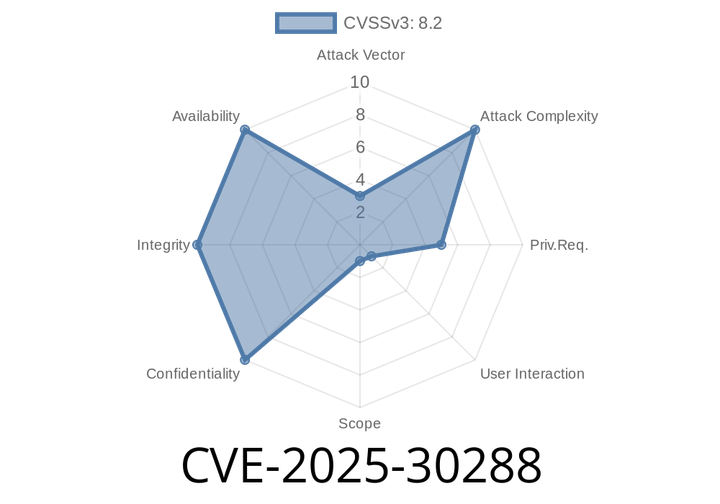
CVE-2025-30288 - Bypassing Security Features in Adobe ColdFusion – How Attackers Could Execute Code
In early 2024, a major vulnerability was disclosed in several versions of Adobe ColdFusion, tracked as CVE-2025-30288. Security teams everywhere are scrambling to understand what’
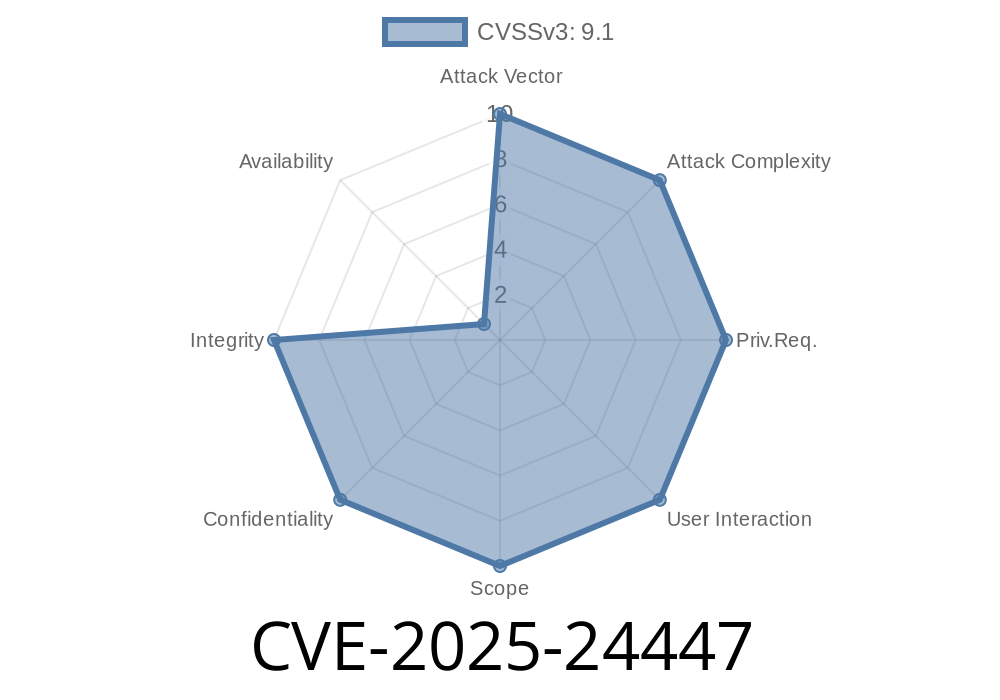
CVE-2025-24447 - Critical ColdFusion Deserialization Vulnerability (Exclusive Breakdown & Exploit Details)
In June 2024, Adobe published a critical security bulletin addressing a serious vulnerability in ColdFusion. Tracked as CVE-2025-24447, this flaw allows attackers to remotely execute
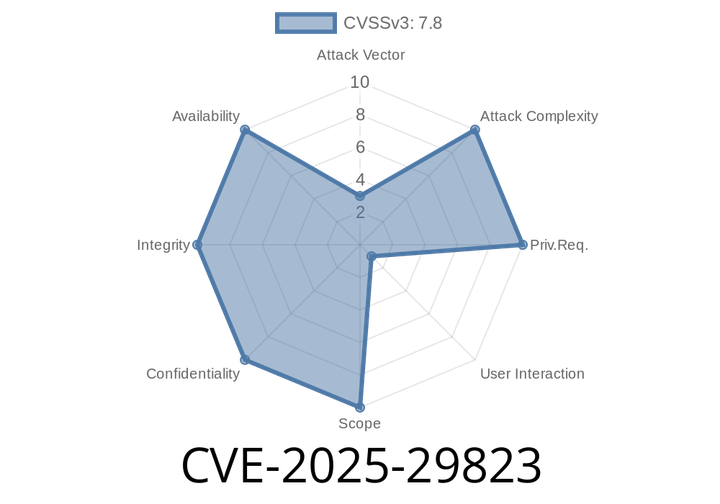
CVE-2025-29823 - Use-After-Free in Microsoft Excel — Exploit Details, Code, and How Attackers Can Execute Code Locally
Microsoft Office Excel is ubiquitous in businesses and homes—it’s everywhere. With its popularity comes risk, and every year we see dangerous vulnerabilities. One
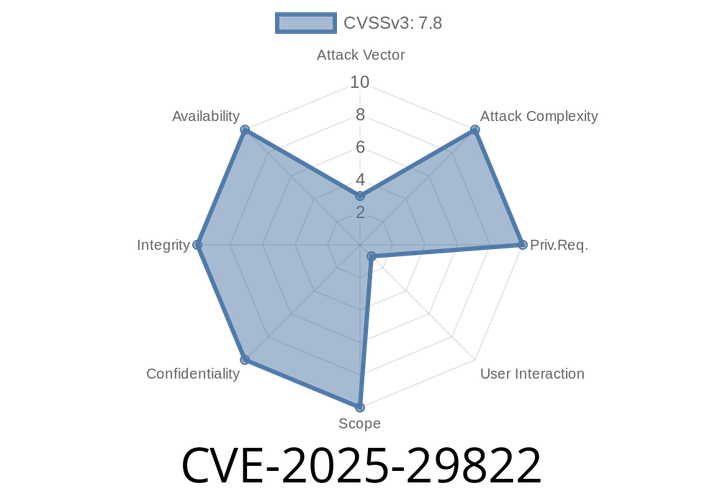
CVE-2025-29822 - How a List Oversight in Microsoft OneNote Can Let Attackers Slip Through—With Code, Exploit & Details
Cybersecurity researchers are sounding the alarm over a newly disclosed vulnerability: CVE-2025-29822. This flaw, found in Microsoft Office OneNote, lets a local attacker bypass important
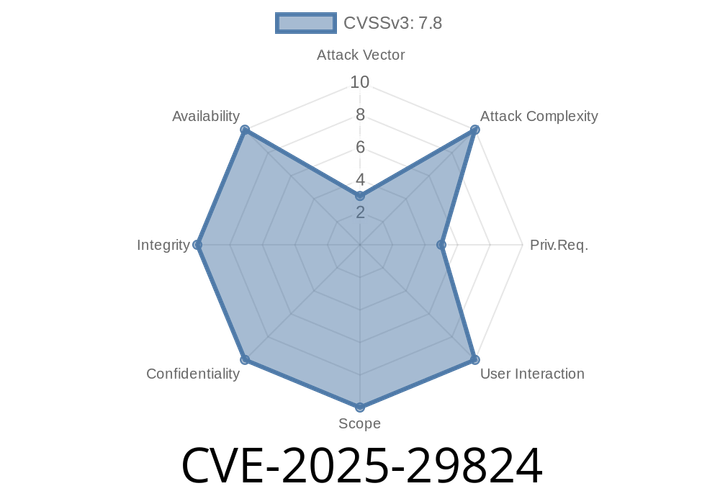
CVE-2025-29824 - Exploring a Use-After-Free Vulnerability in Windows Common Log File System Driver for Local Privilege Escalation
Recently, a new vulnerability (CVE-2025-29824) has been identified in the Windows Common Log File System (CLFS) Driver that allows an authorized attacker to exploit Use-After-Free
Episode
00:00:00
00:00:00