CVE-2022-20141 - Understanding a Use-After-Free Vulnerability in Android Kernel’s igmp.c (ip_check_mc_rcu)
Security in the Android operating system heavily depends on the safety of the Linux kernel. What happens when the kernel has a bug that attackers
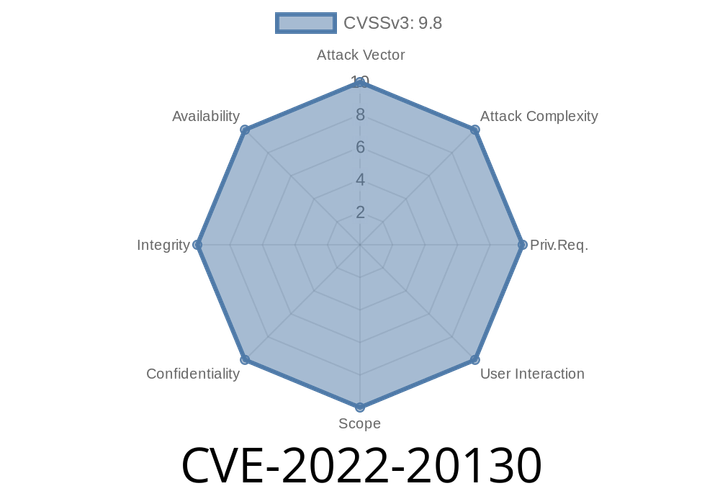
CVE-2022-20130 - How A Heap Overflow in Android’s tpdec_lib.cpp Opens the Door to Remote Code Execution
Summary:
On June 2022, Google publicly acknowledged CVE-2022-20130, a serious security flaw in Android’s tpdec_lib.cpp. This bug, rooted in an out-of-bounds write
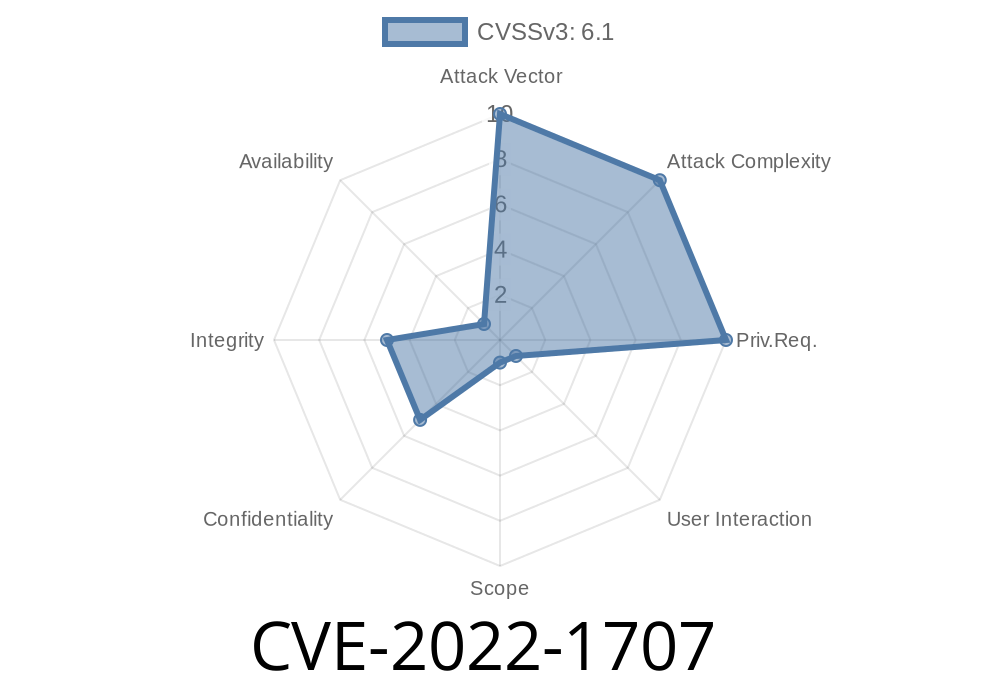
CVE-2022-1707 The Google Tag Manager for WordPress plugin is vulnerable to reflected Cross-Site Scripting due to the site search populating into the data layer. This ranges from up to and including 1.15.
Google Tag Manager for WordPress is a plugin for WordPress that helps you manage your Google Analytics, AdWords, and Google Search campaigns from inside WordPress.
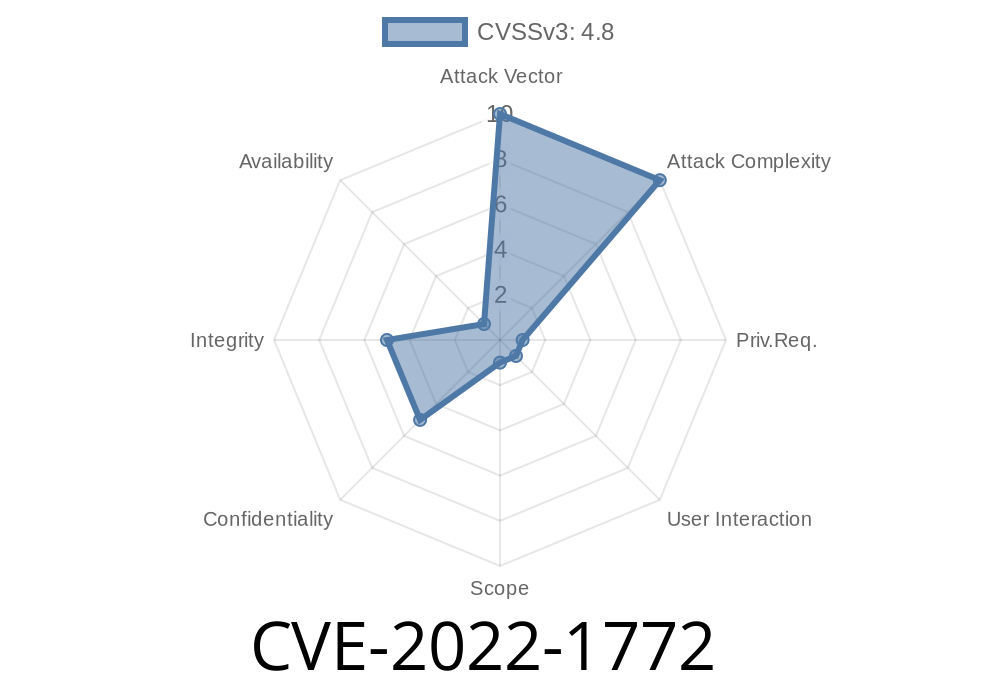
CVE-2022-1772 The Google Places Reviews plugin before 2.0.0 did not properly escape its API key, which is reflected on the site's administration panel.
In the latest 2.0.0 version of the plugin, the Google Places Reviews code has been refactored to fix this issue. If you are
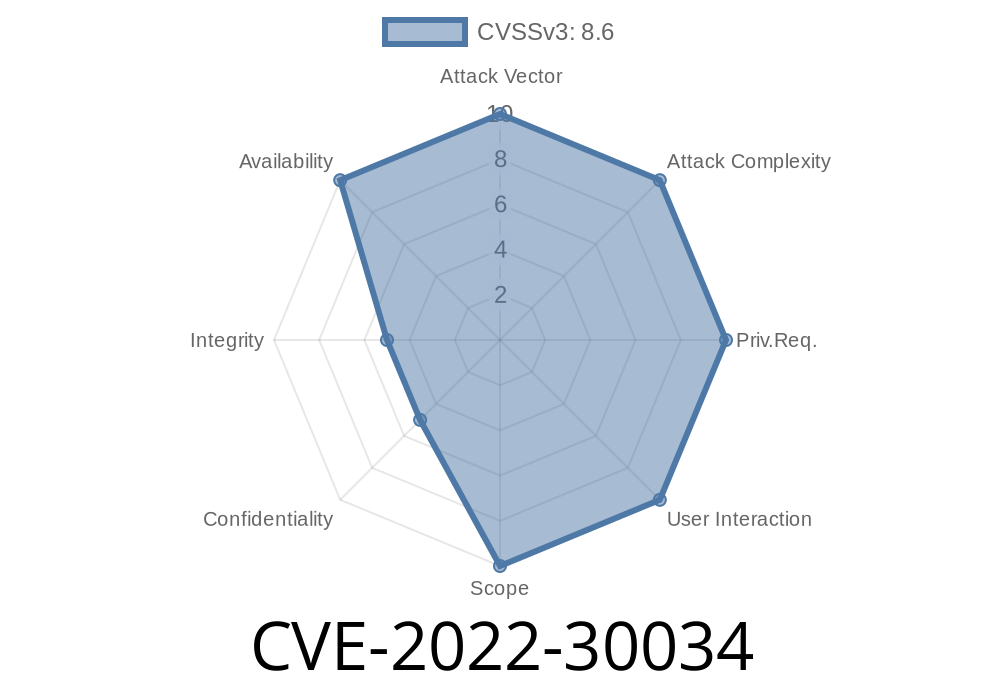
CVE-2022-30034 Flower, a web UI for the Celery Python RPC framework, is vulnerable to an OAuth authentication bypass.
OAuth is a widely used authentication protocol. It provides a secure way for users to grant permission for their data to be accessed by authorized
Episode
00:00:00
00:00:00