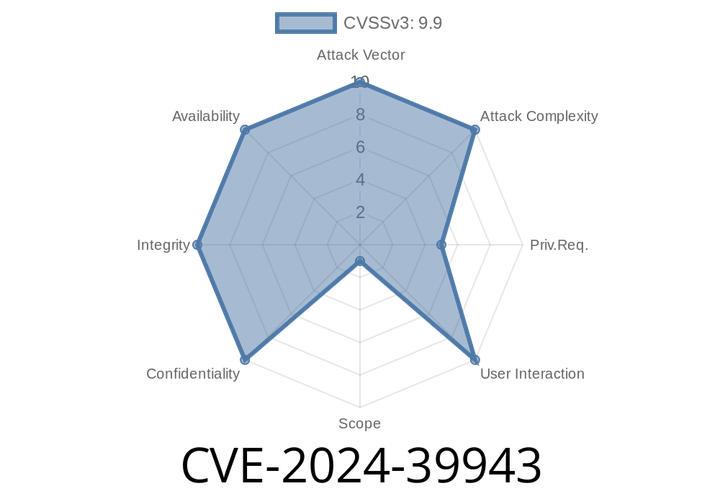
CVE-2024-39943 - Remote Command Execution Vulnerability in rejetto HFS 3 (HTTP File Server) Before .52.10 on Linux, UNIX, and macOS
A recent vulnerability, CVE-2024-39943, has been discovered in rejetto HFS 3 (HTTP File Server version 3) affecting Linux, UNIX, and macOS systems. The issue allows
CVE-2024-39884 - Source Code Disclosure in Apache HTTP Server 2.4.60 Explained
On June 18, 2024, a critical security flaw surfaced in Apache HTTP Server 2.4.60, cataloged as CVE-2024-39884. This vulnerability is especially dangerous to
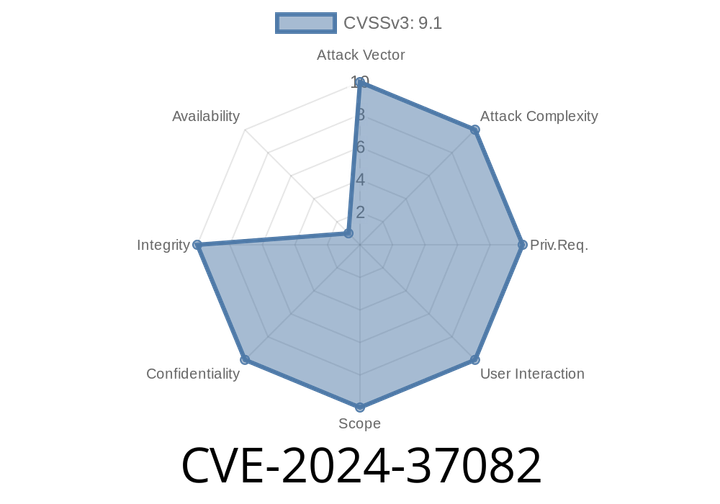
CVE-2024-37082 - How Custom HAProxy Config Can Let Attackers Bypass mTLS in Cloud Foundry – Analysis, PoC, and Fix
In 2024, a tricky vulnerability (now logged as CVE-2024-37082) was discovered in deployments of Cloud Foundry using the haproxy-boshrelease. This security issue isn’t just
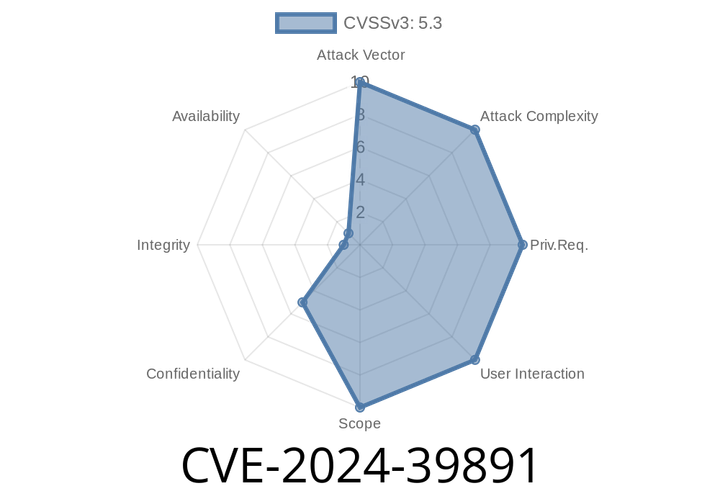
CVE-2024-39891 - Exposed Authy Phone Number Lookup — How Twilio’s API Leaked User Data
In June 2024, security researchers spotted a worrying flaw in the Twilio Authy API—used by millions for secure two-factor authentication. This vulnerability, logged as
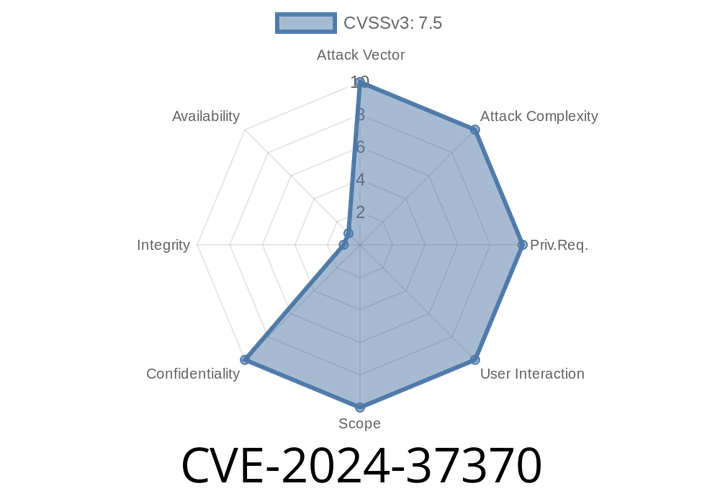
CVE-2024-37370 - How Attackers Trick Applications with Modified Kerberos GSS krb5 Wrap Tokens
June 2024 brought an important security update for MIT Kerberos 5 (krb5), fixing a subtle but serious flaw tracked as CVE-2024-37370. In this article, we’
Episode
00:00:00
00:00:00