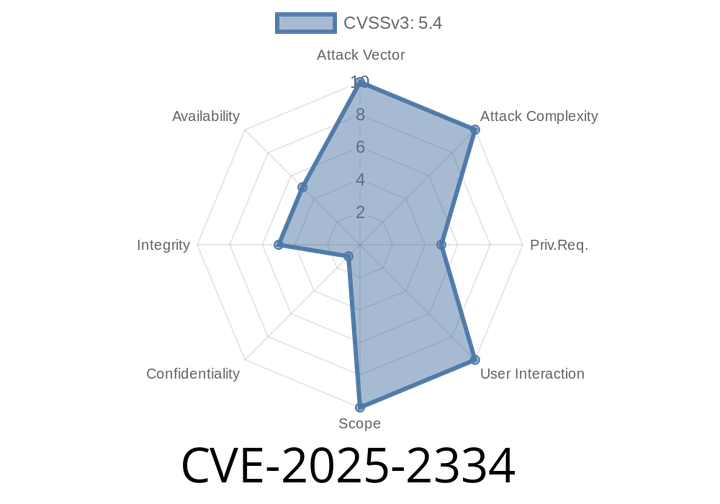
CVE-2025-2334 - Insecure Access Control in SpringBoot OpenAI ChatGPT Lets Attackers Delete Any User’s Chat History
In early 2025, a problematic vulnerability — CVE-2025-2334 — was disclosed affecting the popular springboot-openai-chatgpt (e84f6f5). This issue exposes users to risk by allowing unauthorized deletion of
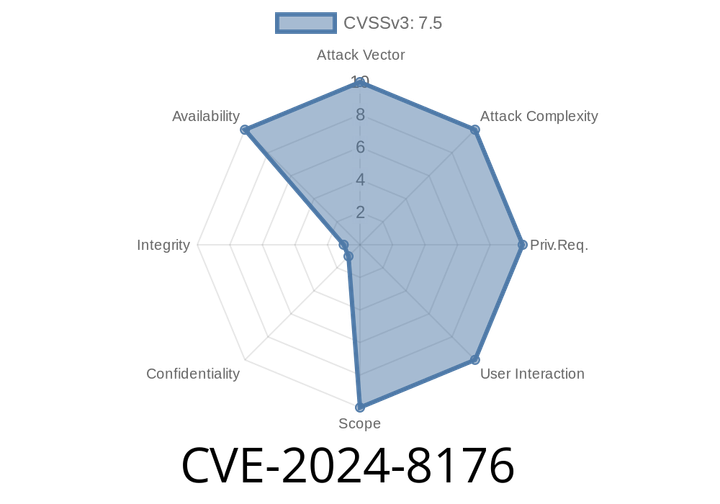
CVE-2024-8176 - Stack Overflow in libexpat via Recursive Entity Expansion — A Deep Dive
In June 2024, security researchers uncovered a critical vulnerability in the popular XML parsing library libexpat. Tracked as CVE-2024-8176, this flaw exposes applications to stack
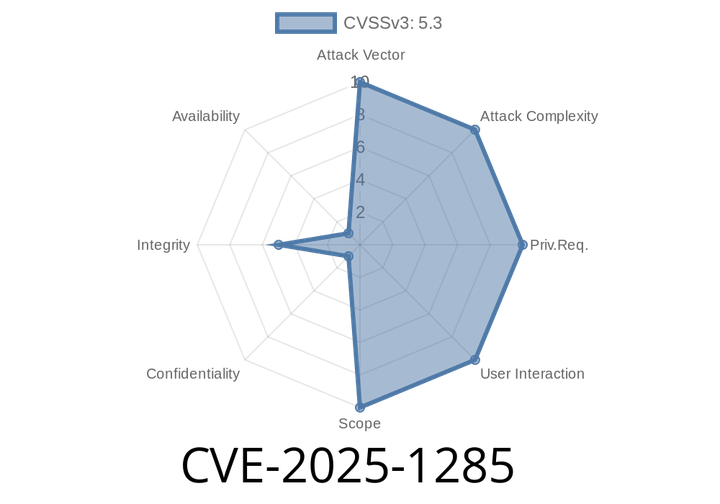
CVE-2025-1285 - How Unauthorized Attackers Can Hijack Resido Real Estate WordPress Sites
In early 2025, a high-risk security flaw was uncovered in the popular Resido - Real Estate WordPress Theme. This vulnerability, tracked as CVE-2025-1285, allows anyone—
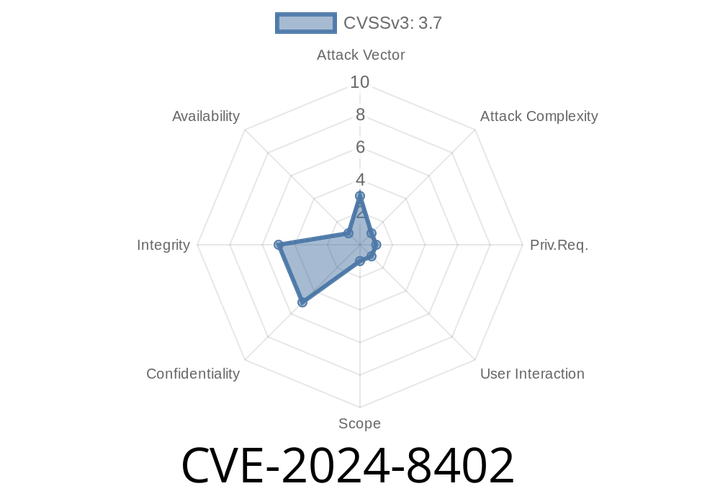
CVE-2024-8402 - Exploiting Google Cloud IAM Integration in GitLab EE – Exploit Analysis, Code Sample, and Mitigation
CVE-2024-8402 is a security vulnerability found in GitLab Enterprise Edition (EE) impacting the Google Cloud IAM integration feature. This flaw affects:
All versions from 17.
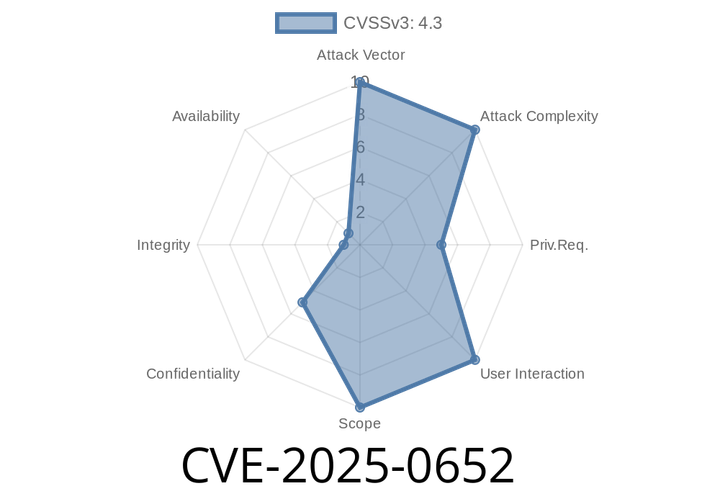
CVE-2025-0652 - Confidential Information Exposure Vulnerability in GitLab EE/CE (Exclusive Analysis, Exploit Details & Mitigation)
---
Introduction
A serious security issue, tracked as CVE-2025-0652, has been found in GitLab EE/CE. This vulnerability exposes confidential internal data to unauthorized users.
Episode
00:00:00
00:00:00