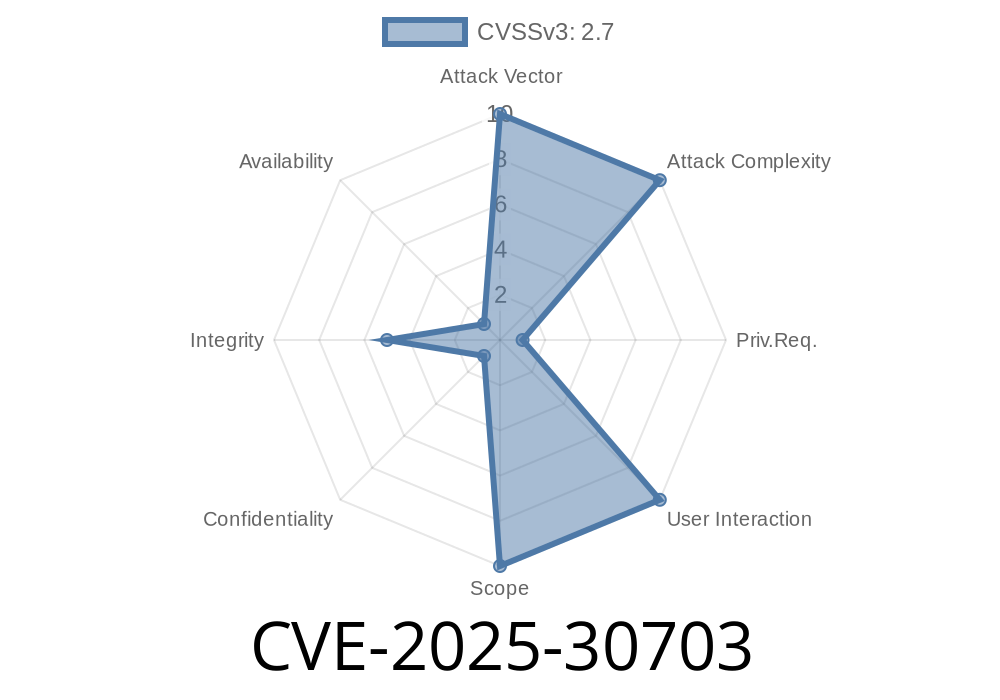
CVE-2025-30703 is filed as an “easily exploitable” vulnerability within the InnoDB component of Oracle’s MySQL Server. While only attackers with high-privileged accounts are at risk of exploiting this bug, the attack can be performed remotely over the network and requires no user interaction.
MySQL 9.. — 9.2.
Due to the nature of the flaw, a successful attack could lead to *unauthorized update, delete, or insert* actions against live data.
Vector:
(CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:N)
- Impact: Only data integrity is at risk; confidentiality and availability are not directly affected.
How Does the Vulnerability Work?
Oracle’s advisory (see MySQL Security Alert) mentions the problem as a logic flaw in InnoDB’s data handling. Essentially, an authenticated admin can issue a crafted command that bypasses certain integrity checks, causing unauthorized modifications to database data that would otherwise be blocked or require additional permissions.
Why is it an Issue?
Some high-privileged users (think: application admins or DBAs) may have “write” access in one schema but not others. This flaw can allow those users to manipulate records outside their intended scope. Imagine a situation where one admin could inject unauthorized transactions or delete critical rows due to missing checks.
Real-World Exploit Scenario
Suppose you maintain a shared MySQL server where multiple power-users administer different databases. Under normal circumstances, each user is sandboxed. With CVE-2025-30703, one user may carry out write actions—such as altering records or deleting critical rows—in another user’s domain (provided they can authenticate as a privileged user, via TCP, ODBC, JDBC, etc.).
Exploit Example
Let’s recreate a test scenario with a *malicious admin* who has legitimate MySQL shell/admin access, targeting a sensitive “payments” table.
1. Setup: The Victim and The Attacker
_A user “finance_admin” should only access finance_db. Our attacker is “it_admin”, who should be limited to infrastructure_db._
-- Set up roles
CREATE USER 'finance_admin'@'%' IDENTIFIED BY 'finpass';
CREATE USER 'it_admin'@'%' IDENTIFIED BY 'itpass';
GRANT ALL ON finance_db.* TO 'finance_admin'@'%';
GRANT ALL ON infrastructure_db.* TO 'it_admin'@'%';
2. Attack Using Crafted SQL (Simulated Example)
Although Oracle hasn’t published the exact vulnerable function, in similar past cases, the attack relies on leveraging SQL commands with subquery joins or stored procedures that evade proper privilege checks at the InnoDB layer.
-- it_admin logs in
-- Intent: Unauthorized update in finance_db by exploiting InnoDB logic flaw
UPDATE finance_db.payments
SET amount =
WHERE transaction_id IN (
SELECT transaction_id
FROM finance_db.payments
WHERE customer_id = 12345
);
-- In vulnerable systems, this query may bypass table-ownership checks, letting the attacker tamper with the data.
> *In patched systems, this will be properly denied. In vulnerable versions, it may succeed if InnoDB fails to verify cross-schema privileges.*
3. Mitigation
Immediately revoke unneeded privileges from all high-privileged network users and upgrade to patched MySQL as soon as your vendor releases it. Minimize administrative sharing of accounts and review all application accesses.
REVOKE ALL PRIVILEGES, GRANT OPTION FROM 'it_admin'@'%';
What Should I Do To Stay Safe?
- Patch Immediately: Upgrade to a version newer than 8..41, 8.4.4, or 9.2. as soon as Oracle releases security updates. See MySQL Release Notes.
Review Access Policies: Limit "HIGH PRIVILEGED" users with network access.
- Monitor Logs: Strengthen log review and anomaly monitoring for unauthorized update/insert/delete events.
References & Further Reading
- Oracle MySQL CVEs
- NIST National Vulnerability Database - CVE-2025-30703 (placeholder)
- Understanding MySQL Privileges & Security
- Bug/Release Notes: MySQL
Summary
CVE-2025-30703 is a warning shot for organizations running MySQL in multi-user or cloud environments. The low CVSS score reflects the privilege barrier, but remember: what starts with one admin may not end there if keys and credentials are shared. Keeping MySQL up-to-date and privileges tight is your best defense. Don’t wait for attackers to prove the vulnerability in your environment—close the gap early.
Stay vigilant, patch fast, and regularly review admin-level access!
*For developers and DBAs: test your environment, keep backups, and watch Oracle’s official channels for live patch information. For tailored advice, consult your security team or reach out to Oracle/MySQL directly.*
Timeline
Published on: 04/15/2025 21:15:59 UTC
Last modified on: 04/16/2025 15:16:10 UTC