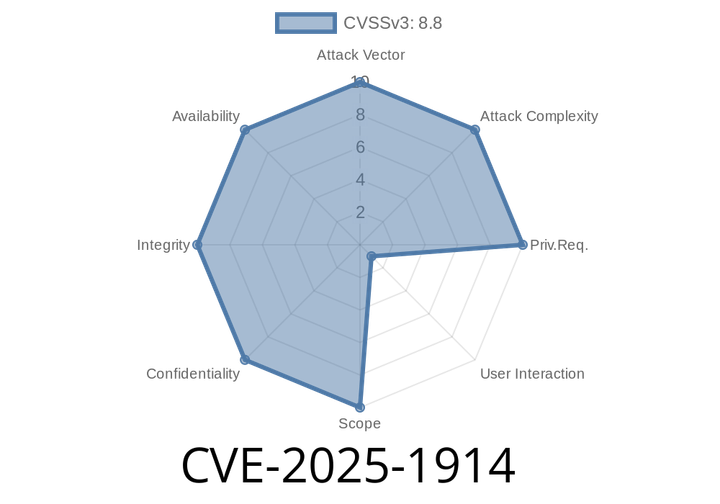
CVE-2025-1914 - Out-of-Bounds Read in Google Chrome’s V8 – How Attackers Can Exploit a Simple Crafted HTML Page
Google Chrome has long been the most popular web browser in the world, offering cutting-edge speed and security. But even Chrome isn’t immune to
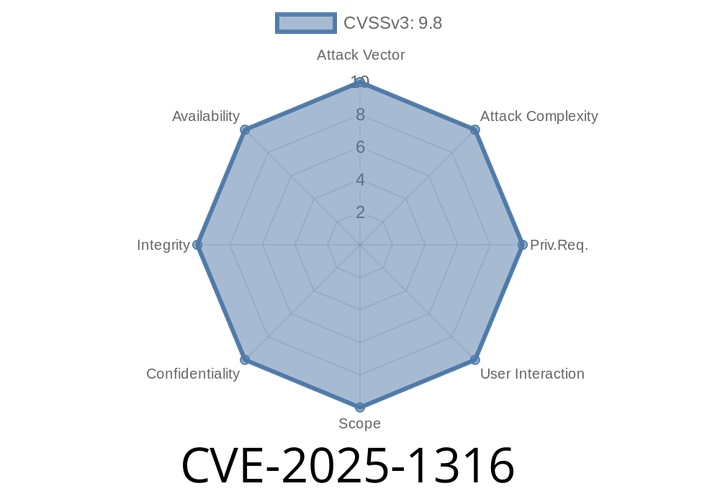
CVE-2025-1316 - Remote Code Execution in Edimax IC-710 Through Improper Input Neutralization
---
The Edimax IC-710 is a popular network camera used for security systems in homes and businesses. In early 2025, a significant vulnerability was found
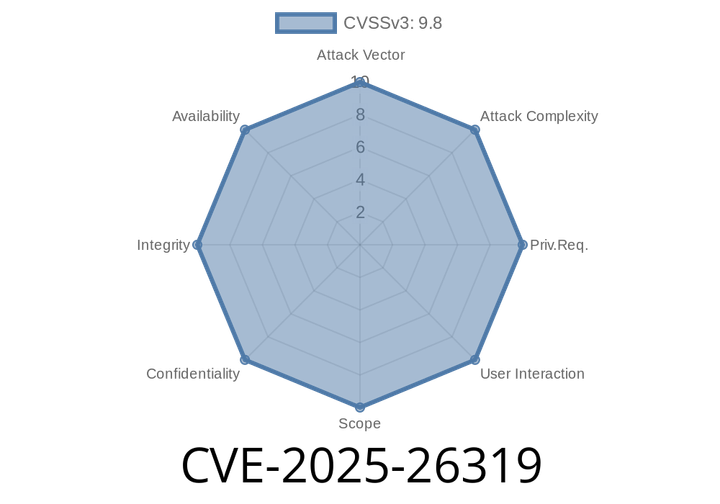
CVE-2025-26319 - Breaking Down FlowiseAI v2.2.6’s Arbitrary File Upload Vulnerability
FlowiseAI has recently been in the spotlight with the discovery of a severe vulnerability—CVE-2025-26319—affecting its v2.2.6 release. This vulnerability allows attackers
CVE-2025-1080 – Exploit in LibreOffice URI Scheme to Hijack MS SharePoint Server Integration
LibreOffice, the popular open-source office application suite, is affected by a critical security vulnerability that allows an attacker to execute arbitrary code on the victim’
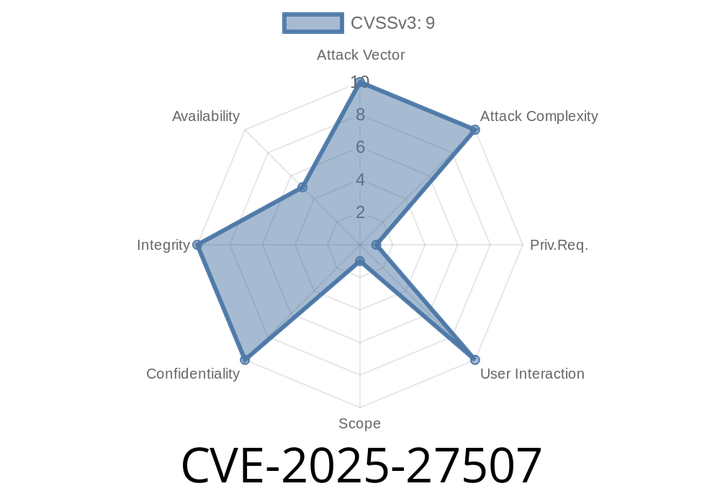
CVE-2025-27507 - Critical IDOR in ZITADEL Allows Account Takeover via LDAP Config Manipulation
ZITADEL is a widely used open-source identity and access management (IAM) solution, helping organizations manage authentication, user registration, and authorization. Designed to be flexible, secure,
Episode
00:00:00
00:00:00