---
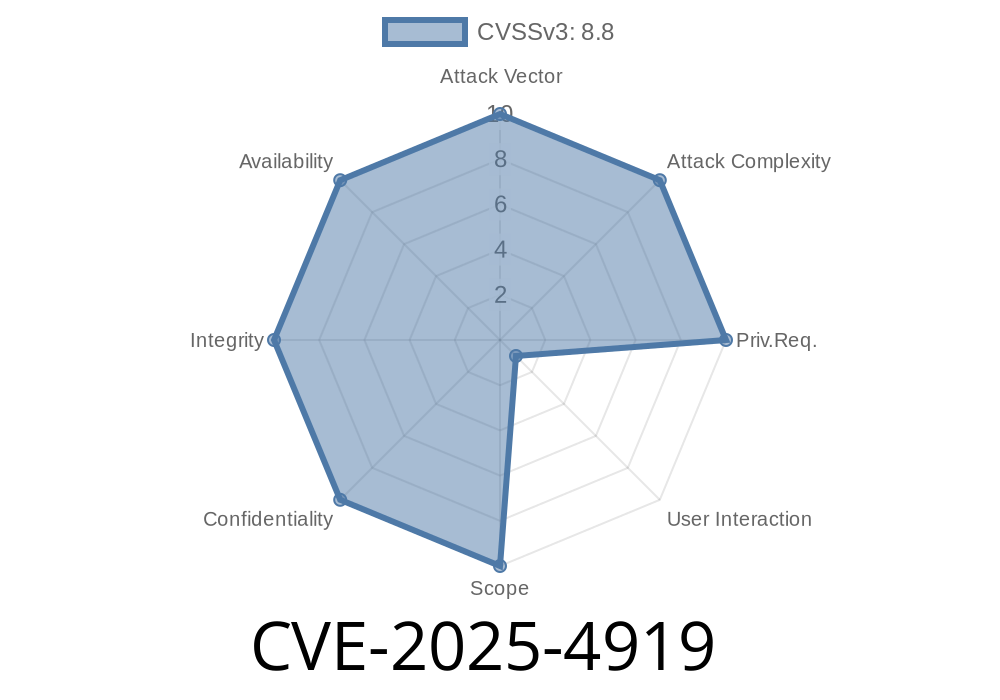
In June 2025, security researchers and Mozilla announced a high-severity vulnerability tracked as CVE-2025-4919. This flaw impacted multiple versions of Firefox and Thunderbird—including older ESR (Extended Support Release) branches—by allowing out-of-bounds read and write operations on JavaScript objects, thanks to confusion in array index handling.
Let’s break down what happened, how the bug works, and what makes it dangerous.
What Is CVE-2025-4919?
CVE-2025-4919 is a security bug affecting the JavaScript engine in Firefox and Thunderbird products. Specifically, it lets attackers misuse the way certain JavaScript arrays manage their sizes and indices. By abusing this confusion, code can trick the browser into reading or writing outside the boundaries of an array’s memory area.
How Did Attackers Exploit It?
Let’s look at a simple picture of the bug in everyday English. In JavaScript, arrays normally keep track of how many elements they have and their limits. If you try to access an index that doesn’t exist, you usually get “undefined.”
But, deep inside the browser’s C++ engine (SpiderMonkey for Firefox), there’s special handling for certain kinds of “typed arrays” or fast arrays. If a script is able to manipulate the internal index size—such as tricking the engine into thinking an array is much larger than it truly is—reads and writes can go to memory locations that shouldn’t be visible.
Example: Simplified Exploit Demo (Pseudo-JavaScript)
Here's a simplified proof of concept. Note: This code will NOT work in patched browsers or other engines, but shows the general idea.
// Pseudo-JS: Exploit the oob bug via confusing indexed properties
let arr = [1, 2, 3];
let victim = {secret: "hidden!"};
// Force arr to become a 'holey' fast array and confuse length
arr.length = xFFFFFFF; // Artificially inflate length (not normally possible)
// Now read out-of-bounds
let leaked = arr[x100000000]; // Might read memory from 'victim' object or elsewhere
console.log(leaked); // Might print a memory leak or random value
In real attacks, these tricks get much more complicated, and the malicious script engineers use a series of conversions, sparsity, and JIT optimizations to break assumptions and move from a bug to a powerful exploit.
To exploit the bug, attackers usually need
1. Heap grooming: Arrange memory in such a way that valuable objects (like function pointers or sensitive data) are next to manipulated arrays.
2. Index confusion: Trick the engine into using a wrong and too large index—perhaps by changing array type, converting between sparseness and packedness, or using proxies.
3. Arbitrary read/write: Perform out-of-bounds access.
4. Privilege escalation: Use the corrupt memory or code pointers to get code execution inside the browser.
Real-world exploits often chain this bug with a “sandbox escape” to take over the system.
Keep automatic updates ON
Mozilla’s patches address the underlying confusion, adding new checks in the array management code to block these tricks.
Reference Links
- Mozilla Security Advisories (Firefox)
- CVE Details: CVE-2025-4919
- Full Patch Diff Example (GitHub Mirror)
- General OOB Exploitation Techniques
Final Thoughts
CVE-2025-4919 is a reminder that even mature JavaScript engines are vulnerable if boundaries are not checked rigorously. Modern browsers are huge, complex programs, so always keep them updated. If you’re a developer, never assume user input or script code is harmless—even inside the supposed safety of the browser.
Stay updated. Stay safe!
If you want to learn more about browser security, check Mozilla’s advisories every month or follow your favorite browser’s official security blog.
Timeline
Published on: 05/17/2025 22:15:19 UTC
Last modified on: 05/28/2025 14:08:29 UTC