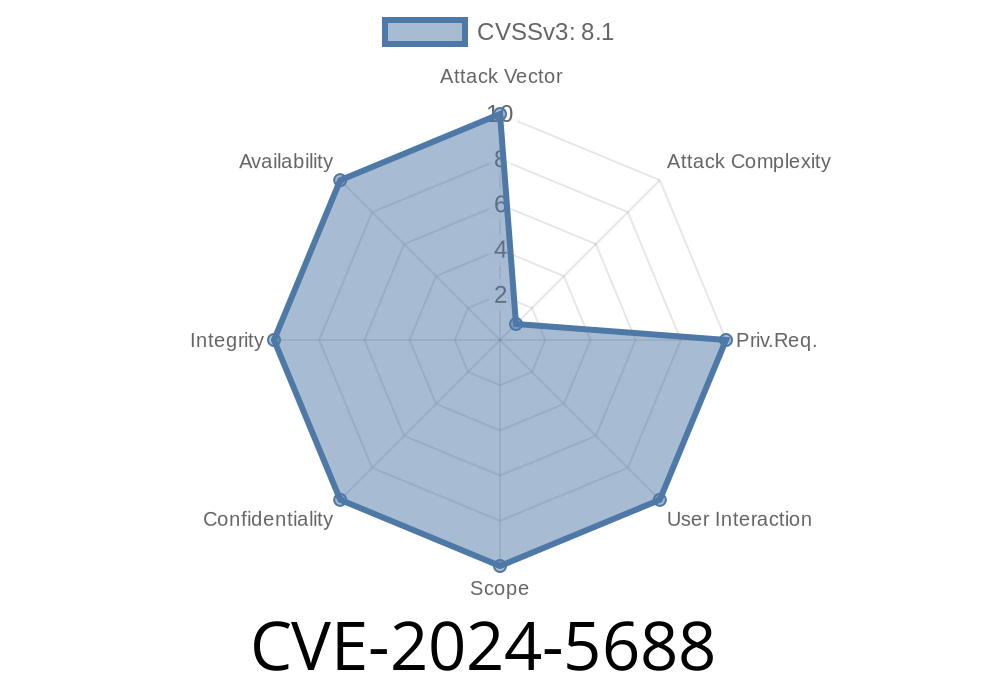
CVE-2024-5688 - Firefox Use-After-Free Exploit in Object Transplant (`Firefox < 127`, ESR < 115.12, Thunderbird < 115.12)
The cybersecurity world is buzzing over CVE-2024-5688, a critical vulnerability discovered in Firefox and Mozilla products. This flaw revolves around a subtle, yet dangerous, use-after-free
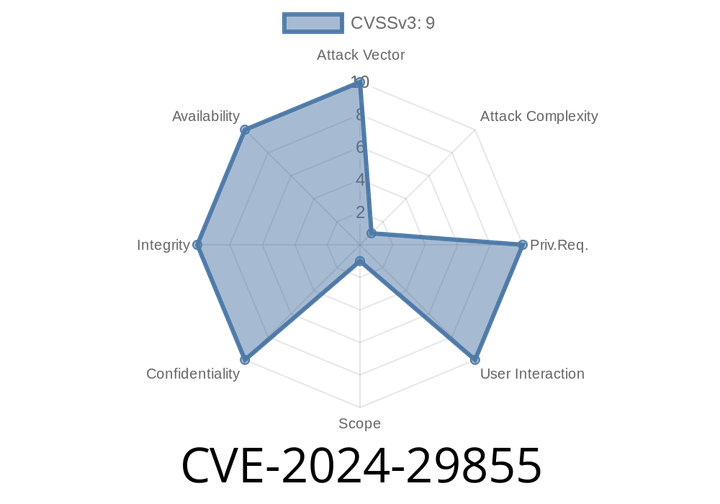
CVE-2024-29855 - Hard-coded JWT Secret Opens Door to Authentication Bypass in Veeam Recovery Orchestrator
CVE-ID: CVE-2024-29855
Product: Veeam Recovery Orchestrator (VRO)
Vulnerability: Hard-coded JWT secret leads to authentication bypass
Severity: Critical
Veeam Recovery Orchestrator is a powerful tool in
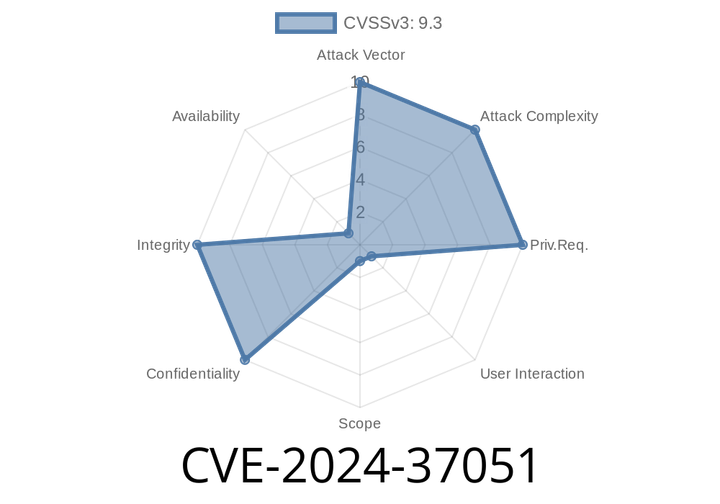
CVE-2024-37051 - GitHub Access Token Exposure in JetBrains IDEs – What Happened, How to Exploit, and How to Fix
---
References and Further Reading
10. Conclusion
1. Introduction
JetBrains IDEs like IntelliJ IDEA, PyCharm, and WebStorm are used by millions of developers worldwide. These
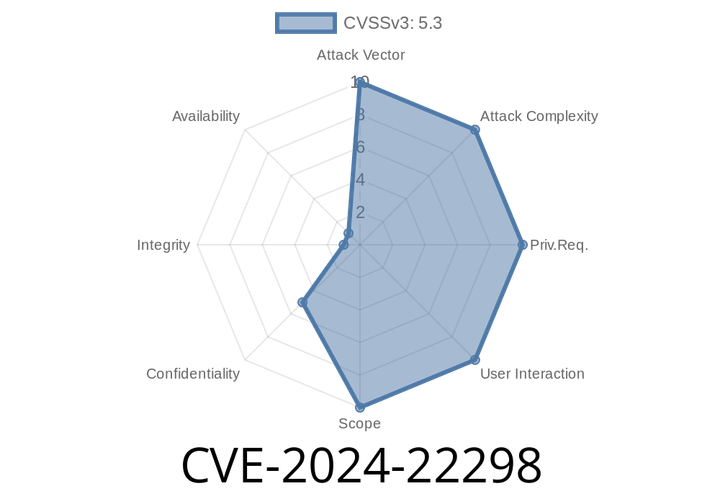
CVE-2024-22298 - Missing Authorization in TMS Amelia Bookings Plugin Can Lead to Unauthorized Access — Detailed Breakdown
In June 2024, CVE-2024-22298 was assigned to a critical security flaw found in the widely-used TMS Amelia WordPress plugin (also known as ameliabooking). This vulnerability
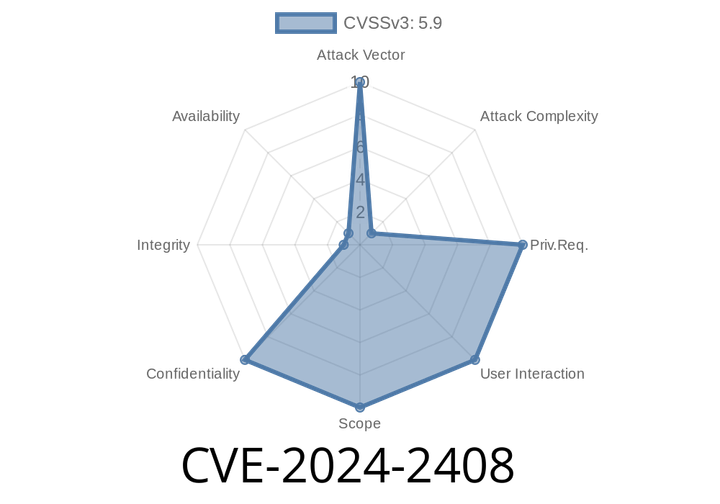
CVE-2024-2408 - PHP's openssl_private_decrypt and the Hidden Risk Behind the Marvin Attack
A new vulnerability tracked as CVE-2024-2408 has come to light, affecting the way PHP handles decryption using its openssl_private_decrypt() function with PKCS1 padding
Episode
00:00:00
00:00:00