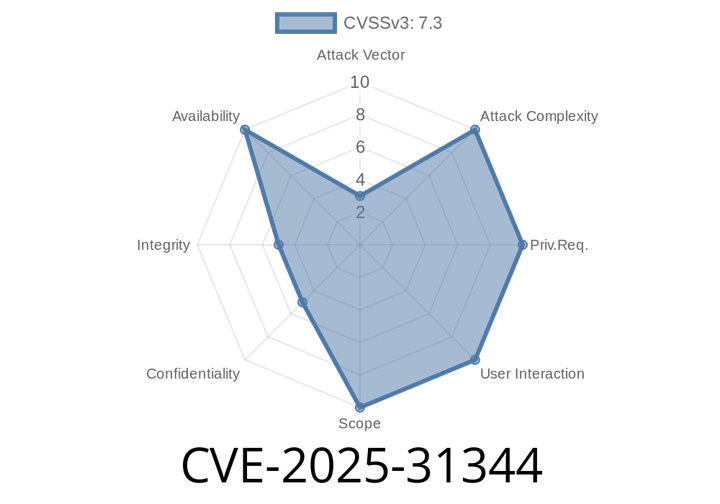
CVE-2025-31344 - Heap-based Buffer Overflow in openEuler giflib's gif2rgb.C (through 5.2.2) Explained
In early 2025, a new vulnerability shocked parts of the open-source world: CVE-2025-31344, a heap-based buffer overflow in the giflib library used by many Linux
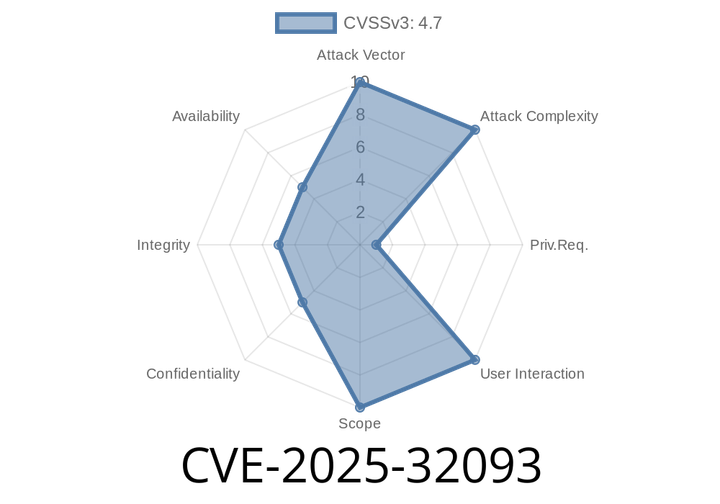
CVE-2025-32093 - Mattermost Improper Permission Validation Lets Non-Admins Modify System Administrators (With Exploit Details)
On June 2024, the security community identified a critical vulnerability in Mattermost, the popular open-source messaging platform designed for teams and enterprises. Tracked as CVE-2025-32093,
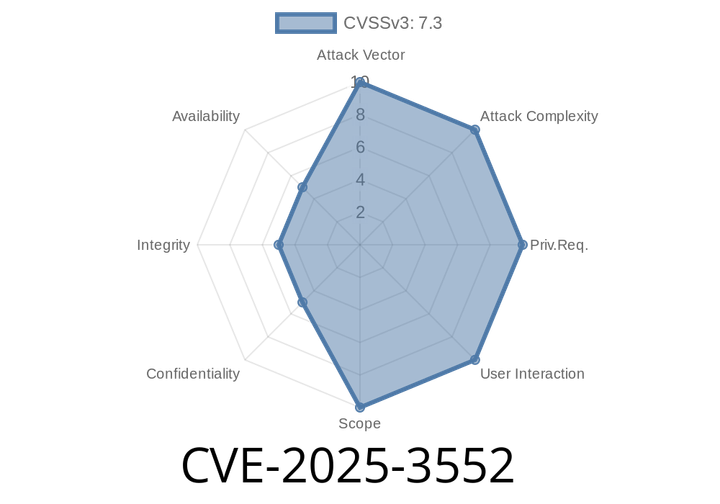
CVE-2025-3552 - Unrestricted File Upload in Lingxing ERP 2 (Exploit and Analysis)
A new critical vulnerability—CVE-2025-3552—has been discovered in the popular business management software, Lingxing ERP 2. This flaw, present in the /Api/TinyMce/UploadAjax.
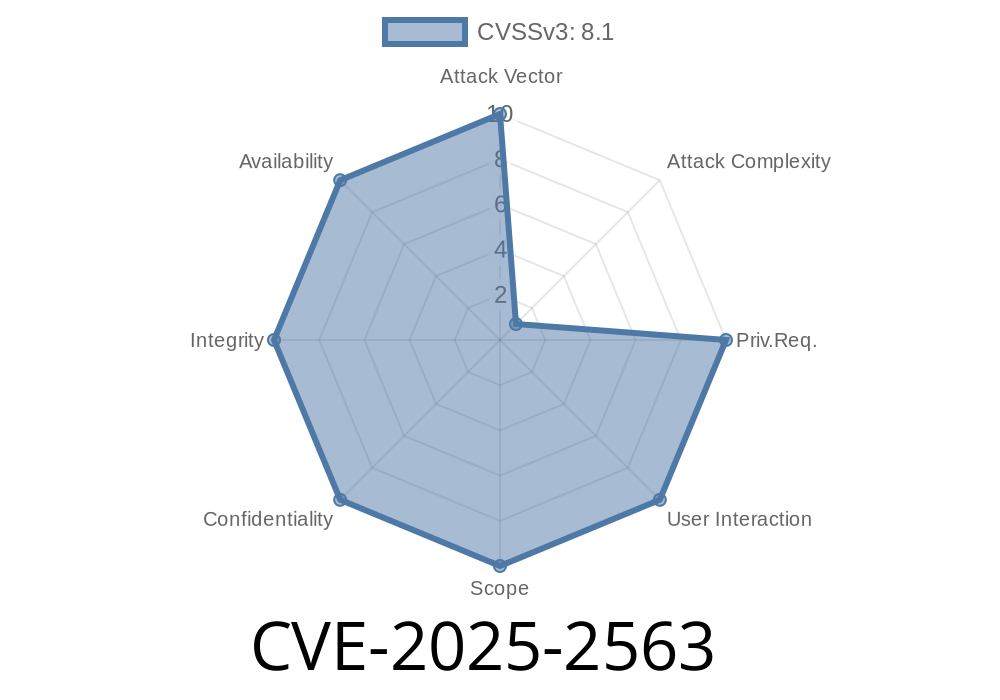
CVE-2025-2563 - How a Hidden Flaw in the “User Registration & Membership” WordPress Plugin Lets Hackers Become Admins
Published: June 2024 <br>Author: [Your Name]
A newly discovered vulnerability, CVE-2025-2563, shakes up the world of WordPress website administration. This security flaw
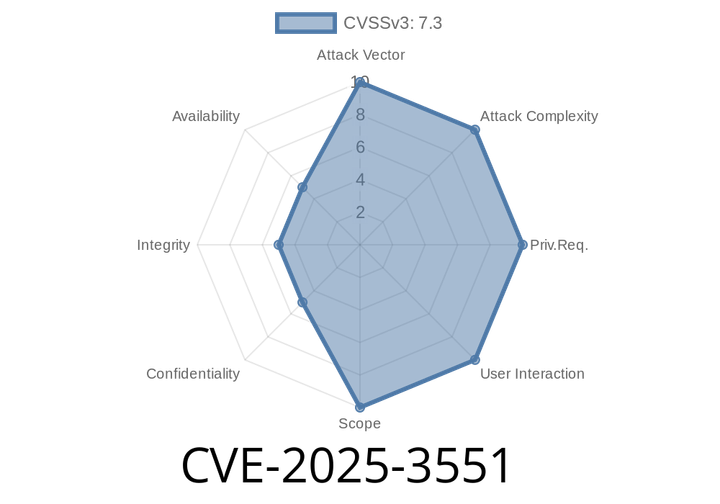
CVE-2025-3551 - Critical Unrestricted File Upload in Lingxing ERP 2 – Exploit Insights and What You Need to Know
In the fast-moving world of business ERP systems, vulnerability exposures can mean disaster for organizations. Recently, a new vulnerability—CVE-2025-3551—has drawn attention for potentially
Episode
00:00:00
00:00:00