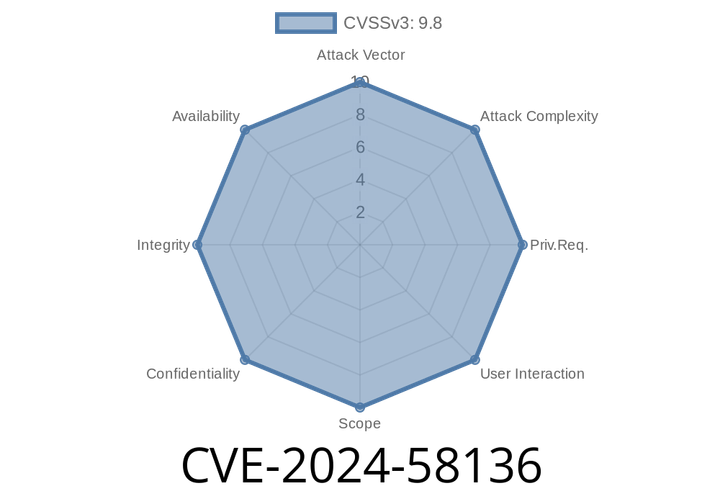
CVE-2024-58136 - Yii2 Behavior Attach Bypass & Wild Exploitation (Exclusive Long Read)
Intro
In the early months of 2025, security experts started noticing attacks leveraging a fresh vulnerability in Yii 2 web applications. Dubbed CVE-2024-58136, this bug
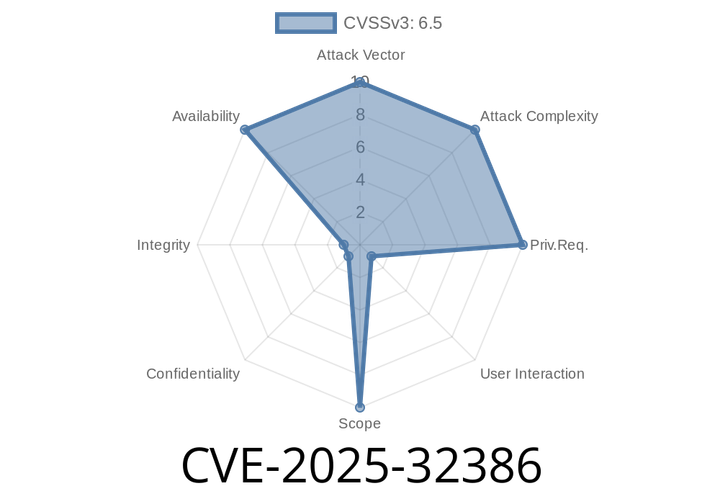
CVE-2025-32386 - Helm Chart Archive Decompression Bug Can Crash Your Apps – Full Analysis & Exploit Example
Summary:
If you use Helm to manage Kubernetes applications, there’s a security issue you should know: CVE-2025-32386. In versions before v3.17.3, Helm
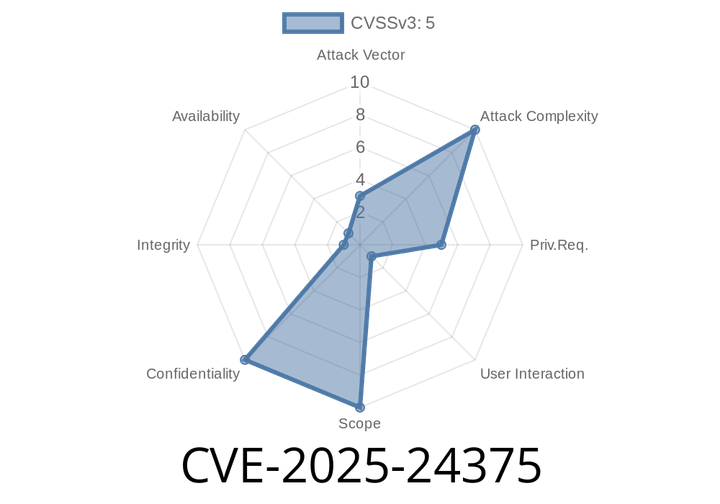
CVE-2025-24375 - Critical Credential Disclosure in Charmed MySQL K8s Operator
A recent vulnerability tracked as CVE-2025-24375 was discovered in the Charmed MySQL Kubernetes (K8s) Operator, which is a popular Charmed Operator for managing MySQL clusters
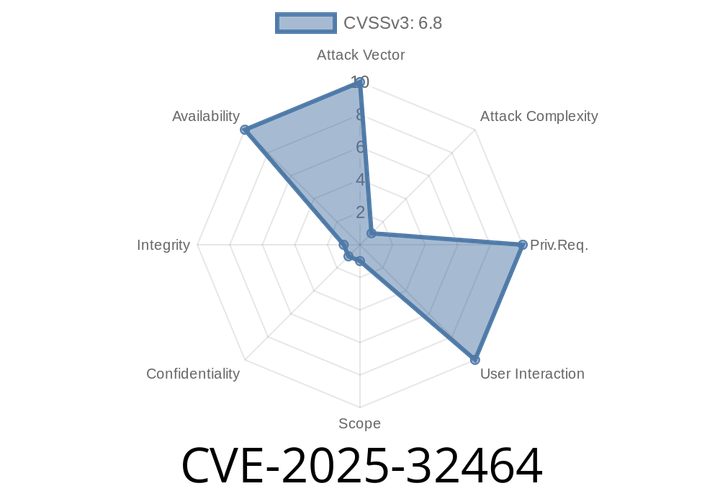
CVE-2025-32464 - HAProxy Buffer Overflow – What You Need to Know, How It Works, and Example Exploit
HAProxy is a popular open-source load balancer and proxy server, widely used for distributing traffic in high-availability environments. While it's known for its
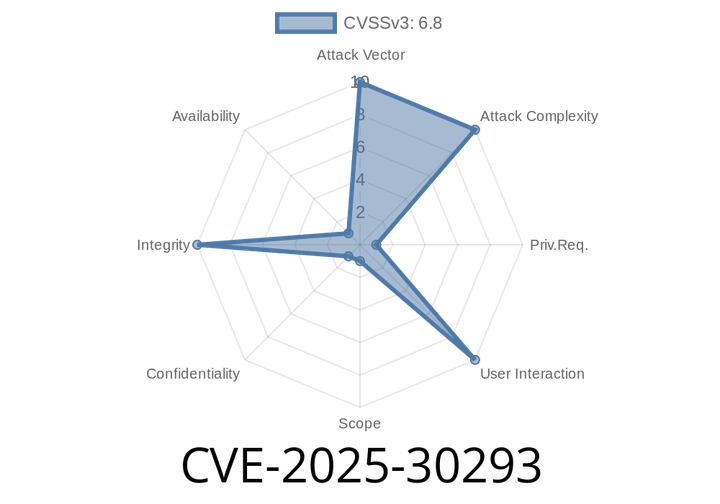
CVE-2025-30293 - High-Privilege Security Bypass in Adobe ColdFusion (Exclusive Analysis & Exploit Insight)
A new high-severity vulnerability—CVE-2025-30293—has been discovered in Adobe ColdFusion versions 2023.12, 2021.18, 2025., and earlier. The flaw arises from improper input
Episode
00:00:00
00:00:00