CVE-2022-31671 - How Harbor’s Weak Log Permissions Expose Your Job Logs
In today’s world, container registries like VMware Harbor are the backbone of cloud-native development. Harbor is valued for its security features, but even the
CVE-2022-31667 - How to Exploit Harbor's Robot Account Permission Bypass
> Exclusive Long Read: Understand and Exploit a Subtle but Serious Harbor Security Bug
What is Harbor?
Harbor is an open-source registry for storing, signing,
CVE-2023-34049 - How Predictable Script Paths in Salt-SSH Can Be Exploited for Privilege Escalation
Published: June 2024
Introduction
Recently, a severe vulnerability—CVE-2023-34049—was found in Salt Project’s Salt-SSH tool. This security flaw is serious because attackers who
CVE-2024-43093 - How Unicode Tricks Bypass Android’s Storage Protection
Security vulnerabilities in Android aren’t always about complex code—sometimes, it’s about tiny details, like how text is converted under the hood. CVE-2024-43093
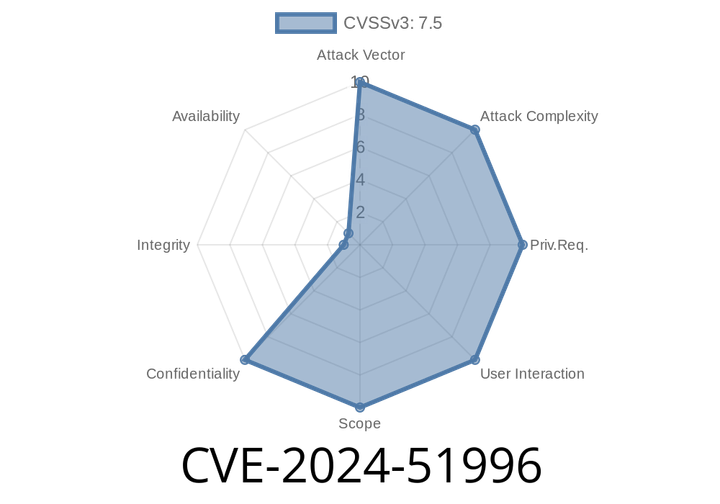
CVE-2024-51996 - Authentication Bypass in Symfony Remember-Me Feature Explained
The security of user authentication is critical in any web application. Recently, a new vulnerability—CVE-2024-51996—was discovered in the *Symfony* PHP framework that can
Episode
00:00:00
00:00:00