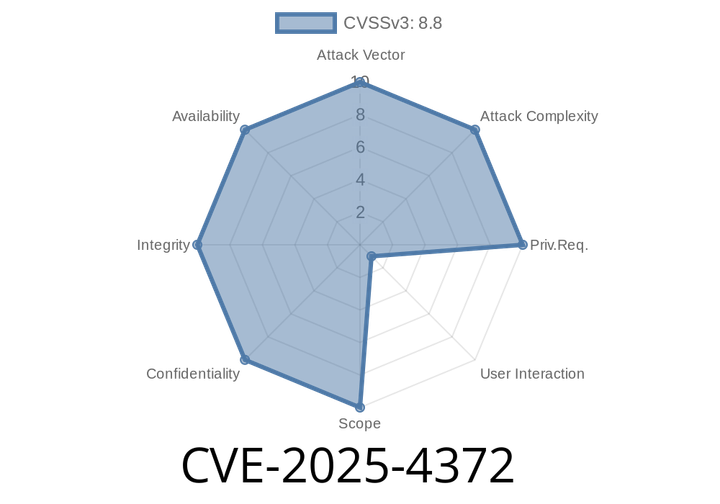
CVE-2025-4372 - Exploiting Use-After-Free in WebAudio on Google Chrome (Pre-136..7103.92)
In early 2025, a new Chrome vulnerability was disclosed: CVE-2025-4372. This bug allows remote attackers to corrupt the heap by exploiting a Use-After-Free (UAF) flaw
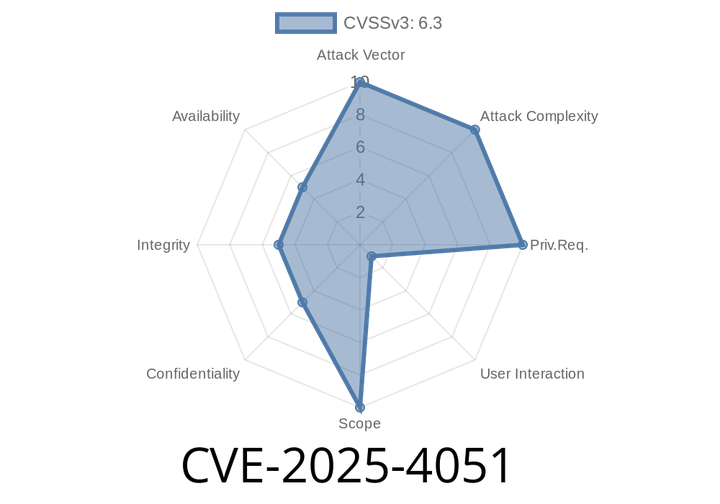
CVE-2025-4051 - How a Data Validation Flaw in Google Chrome DevTools Opened the Door for Remote Attacks
On June 2024, a new vulnerability—CVE-2025-4051—was made public, impacting Google Chrome versions prior to 136..7103.59. The flaw sits in Chrome’s
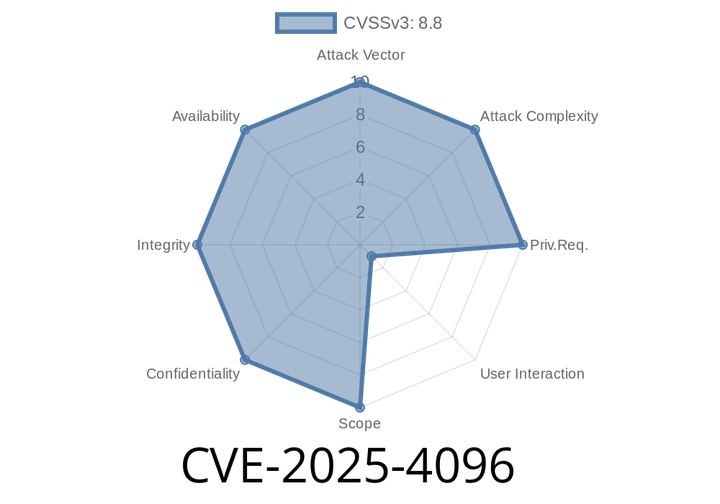
CVE-2025-4096 - Heap Buffer Overflow in HTML Parsing in Google Chrome – Exploit Analysis and Details
---
Overview
In early June 2024, Google Chrome patched a critical security flaw, identified as CVE-2025-4096, that could allow attackers to exploit heap memory corruption
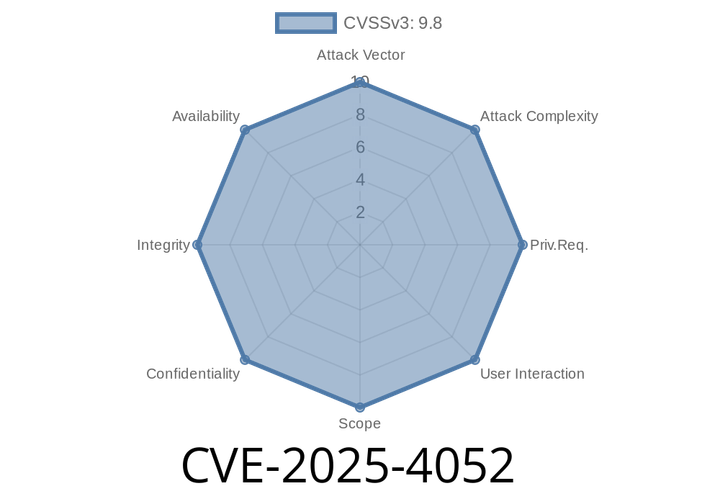
CVE-2025-4052 - How a Chrome DevTools Bug Let Remote Attackers Bypass Access Controls
Google Chrome is famous for its strong security features, but even the best have cracks. In early 2025, a fresh vulnerability emerged—tracked as CVE-2025-4052,
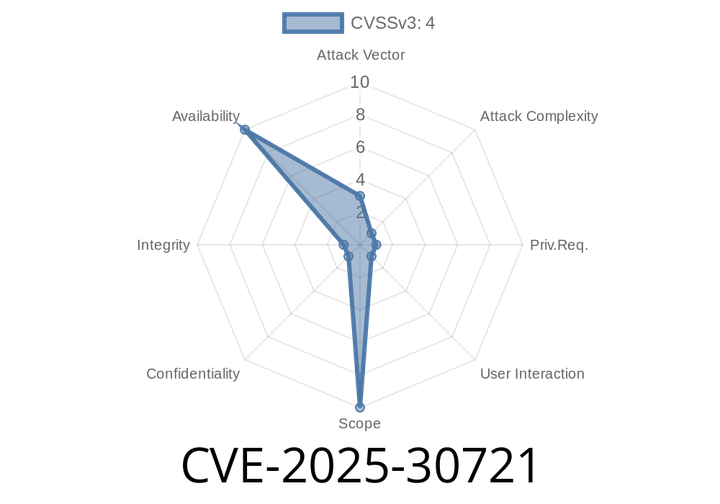
CVE-2025-30721 - Deep Dive into DoS Vulnerability in Oracle MySQL Server’s UDF Engine
CVE-2025-30721 is a new vulnerability affecting Oracle's MySQL Server, specifically in the Server: UDF (User Defined Function) component. This flaw is stirring conversations
Episode
00:00:00
00:00:00