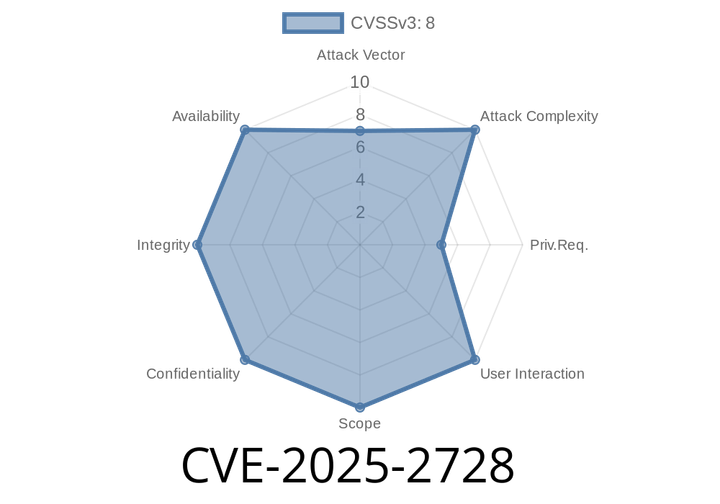
CVE-2025-2728 - Critical Command Injection in H3C Magic NX30 Pro and NX400 Routers (Up to V100R014)
Recently, a critical vulnerability, tracked as CVE-2025-2728, was discovered in H3C Magic NX30 Pro and Magic NX400 router models running firmware versions up to V100R014.
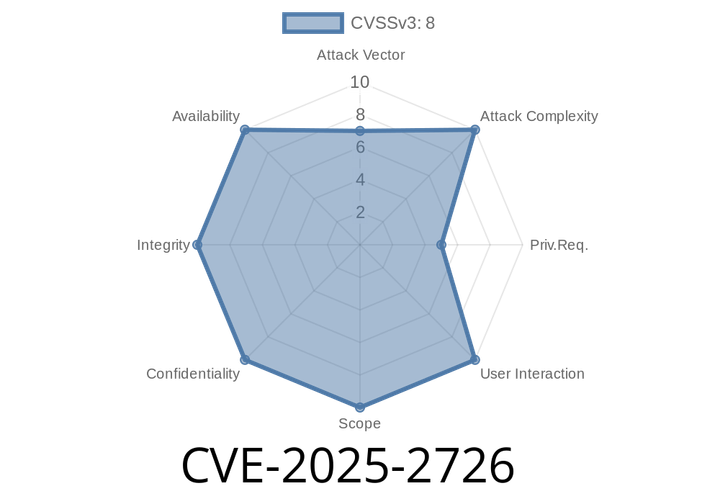
CVE-2025-2726 - Critical Command Injection in H3C Magic Routers – Full Breakdown, Exploit, and Recommendations
---
Overview
A newly discovered vulnerability, CVE-2025-2726, affects several popular H3C Magic router models, including Magic NX15, Magic NX30 Pro, Magic NX400, Magic R301, and
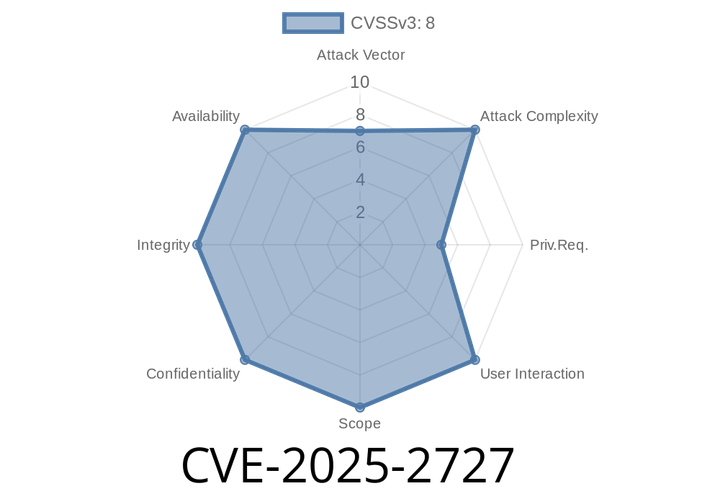
CVE-2025-2727 - Critical Command Injection Vulnerability in H3C Magic NX30 Pro Router Explained (with Exploit Details)
A new, critical security issue has been discovered in H3C Magic NX30 Pro routers up to version V100R007. Known as CVE-2025-2727, this vulnerability exposes your
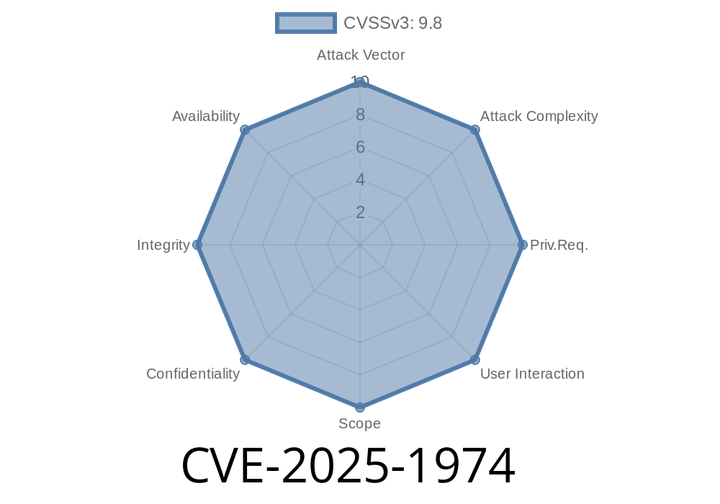
CVE-2025-1974 - How Ingress-NGINX in Kubernetes Can Expose Your Secrets (And How Attackers Can Exploit It)
In mid-2025, a serious security vulnerability was found in Kubernetes, tracked as CVE-2025-1974. If you’re using the popular Kubernetes ingress-nginx controller, your cluster could
CVE-2025-26512 - SnapCenter Privilege Escalation Vulnerability Explained & Exploited
NetApp’s SnapCenter is a popular backup and management tool used by enterprises worldwide to safeguard applications, databases, and files. But in early 2025, cybersecurity
Episode
00:00:00
00:00:00