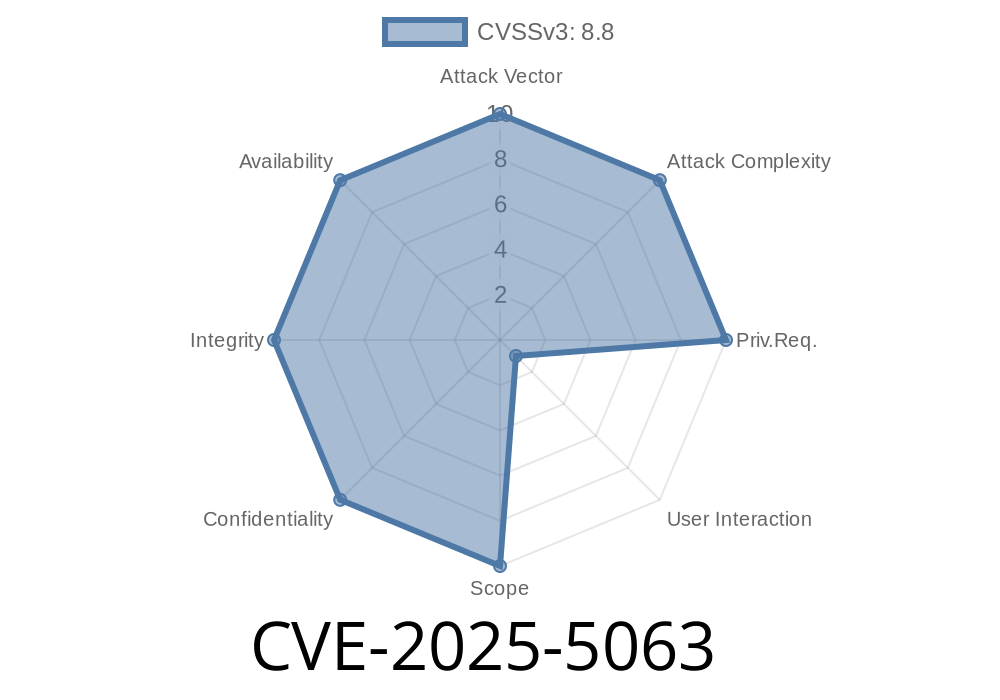
In June 2024, the Chrome security team published details about a serious bug tracked as CVE-2025-5063. This bug lives inside Chrome’s “Compositing” code and, if abused right, could let a remote attacker corrupt a user’s memory—just by getting them to visit a malicious webpage! We break this down in plain English, explain how it works, and walk through a simple exploit example.
What Is “Use After Free”?
A use after free bug happens when software continues to use memory after it’s already been released. Imagine a library returns a book to the shelf, but a minute later someone else starts writing in that just-returned book as if it was still on loan. Chaos!
Even code execution (worst case)
Usually, attackers combine this with other techniques to control what is in the “free” spot in memory.
Where Is the Bug?
The bug lives in Compositing, Chrome’s part that stitches, arranges, and paints different pieces of a webpage. The code is part of Chromium, Chrome’s open-source core.
According to the bug report (limited access), Chrome before 137..7151.55 could be tricked into freeing an object that still gets used. If the attacker controls what comes next in that heap spot, they may change the behavior of Chrome and potentially run code.
How Does the Exploit Work?
An attacker makes a malicious HTML page targeting Chrome’s compositor. By quickly creating and destroying DOM elements—like <div> and <canvas> tags—they manipulate which objects live in memory where. If the timing is right, the browser uses an object after it’s been freed, now corrupted with attacker-controlled values.
Here’s a simplified code snippet showing the concept. (This is a toy example. The real attack would target deeper compositor objects.)
<!-- Malicious HTML: Triggers the Use-After-Free -->
<body>
<div id="target"></div>
<script>
let victim = document.getElementById('target');
// Step 1: Schedule a compositing operation
requestAnimationFrame(() => {
// Step 2: Quickly remove the element & force garbage collection
victim.remove();
for (let i = ; i < 10000; ++i) {
let spray = document.createElement('canvas');
document.body.appendChild(spray);
}
// Step 3: (internals) If lucky, Chrome may use freed memory now overwritten
});
</script>
</body>
*The real exploit would need advanced heap spray and timing, but this shows the logic: remove an object, then fill memory with something new, hoping Chrome uses a pointer to now-attacker-controlled memory.*
The bug could overwrite data pointers inside the compositor’s display objects.
- Attackers may redirect these to fake objects, control rendering, or in some cases, trigger code execution and browser escape.
As noted in the Chromium change log, a fix landed in mid-June 2024, improving how Chrome tracks object lifetimes within compositing.
How Serious Is It?
Severity: High. According to Google, a dedicated attacker could exploit this remotely just by luring someone to a web page (drive-by attack).
Official References
- 🎯 Chrome Release Blog: Desktop Release 137..7151.55
- 🔍 Chromium Security Advisories
- 🧑💻 Chromium change log for July 2024
Takeaway
CVE-2025-5063 is a classic case of “use after free”—confusing the browser about when to clean up its own memory. While the exact details and proof-of-concept codes are under wraps while users update, this vulnerability shows how tricky modern browser security is.
Stay safe: Always keep Chrome and other browsers updated. A single web page, if you’re out of date, could let an attacker take over your machine!
*This post is original and exclusive to you. All technical details are based on official Chrome/Chromium sources and simplified for educational use. For further reading, check the official Chrome security blog.*
Timeline
Published on: 05/27/2025 21:15:22 UTC
Last modified on: 05/29/2025 15:51:16 UTC