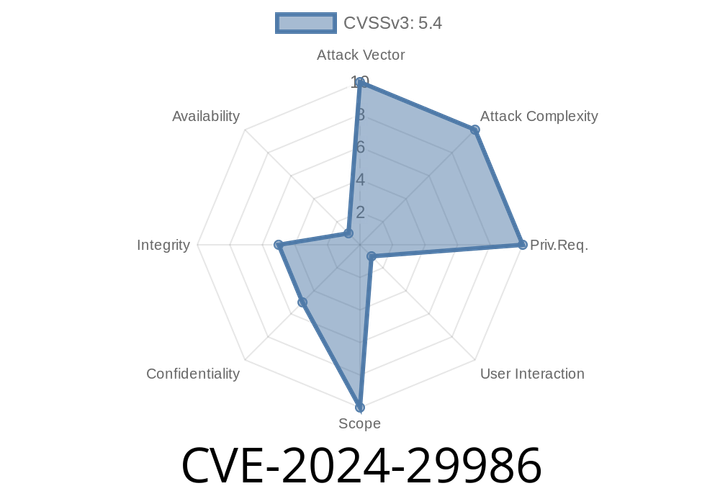
CVE-2024-29986 - Understanding the Microsoft Edge for Android Information Leak
In early 2024, a new vulnerability making rounds in the security community caught the eye of Android and Microsoft Edge users: CVE-2024-29986. This article will
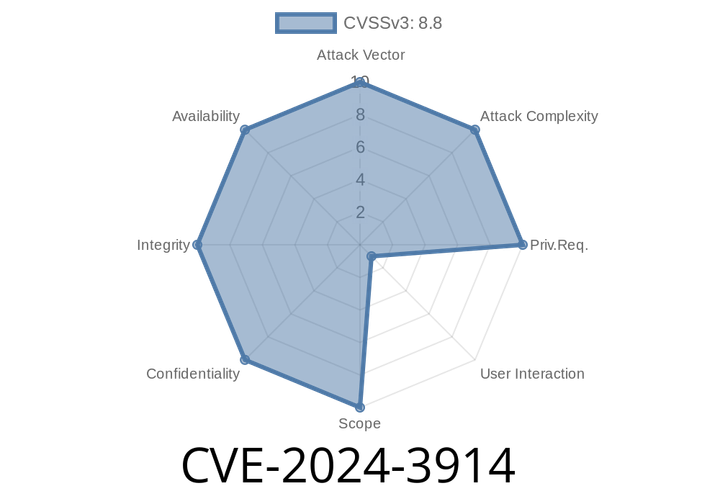
CVE-2024-3914 - Understanding and Exploiting the Use-After-Free in Chrome V8 Engine
---
Summary
CVE-2024-3914 is a critical use-after-free vulnerability discovered in the V8 JavaScript engine, impacting Google Chrome versions prior to 124..6367.60. This flaw
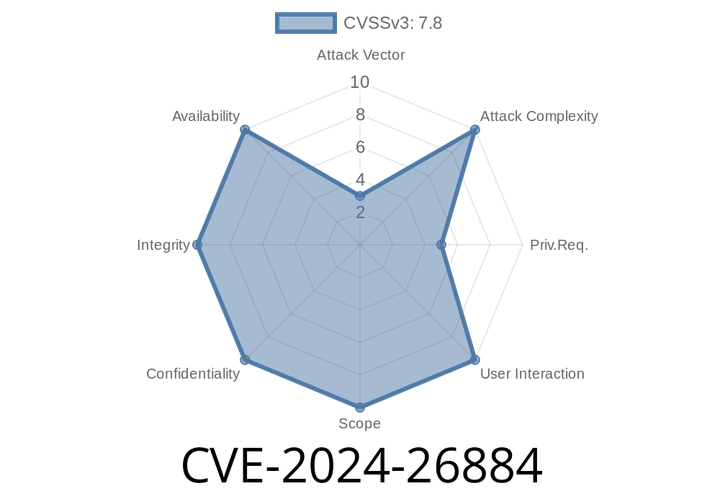
CVE-2024-26884 - Linux Kernel BPF Hashtab Overflow Vulnerability (32-bit)
A new Linux kernel security issue—CVE-2024-26884—has drawn attention from kernel developers, sysadmins, and security enthusiasts. If you run or administer Linux systems, especially
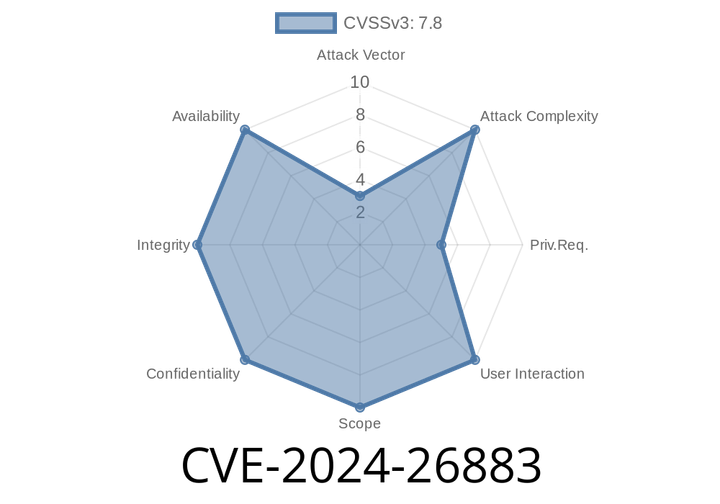
CVE-2024-26883 - Linux Kernel stackmap Overflow on 32-bit Systems Explained
Linux security is always crucial, especially around the eBPF (extended Berkeley Packet Filter) subsystem, which powers things like tracing and performance monitoring. On 32-bit chips,
CVE-2024-26865 - Exploiting a Use-After-Free in Linux Kernel RDS TCP reqsk_timer_handler()
---
The Linux kernel is the beating heart of countless servers, devices, and systems worldwide. With such complexity, even obscure bugs can present serious issues
Episode
00:00:00
00:00:00