CVE-2025-5283 - Use-After-Free in libvpx Before Chrome 137..7151.55 — How Attackers Could Exploit It
In early 2025, security researchers discovered a serious bug tracked as CVE-2025-5283 affecting libvpx—the video codec library used by Google Chrome. This vulnerability occurs
CVE-2025-5281 - Exploiting BFCache in Google Chrome to Leak User Information
A critical new browser bug, identified as CVE-2025-5281, has caught the cybersecurity community’s attention. This flaw, found in the careful workings of the Back/
CVE-2025-5063 - How a “Use After Free” in Chrome’s Compositing Engine Let Hackers Corrupt Heap Memory
In June 2024, the Chrome security team published details about a serious bug tracked as CVE-2025-5063. This bug lives inside Chrome’s “Compositing” code and,
CVE-2025-5067 - UI Spoofing Vulnerability in Chrome’s Tab Strip Explained
Google Chrome is one of the most popular web browsers, but even giants have weak spots. In this post, we’ll break down CVE-2025-5067, a
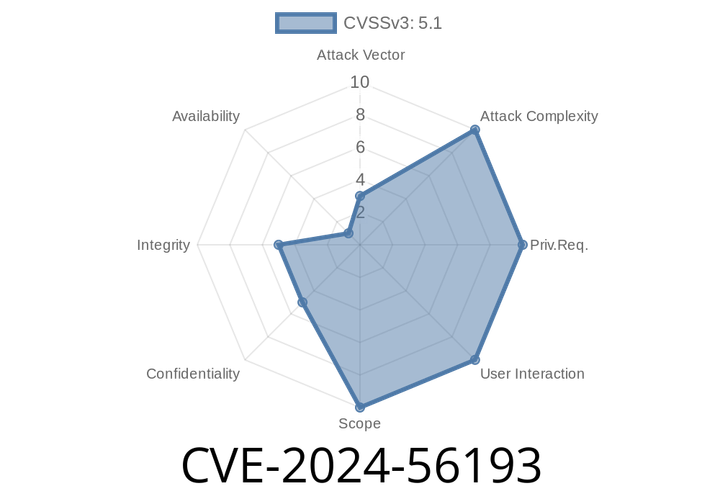
CVE-2024-56193 - Bluetooth Adapter Info Leak via Permissions Bypass
CVE-2024-56193 is a newly disclosed vulnerability affecting certain Android devices, allowing a malicious local app to read sensitive details about the device’s Bluetooth adapter
Episode
00:00:00
00:00:00