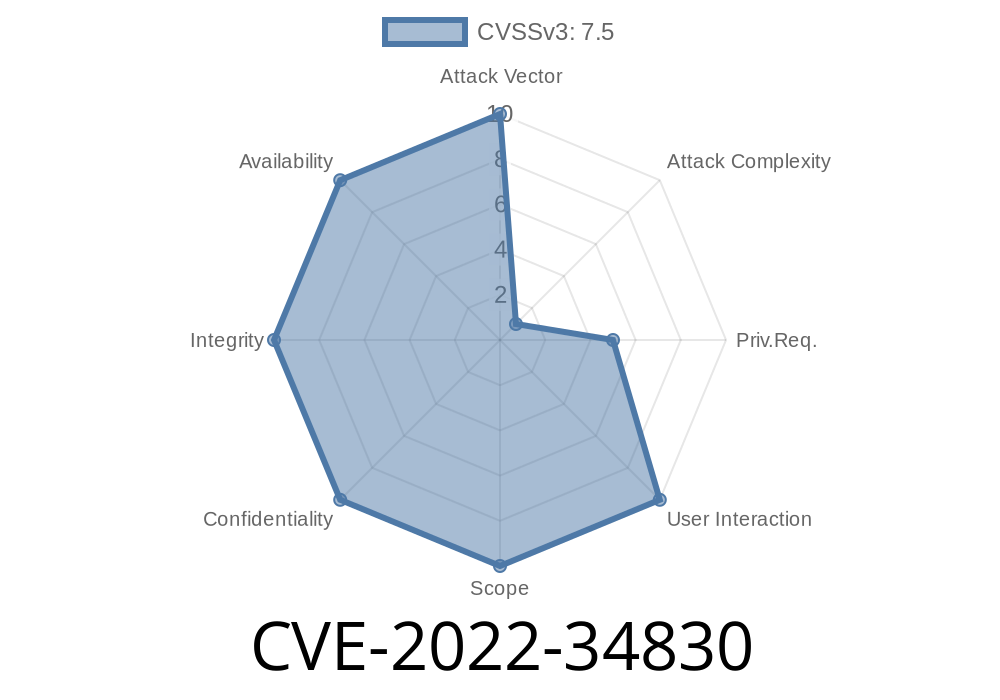
CVE-2022-34830 - How a Race Condition in ARM GPUs Lets Attackers Access Freed Memory
In 2022, a vulnerability labeled CVE-2022-34830 was disclosed that affects certain ARM GPU drivers—specifically those in use up to June 29, 2022. This bug
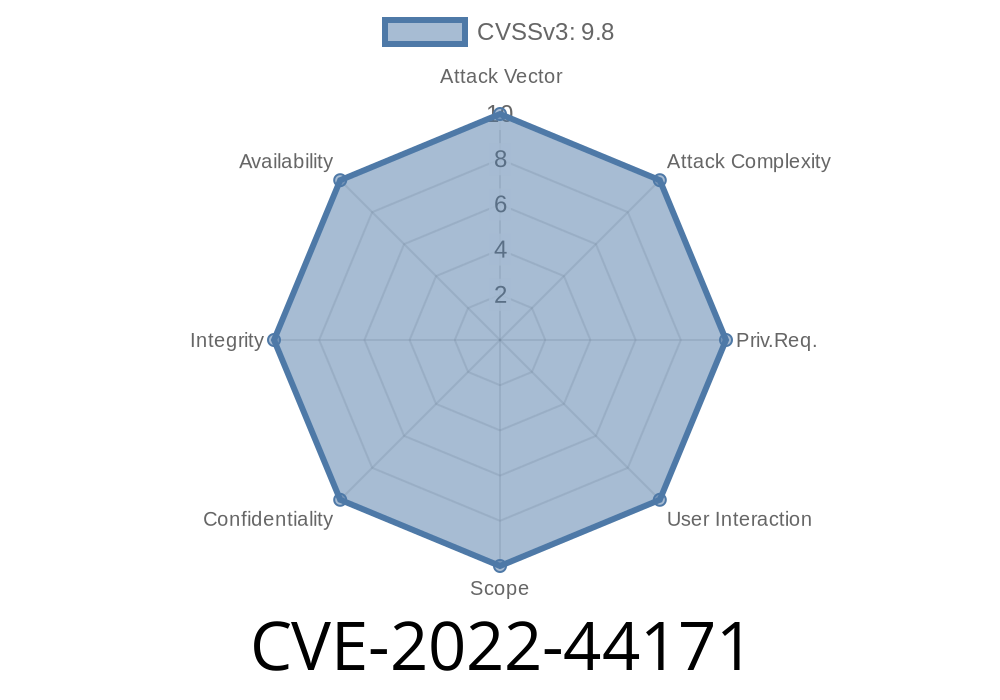
CVE-2022-44171 - Unpacking the Buffer Overflow Vulnerability in Tenda AC18 (V15.03.05.19) – Exploit, Code Proof and Fix
In the world of home and office networking, Tenda routers are known for their affordability and widespread use. However, like any device, they're
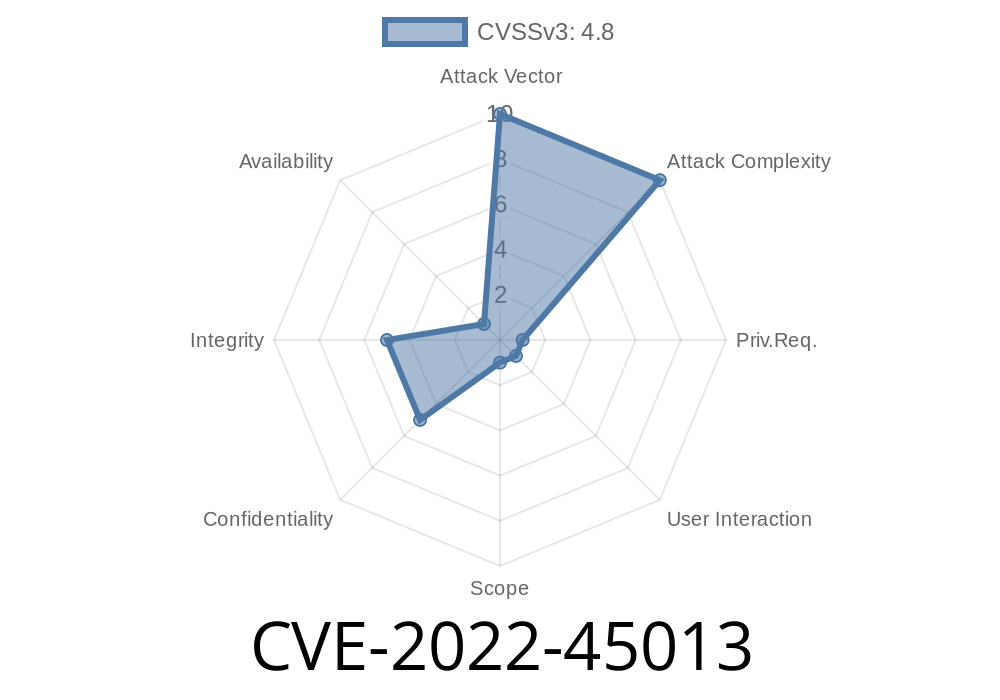
CVE-2022-45013 An XSS vulnerability in the Show Advanced Option module of WBCE CMS v1.5.4 allows attackers to execute arbitrary web scripts or HTML.
An attacker may exploit this vulnerability by submitting a crafted URL into the Section Header field.
To exploit this vulnerability, an attacker needs to submit
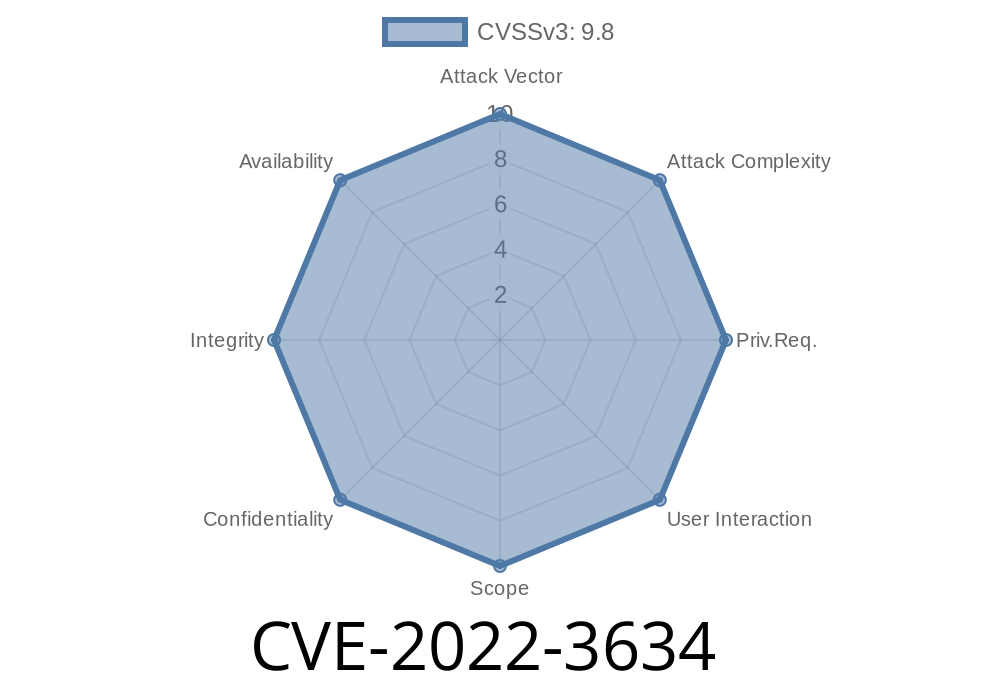
CVE-2022-3634 - How Contact Form 7 Database Addon Plugin for WordPress Exposed Sites to CSV Injection Attacks
If you use WordPress, chances are you rely on plugins to extend your website’s features. One popular plugin, Contact Form 7 Database Addon – CFDB7,
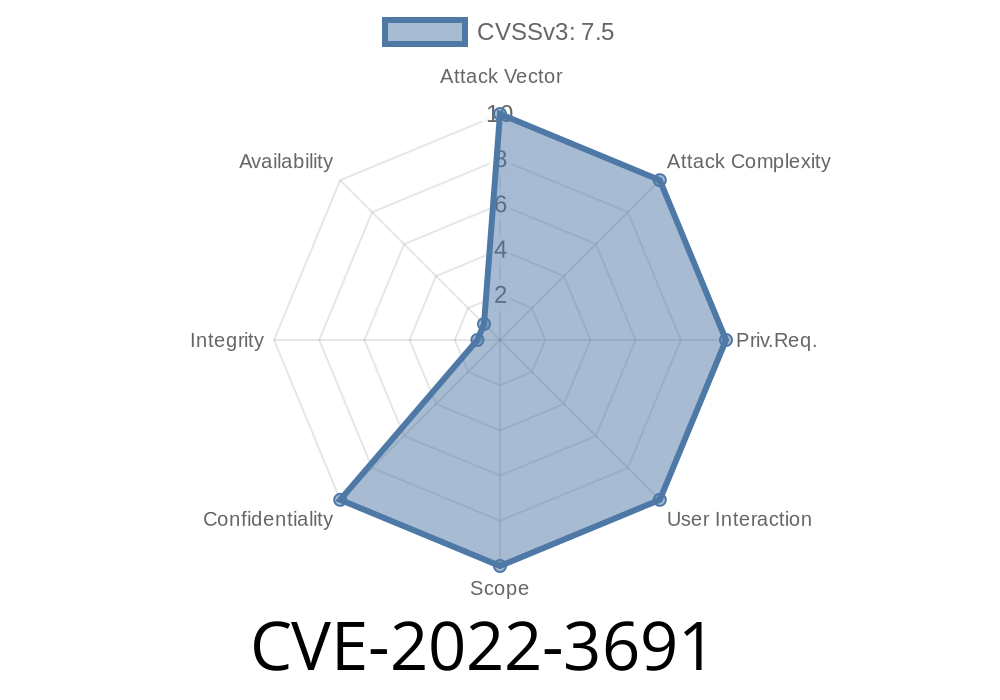
CVE-2022-3691 The DeepL Pro API translation plugin before 1.7.5 leaks sensitive information in its log files, including the API key.
The DeepL developer recommends not disabling the plugin’s logging and keeping a backup of the log files to monitor for security issues and to
Episode
00:00:00
00:00:00