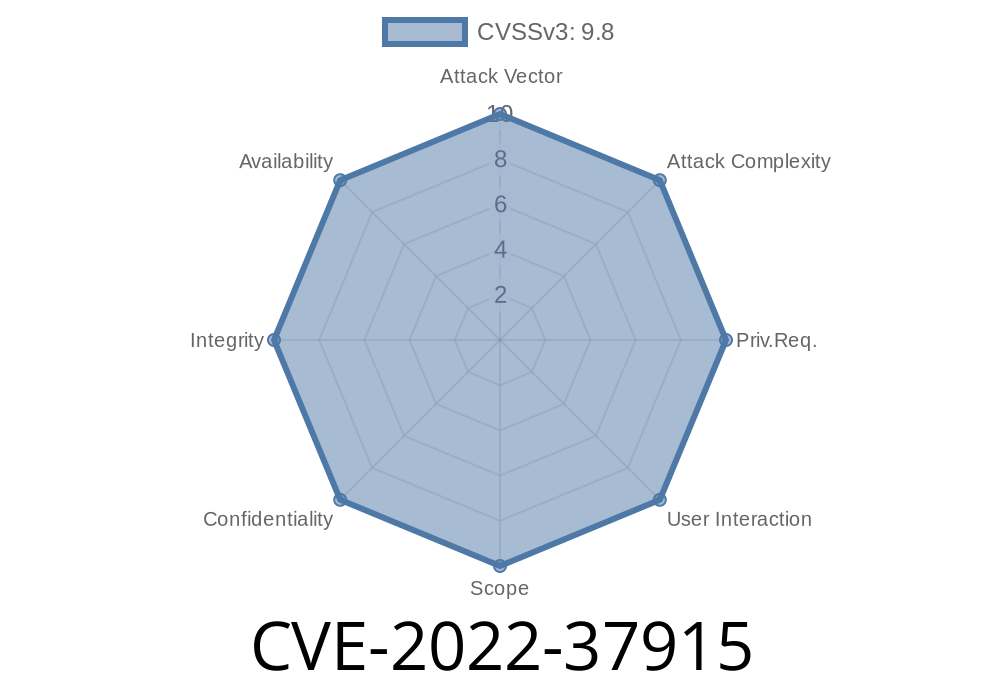
CVE-2022-37915 - Critical RCE in Aruba EdgeConnect Enterprise Orchestrator—How an Attacker Can Totally Take Over Your Network
In the ever-growing threat landscape, network management interfaces are prime targets for attackers. If you run Aruba EdgeConnect Enterprise Orchestrator, especially a fresh 9.1.
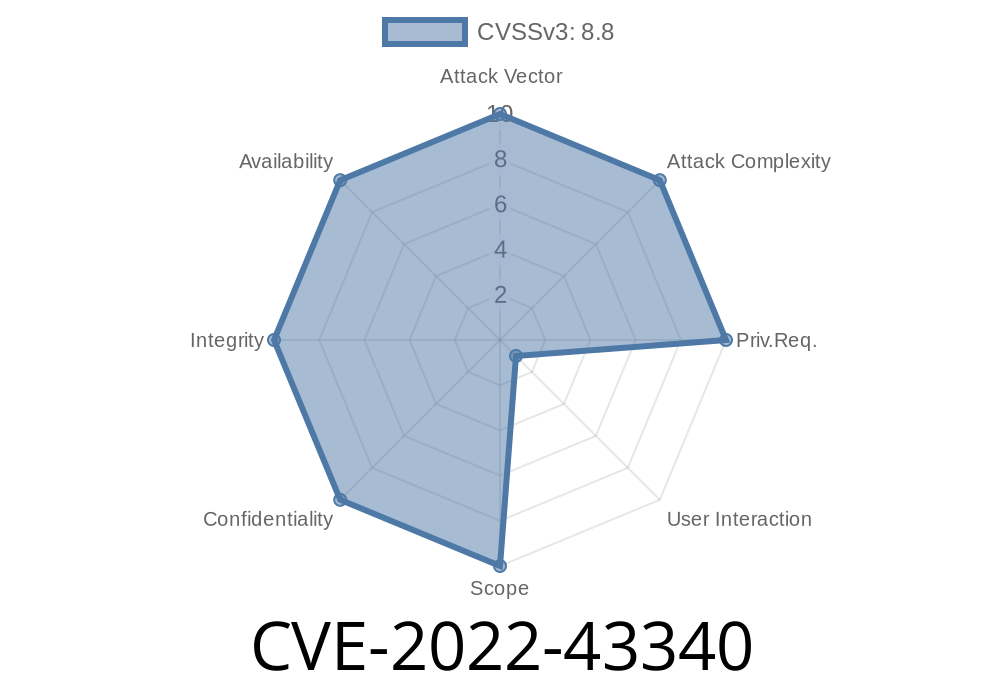
CVE-2022-43340 - Exploiting CSRF in Dzzoffice 2.02.1_SC_UTF8 to Gain Admin Control
---
Introduction
In late 2022, a critical security flaw was discovered in Dzzoffice version 2.02.1_SC_UTF8. Tracked as CVE-2022-43340, this bug allows
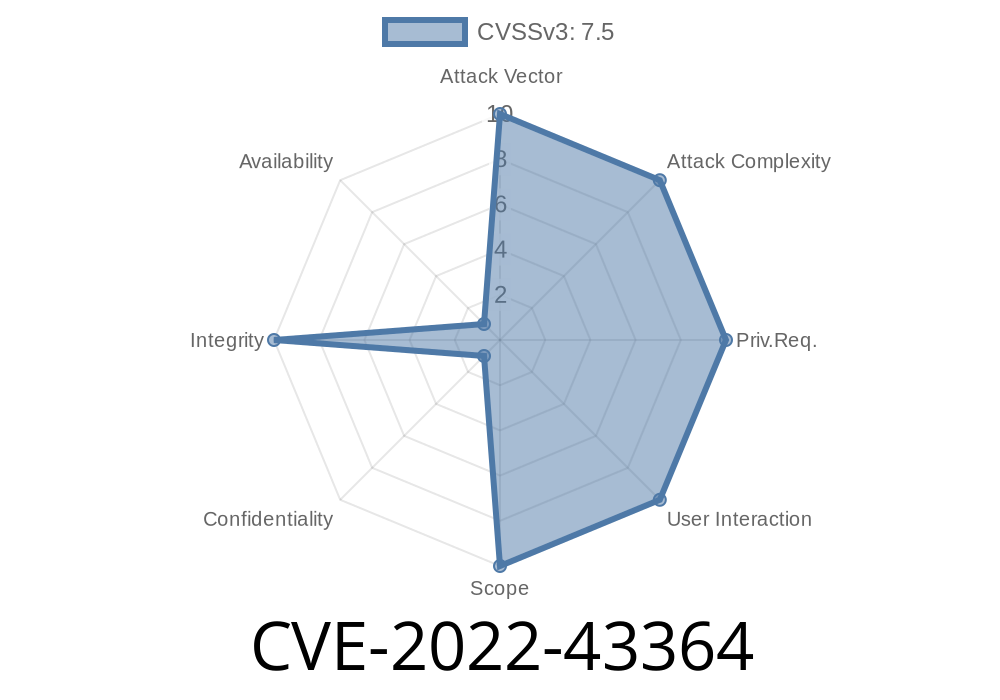
CVE-2022-43364 - How a Simple Flaw in IP-COM EW9 Let Anyone Reset the Admin Password
---
Introduction
In 2022, a critical vulnerability was found in the wireless controller IP-COM EW9, specifically in firmware version V15.11..14(9732). Tracked as
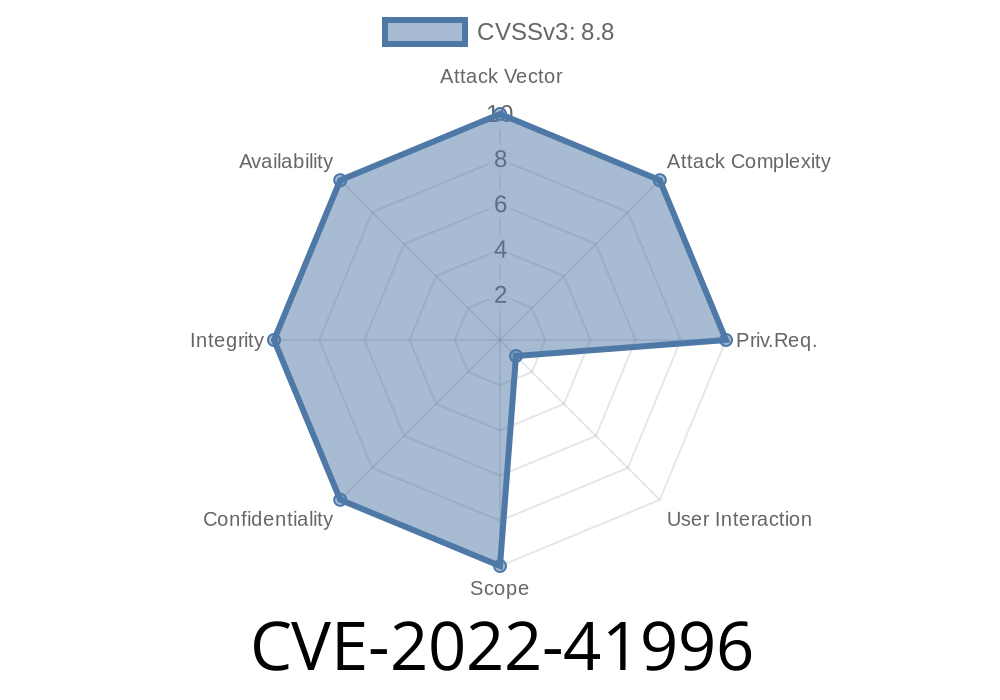
CVE-2022-41996 ThemeFusion Avada premium theme versions = 7.8.1 has a CSRF vulnerability that can be used to install arbitrary plugins.
This can result in your website being hijacked via malicious scripts or unauthorized payment/account activation. CSRF attacks can be especially dangerous on shared or
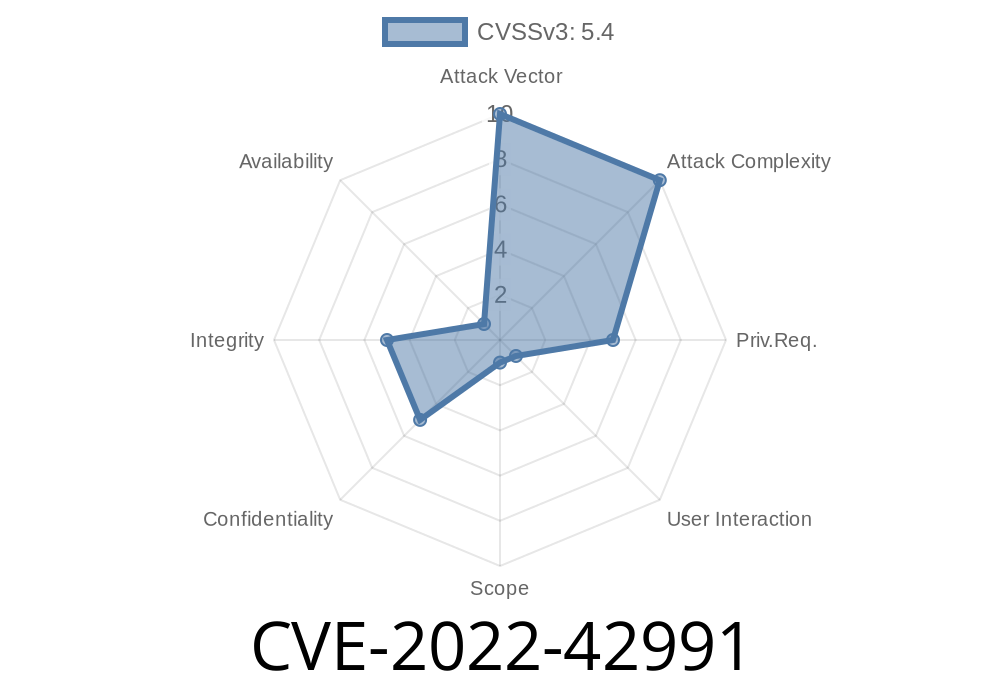
CVE-2022-42991 - Stored XSS in Simple Online Public Access Catalog v1. – Exploit, Analysis, and Protection
In this article, we'll break down CVE-2022-42991—a stored cross-site scripting (XSS) vulnerability found in Simple Online Public Access Catalog (OPAC) v1.. We&
Episode
00:00:00
00:00:00