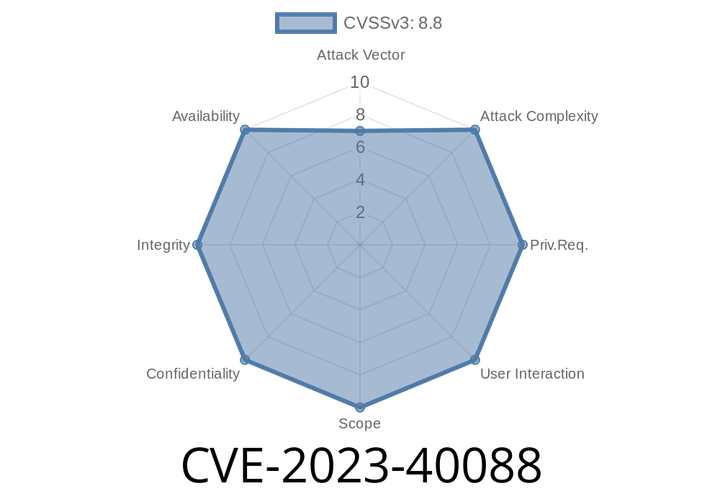
CVE-2023-40088 - How a Bluetooth Use-After-Free Bug in Android Can Lead to Code Execution
Android has long been a leader in connecting devices wirelessly, with Bluetooth playing a central role in most phones and smart gadgets today. But sometimes,
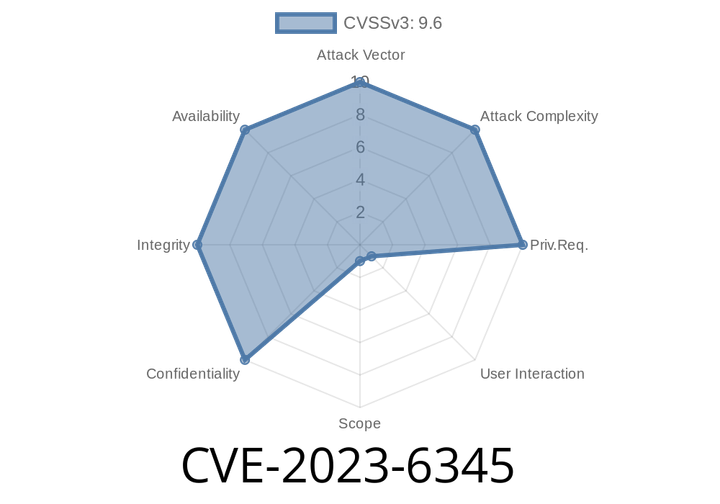
CVE-2023-6345 - How an Integer Overflow in Skia Led to Chrome Sandbox Escape (Explained Simply)
On November 28, 2023, Google published a high-severity vulnerability affecting Chrome: CVE-2023-6345. This flaw targets the graphics library Skia, which Chrome uses to render images
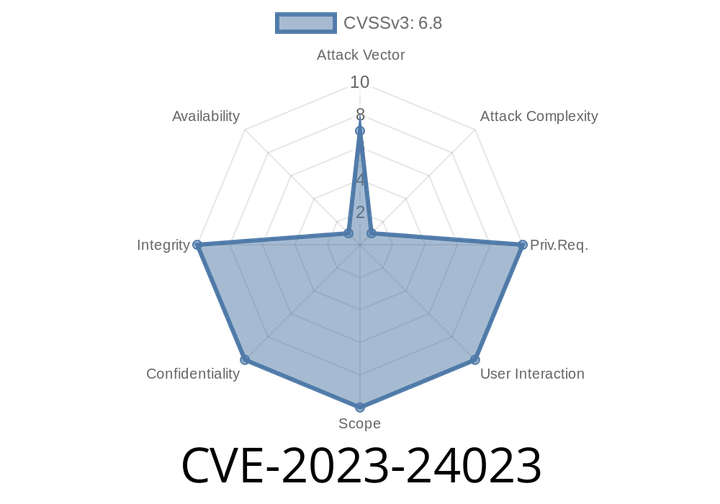
CVE-2023-24023 - How BLUFFS can Break Bluetooth Security (Easy Read, Full Exploit Walkthrough)
Bluetooth is everywhere—from your headphones to your car’s entertainment. But a newly published vulnerability, CVE-2023-24023, proves that even the most common tech is
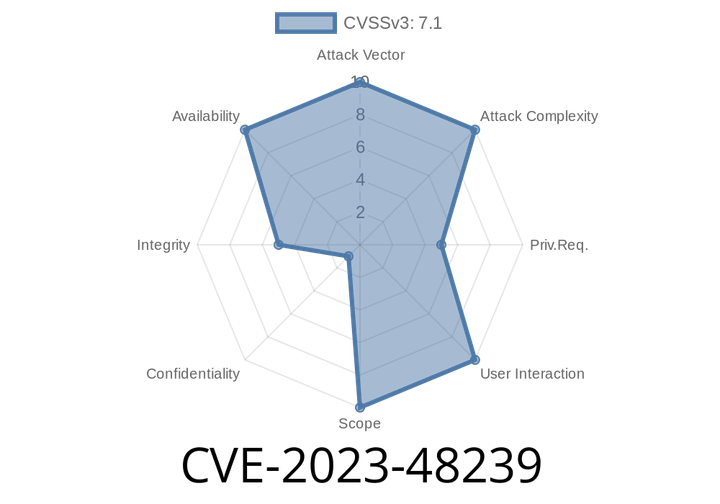
CVE-2023-48239 - How a Malicious User Could Break Nextcloud’s External Storage for Everyone
Nextcloud Server is a popular self-hosted, open-source cloud solution, used around the world for storing data, sharing files, and syncing documents with teams. But recently,
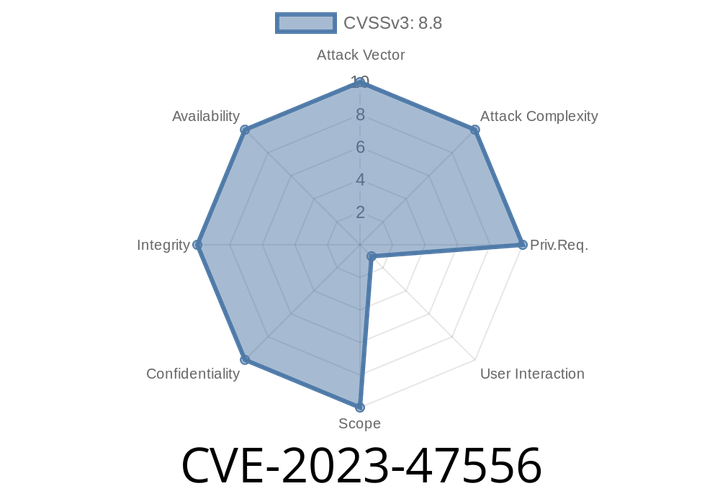
CVE-2023-47556 - Understanding and Exploiting the CSRF Vulnerability in Device Theme Switcher (<=3..2)
The world of WordPress security is constantly changing, and every so often, a critical vulnerability comes to light—sometimes, in a plugin you might never
Episode
00:00:00
00:00:00