CVE-2025-4207 - Exploit Details & Simple Explanation – PostgreSQL GB18030 Buffer Over-read
---
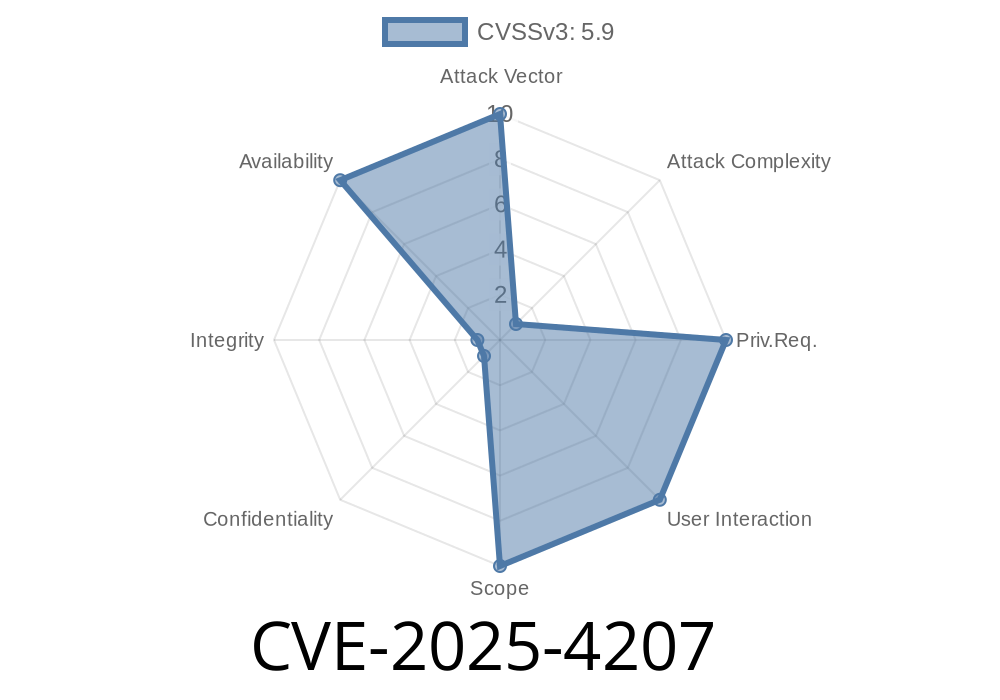
What is CVE-2025-4207?
CVE-2025-4207 is a buffer over-read vulnerability found in PostgreSQL’s handling of the GB18030 character encoding. This bug lets someone cause
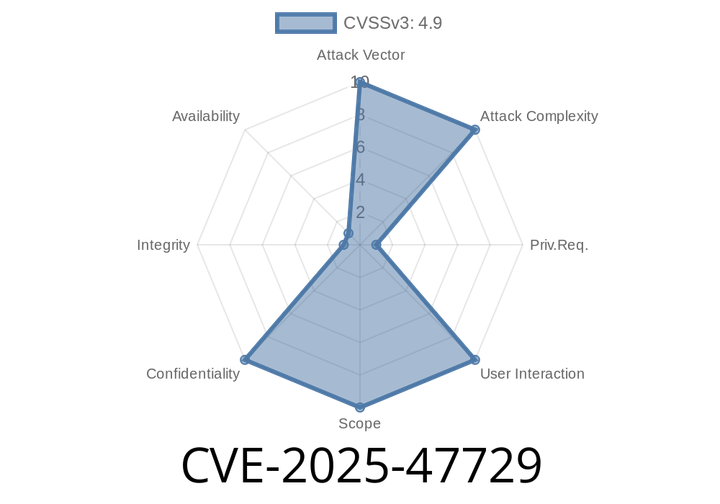
CVE-2025-47729 - How TeleMessage's Archive Signal Exposed Users’ Encrypted Messages in Plain Text
In May 2025, security researchers and threat actors alike discovered a major vulnerability in TeleMessage’s enterprise compliance archiving platform, specifically in its integration with
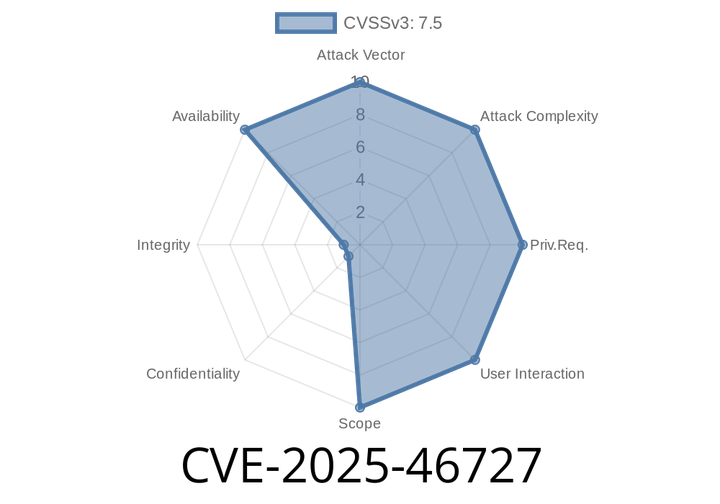
CVE-2025-46727 - Rack’s QueryParser Parameter Bomb (Denial-of-Service Vulnerability)
A new, critical vulnerability has been discovered in the Rack Ruby web server interface, identified as CVE-2025-46727. This vulnerability can cause denial-of-service (DoS) on any
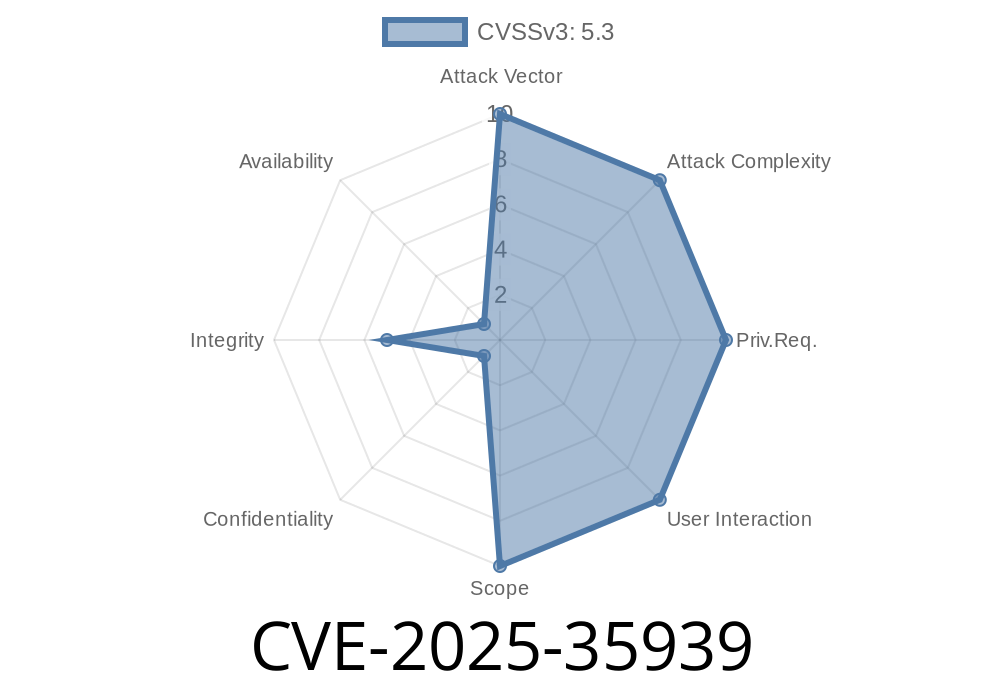
CVE-2025-35939 - How Unauthenticated Users Could Inject Content into Craft CMS Session Files
*Published: June 2024*
Craft CMS is a widely used content management system for building flexible websites and digital experiences. But recently, a serious vulnerability (tracked
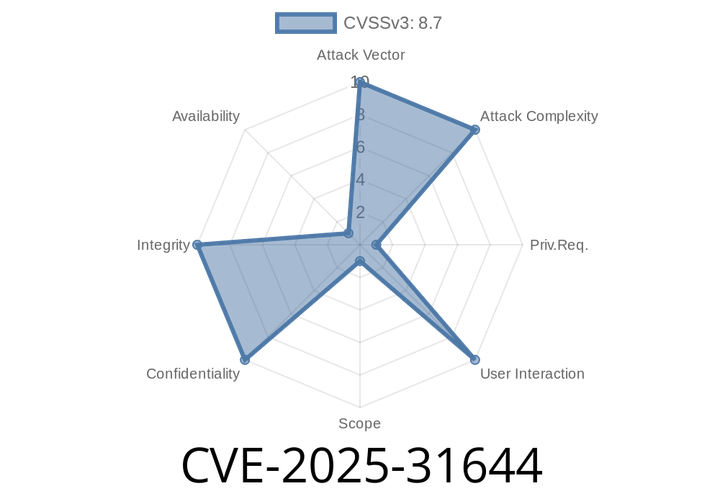
CVE-2025-31644 - Exploiting Command Injection in F5 BIG-IP iControl REST and TMOS Shell (tmsh)
On June 2025, a critical vulnerability (CVE-2025-31644) was disclosed in F5 BIG-IP systems, specifically when running in Appliance mode. This flaw allows authenticated administrators to
Episode
00:00:00
00:00:00