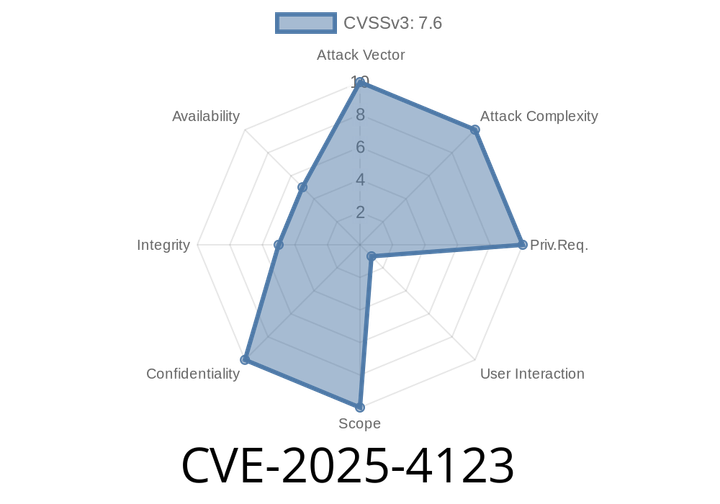
CVE-2025-4123 - Chained Path Traversal & Open Redirect Leads to XSS & SSRF in Grafana
A newly identified security flaw, CVE-2025-4123, exposes the popular monitoring dashboard Grafana to risk of both cross-site scripting (XSS) and server-side request forgery (SSRF) attacks.
CVE-2025-34027 - Remote Code Execution via Authentication Bypass and Race Condition in Versa Concerto SD-WAN
CVE-2025-34027 is a critical vulnerability affecting Versa Concerto SD-WAN orchestration platforms, specifically versions 12.1.2 through 12.2. (and potentially others). The flaw lies
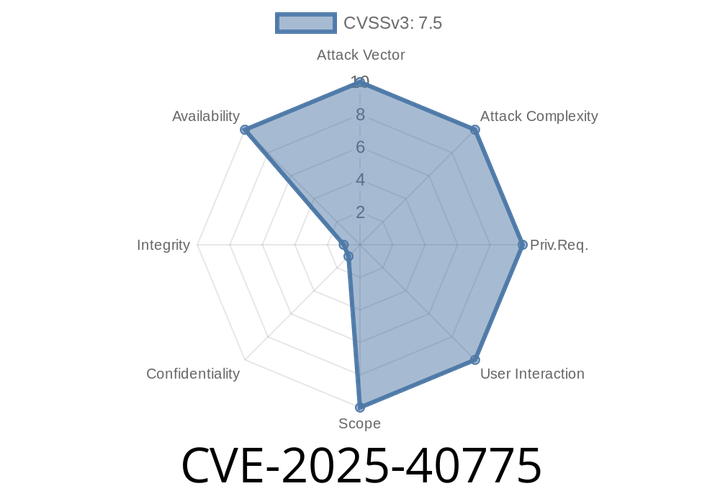
CVE-2025-40775 - BIND TSIG Algorithm Assertion Failure Leads to Crash (Exploit Details Inside)
In June 2025, security researchers disclosed CVE-2025-40775, a high-impact vulnerability in BIND, the world’s most popular DNS server software. If you run BIND 9.
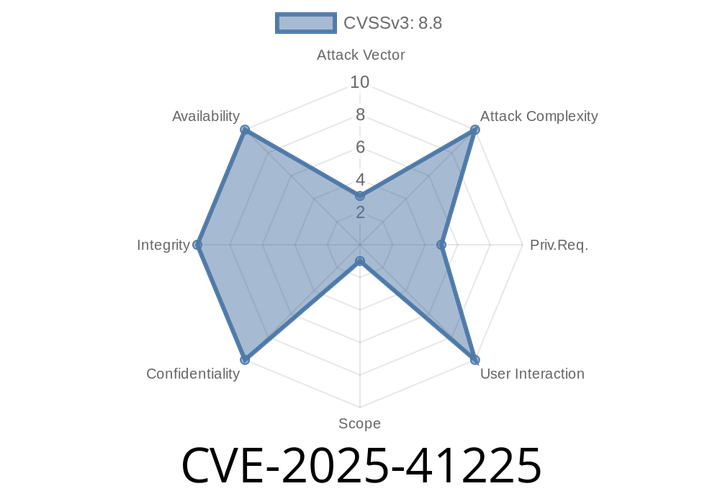
CVE-2025-41225 - Authenticated Command Execution in VMware vCenter Server – Deep Dive, Exploit, and Remediation
On June 5th, 2025, VMware disclosed CVE-2025-41225, a critical vulnerability in vCenter Server. This flaw allows any authenticated user with enough privileges to create or
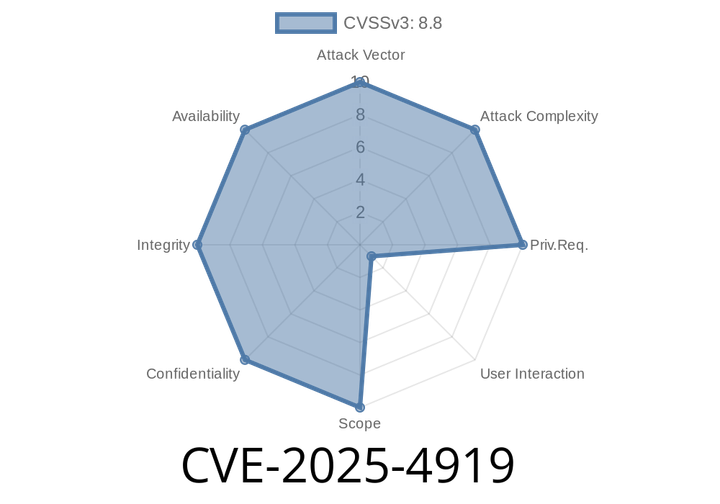
CVE-2025-4919 - Out-of-Bounds Read/Write via Array Index Confusion in Firefox and Thunderbird
---
In June 2025, security researchers and Mozilla announced a high-severity vulnerability tracked as CVE-2025-4919. This flaw impacted multiple versions of Firefox and Thunderbird—including
Episode
00:00:00
00:00:00