CVE-2024-9633 - GitLab Group Name Domain Confusion Attack Detailed
A recently disclosed security vulnerability—CVE-2024-9633—affects multiple versions of GitLab Community Edition (CE) and Enterprise Edition (EE). This flaw could let an attacker confuse
CVE-2022-31670 - Breaking Harbor’s Boundaries with Tag Retention Policy Escalation
When we protect our container images, tools like Harbor are critical in keeping our images organized, up-to-date, and safe from accidental deletion. Harbor lets teams
CVE-2022-31671 - How Harbor’s Weak Log Permissions Expose Your Job Logs
In today’s world, container registries like VMware Harbor are the backbone of cloud-native development. Harbor is valued for its security features, but even the
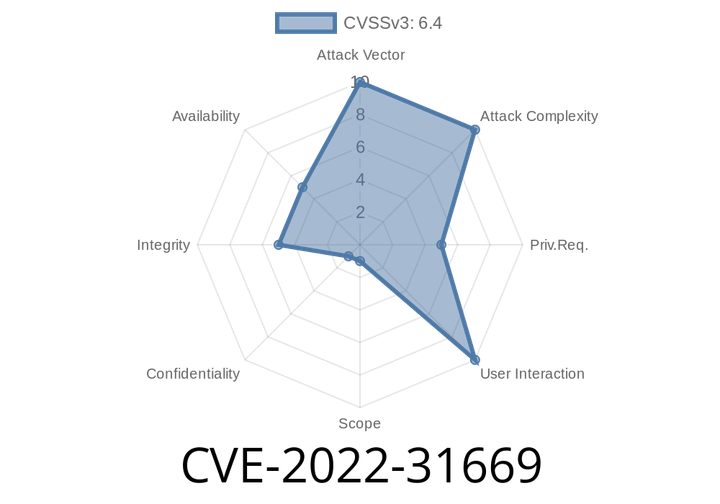
CVE-2022-31669 - How Harbor’s Tag Immutability Policy Update Bug Can Let Attackers Alter Other Projects
When it comes to securing container images, Harbor is an open-source registry many organizations depend on for its advanced features, including tag immutability policies—rules
CVE-2022-31667 - How to Exploit Harbor's Robot Account Permission Bypass
> Exclusive Long Read: Understand and Exploit a Subtle but Serious Harbor Security Bug
What is Harbor?
Harbor is an open-source registry for storing, signing,
Episode
00:00:00
00:00:00