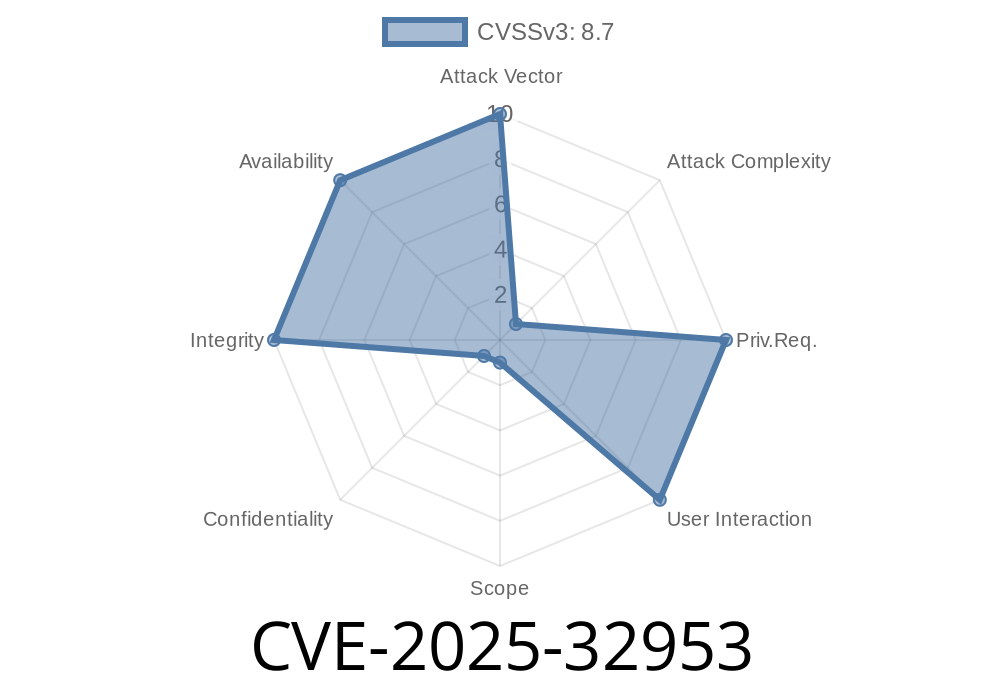
Published: June 2024 <br>CVE ID: CVE-2025-32953
Overview
z80pack, a long-lived emulator for Z80 and 808 CPUs, is widely used in the retrocomputing community. In versions 1.38 and earlier, a dangerous vulnerability was found in its continuous integration (CI) workflows, specifically in its makefile-ubuntu.yml GitHub Actions file. This flaw made it possible to leak the highly sensitive GitHub GITHUB_TOKEN, leaving the project open to malicious modifications and attacks.
This post explains how the vulnerability worked, offers a code snippet example, breaks down the risk, and gives practical mitigation tips. At the end, you'll also find references to the original fix and how users and other open source maintainers can protect similar workflows.
The Vulnerability
In z80pack’s CI pipeline, artifacts generated as release assets were being zipped and uploaded using the GitHub Actions step: actions/upload-artifact@v4.
The artifact, named z80pack-ubuntu, included all files from the current working directory. Unfortunately, this directory also contains an internal Git configuration file: .git/config. During CI runs, this file contains the workflow's GITHUB_TOKEN in plain text, used by actions to authenticate and push changes.
The Problem
If someone could grab the artifact before the workflow finished and the token was invalidated, they could:
Extract the live GITHUB_TOKEN
- Use it to call GitHub APIs on behalf of the repository, with permissions like pushing malicious code, resetting branches, or even rewriting release commits
Though the artifact is meant for later use, there’s a short window after upload where it could be accessed by someone with knowledge of its name or who interferes with logs/artifact listings.
This serious risk was reported and is tracked as CVE-2025-32953.
Below is the relevant part of the old, vulnerable GitHub Actions workflow in makefile-ubuntu.yml
- name: Build Ubuntu Packages
run: |
make clean
make all
- name: Archive build output
run: |
zip -r z80pack-ubuntu .
- uses: actions/upload-artifact@v4
with:
name: z80pack-ubuntu
path: z80pack-ubuntu.zip
Key issue:
The zip -r z80pack-ubuntu . command zipped up everything, including .git/config by default.
Example .git/config snippet from a workflow
[credential]
helper = "!f() { echo username=github-actions; echo password=ghs_1234exampleTOKENabc; }; f"
That means the password line directly exposes the current run’s token.
Download the artifact during the few-second window before workflow completion.
3. Unzip the artifact and extract .git/config.
Modify PRs, issues, or other assets (subject to token permissions)
Anyone with the knowledge and access could use this live token for malicious changes or even erasing traces of their edits, with severe impacts on trust and security for z80pack.
Reported & acknowledged: May 2024
- Fixed in commit: bd95916
The project maintainers quickly patched the workflow
- Excluded sensitive files from the artifact by explicitly picking only the necessary files for zip, or
Improved line example
- name: Archive build output (secure)
run: |
zip -r z80pack-ubuntu ./bin ./README.md
Or using a .zipignore or exclusion with zip
zip -r z80pack-ubuntu . -x "*.git*"
Or simply zipping only the build output (not the entire repo).
Upgrade to v1.39 or later
- Check your downloaded artifacts — if you downloaded old artifacts, don’t reuse their tokens or trust their content
For all open source maintainers
- Never archive or upload the entirety of the build directory without considering hidden or dotfiles
- Always exclude .git/, .env, and other config directories
Further Reading & References
- z80pack Main Site
- CVE-2025-32953 MITRE Record
- GitHub Issue Discussion *(search for “artifact token leak”)*
- actions/upload-artifact Documentation
- Security Best Practices for GitHub Actions
In Closing
CVE-2025-32953 in z80pack is a lesson for all maintainers:
Modern CI tools make it easy to ship code—but it’s just as easy to accidentally ship your keys to the kingdom. Always check what goes into your build artifacts, and keep secrets out of your source archives!
Timeline
Published on: 04/18/2025 21:15:44 UTC
Last modified on: 04/21/2025 14:23:45 UTC