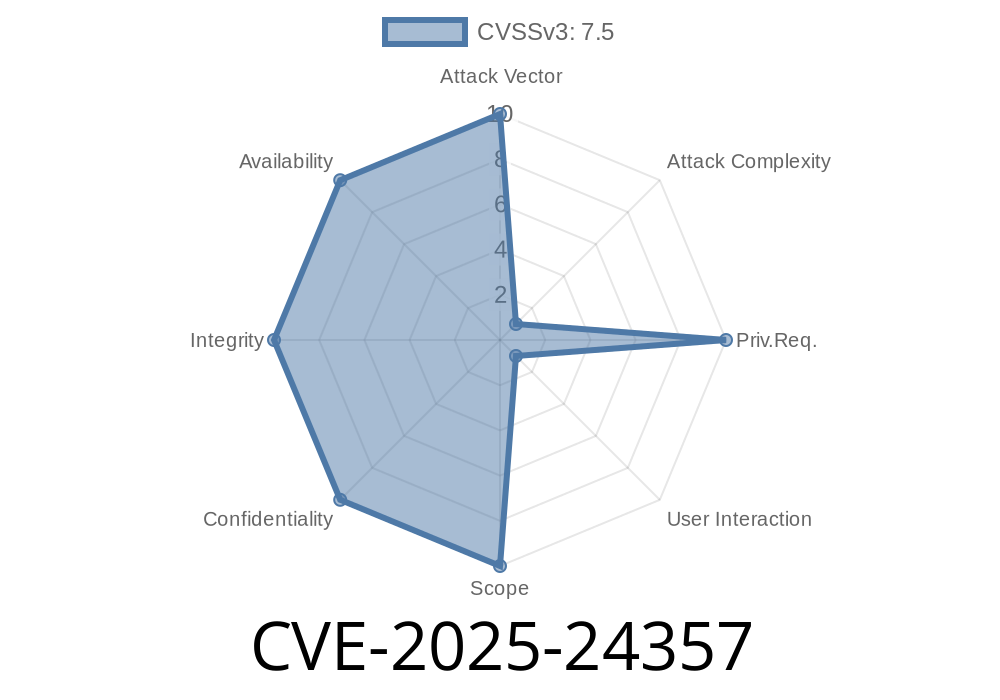
CVE-2025-24357 - RCE Vulnerability in vLLM Model Checkpoints via Unsafe torch.load Usage
CVE-2025-24357 highlights a serious remote code execution (RCE) vulnerability in the popular vLLM library, used for serving and inferencing large language models. At its core,
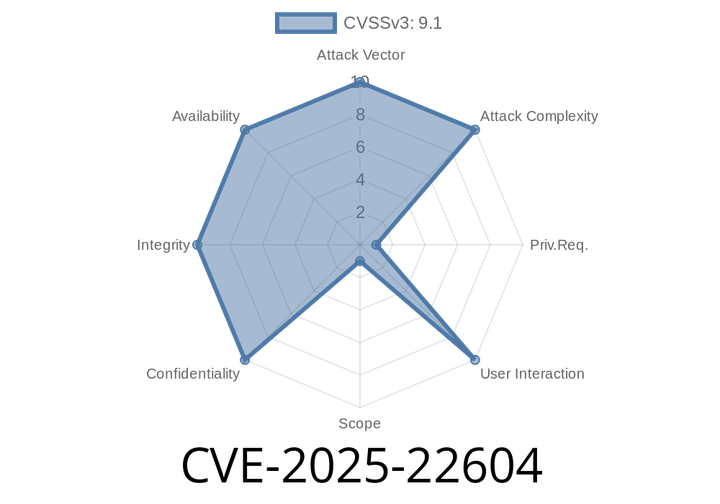
CVE-2025-22604 - Command Injection Vulnerability in Cacti SNMP Disk IO Parsing Explained
Cacti is a popular open-source network monitoring and graphing solution. On June 2025, a critical security flaw was reported that directly affects how Cacti processes
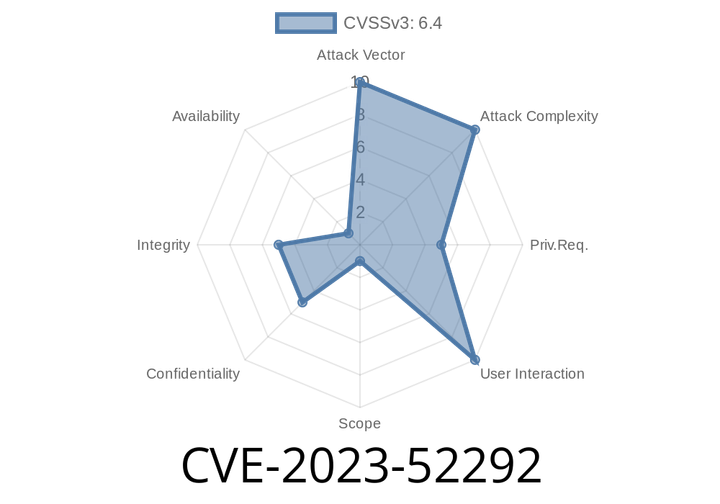
CVE-2023-52292 - Inside the IBM Sterling File Gateway XSS Vulnerability
In late 2023, a significant security problem was found in IBM Sterling File Gateway—a tool used by businesses to transfer and manage files. The
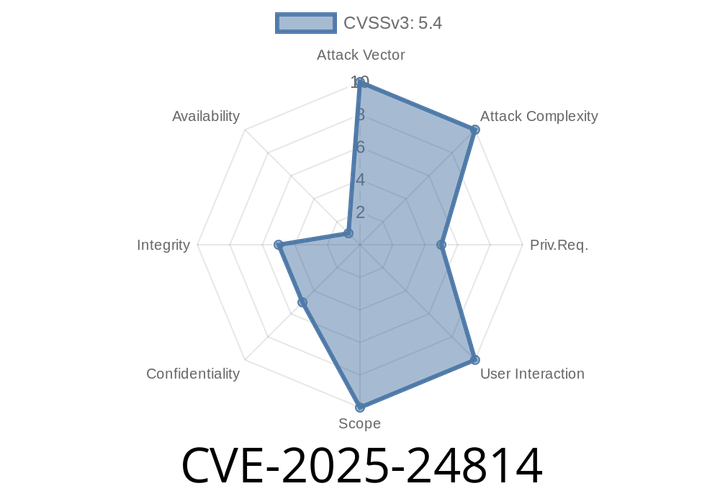
CVE-2025-24814 - Serious Misconfiguration in Apache Solr Allows Arbitrary Configset File Replacement (Privilege Escalation & RCE Explained)
CVE-2025-24814 is a critical security vulnerability in Apache Solr affecting versions up to 9.7. This flaw lets attackers replace supposedly “trusted” configuration files within
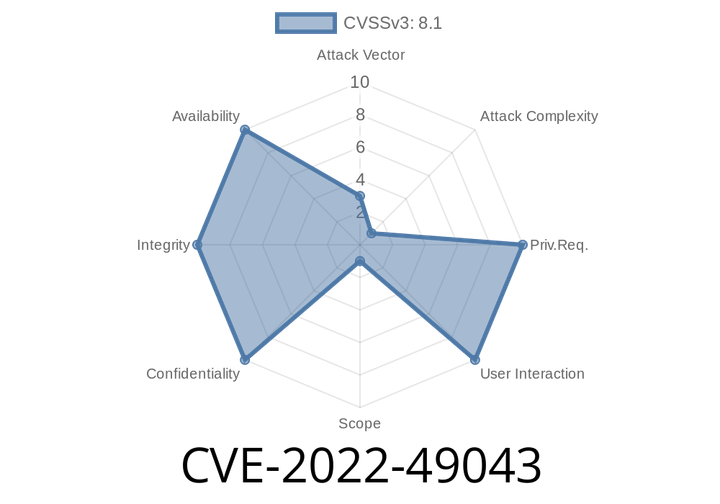
CVE-2022-49043 - Exploiting Use-After-Free in libxml2’s xmlXIncludeAddNode – Step-by-Step Guide
libxml2 is one of the most widely used XML parsing libraries on Linux and other platforms. It’s used by many popular applications, programming languages,
Episode
00:00:00
00:00:00