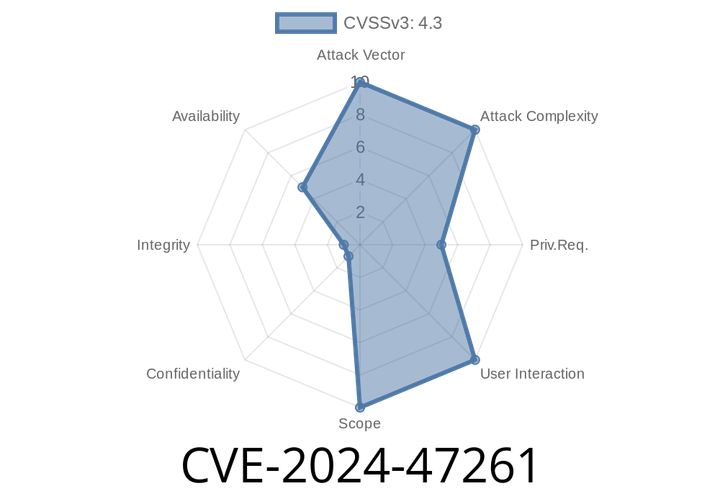
CVE-2024-47261 - How 51l3nc3 Exposed Axis Camera Overlay Upload Vulnerability
On May 2024, a security researcher known as 51l3nc3, actively participating in the AXIS OS Bug Bounty Program, uncovered a critical flaw in Axis network
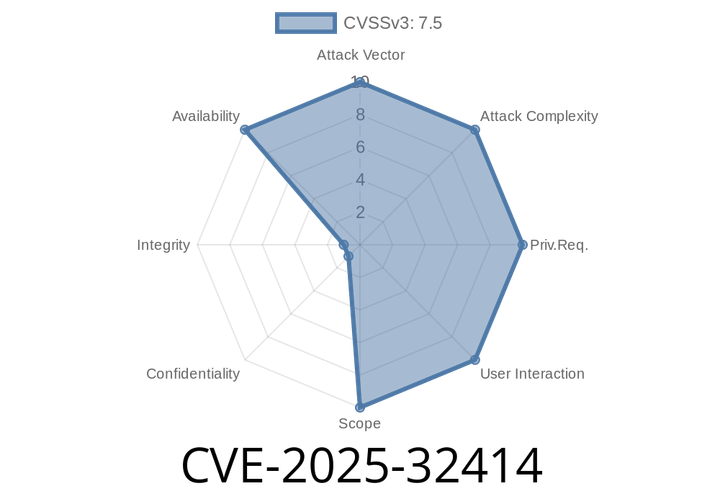
CVE-2025-32414 - Out-of-Bounds Memory Access in libxml2 Python Bindings Explained
CVE-2025-32414 is an out-of-bounds memory access bug in libxml2’s Python API. It happens in versions before 2.13.8 and 2.14.x before
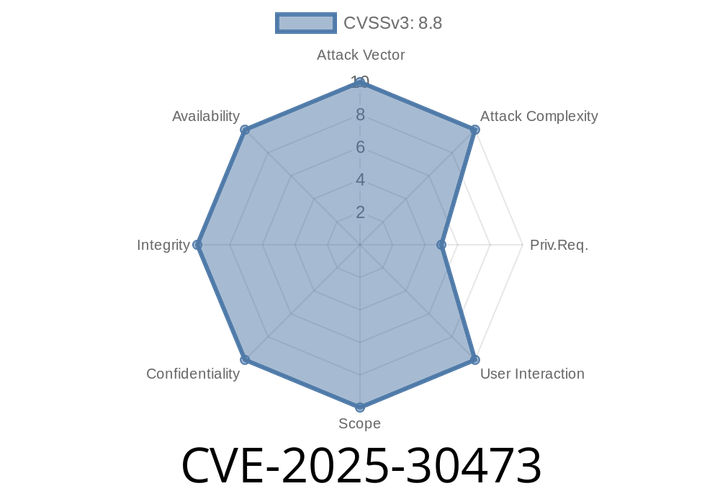
CVE-2025-30473 - SQL Injection Flaw in Apache Airflow Common SQL Provider Can Lead to Privilege Escalation
A new security vulnerability, CVE-2025-30473, was discovered in the Apache Airflow Common SQL Provider (versions before 1.24.1). This flaw allows authenticated users to
CVE-2024-11859 - DLL Search Order Hijacking Can Lead to Malicious Code Execution by Administrators
In early 2024, security researchers discovered CVE-2024-11859, a vulnerability tied to how certain applications in Windows search and load dynamic-link libraries (DLLs). This issue—commonly
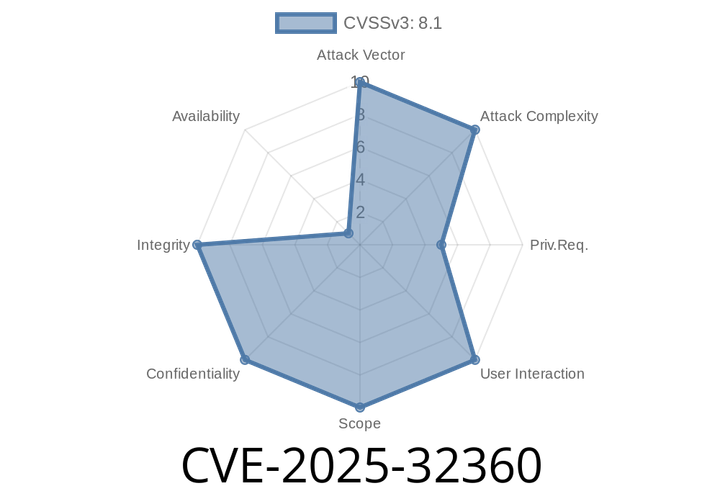
CVE-2025-32360 - Information Exposure and Draft Manipulation in Zammad 6.4.x
*Published: June 2024*
Recently, a critical security vulnerability—CVE-2025-32360—was found in Zammad, the popular open-source support and ticketing system. This post breaks down how
Episode
00:00:00
00:00:00