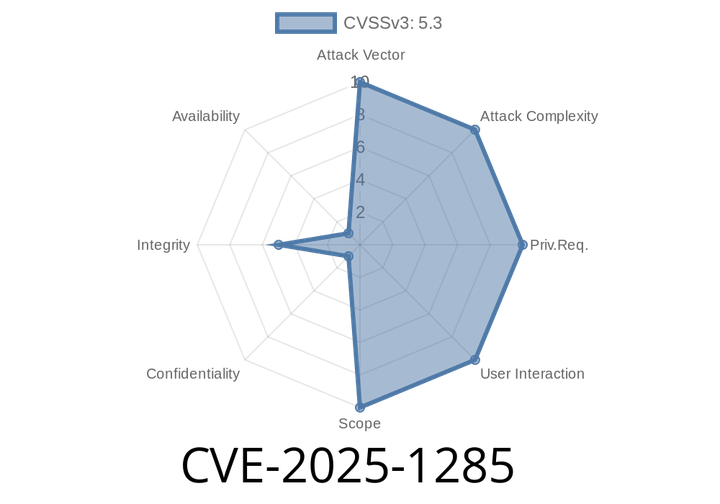
CVE-2025-1285 - How Unauthorized Attackers Can Hijack Resido Real Estate WordPress Sites
In early 2025, a high-risk security flaw was uncovered in the popular Resido - Real Estate WordPress Theme. This vulnerability, tracked as CVE-2025-1285, allows anyone—
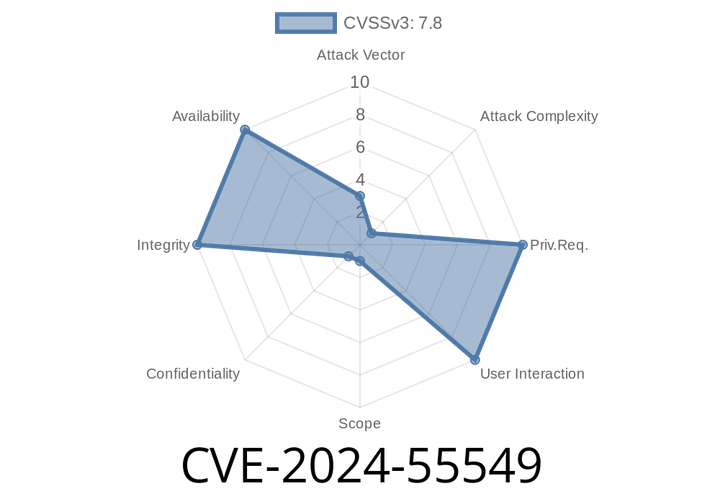
CVE-2024-55549 - Breaking Down libxslt’s xsltGetInheritedNsList Use-After-Free Bug
In June 2024, a new vulnerability tracked as CVE-2024-55549 was identified in the popular XML stylesheet library libxslt. This bug, lurking since before version 1.
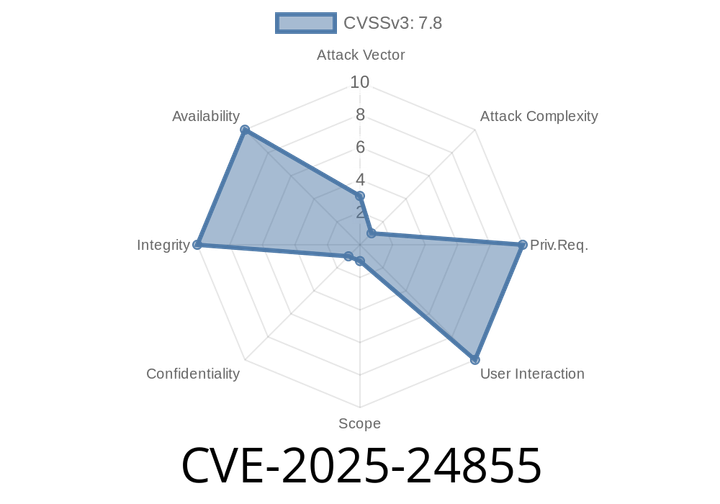
CVE-2025-24855 - Exploiting Use-After-Free in libxslt’s numbers.c (Before 1.1.43) – A Hands-On Guide
---
Introduction: What is CVE-2025-24855?
CVE-2025-24855 uncovers a dangerous use-after-free vulnerability in libxslt (prior to version 1.1.43). The issue lurks in numbers.c,
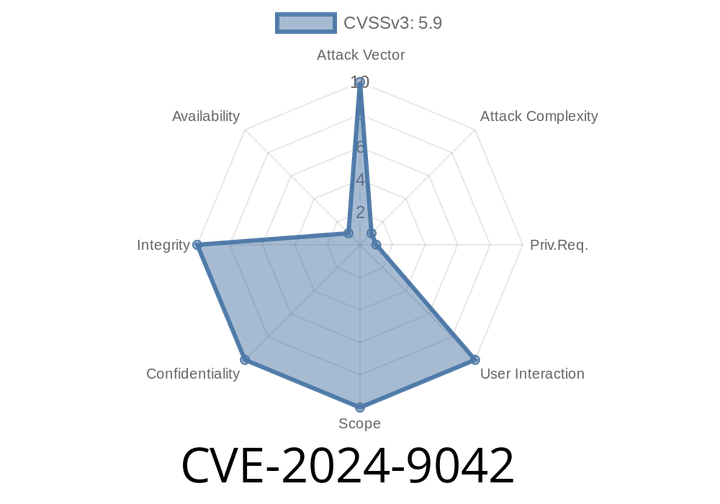
CVE-2024-9042 - Critical Kubernetes Privilege Escalation on Windows Worker Nodes
In early 2024, security researchers discovered a major vulnerability in Kubernetes that specifically impacts Windows worker nodes. Documented as CVE-2024-9042, this flaw allows attackers to
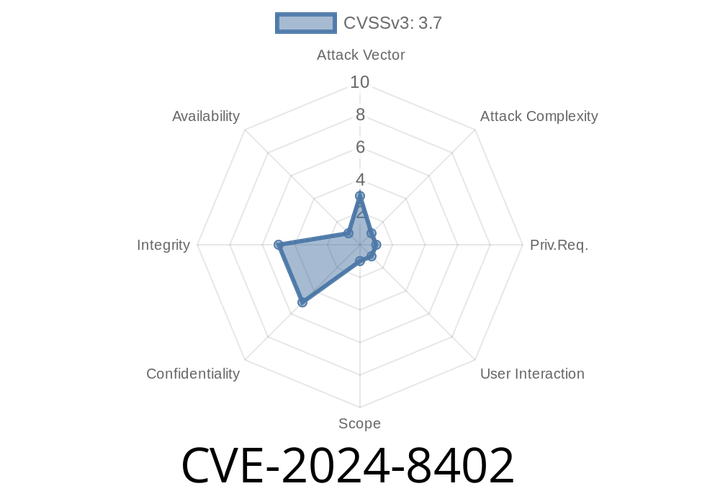
CVE-2024-8402 - Exploiting Google Cloud IAM Integration in GitLab EE – Exploit Analysis, Code Sample, and Mitigation
CVE-2024-8402 is a security vulnerability found in GitLab Enterprise Edition (EE) impacting the Google Cloud IAM integration feature. This flaw affects:
All versions from 17.
Episode
00:00:00
00:00:00