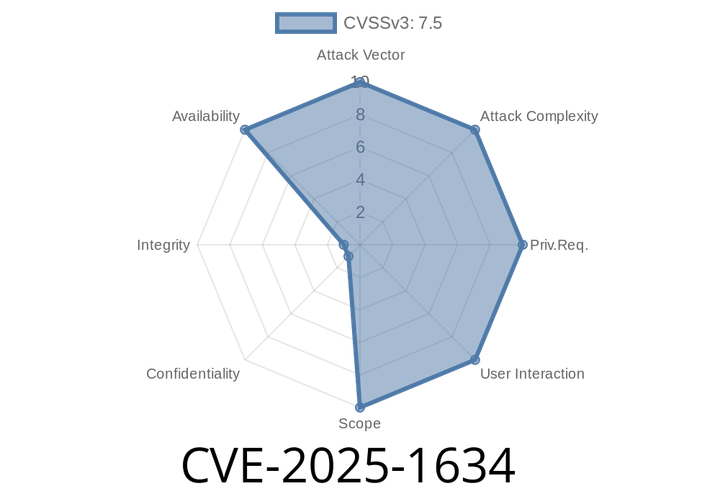
CVE-2025-1634 - Memory Leak in quarkus-resteasy Leads to OutOfMemoryError — Detailed Analysis & Exploit Guide
Published: June 2024
Severity: High
Introduction
A critical vulnerability labeled CVE-2025-1634 was discovered in the popular Java framework extension quarkus-resteasy. This flaw can cause your
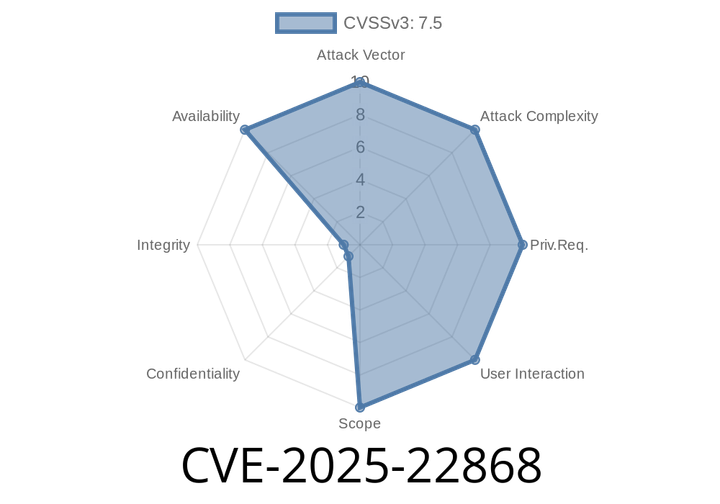
CVE-2025-22868 - Malformed Token Exploit Consumes Excessive Memory (Full Details, Code Sample, Impact)
In early 2025, a significant vulnerability tagged CVE-2025-22868 was discovered that puts many web applications and API services at risk. This post breaks down what
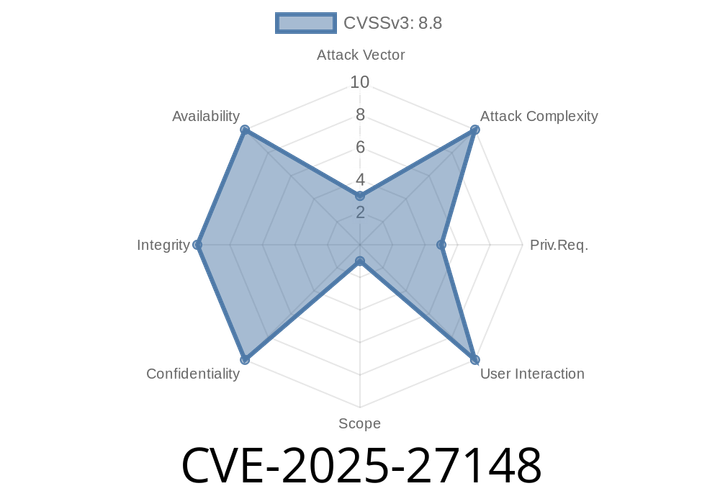
CVE-2025-27148 - How Gradle’s Native-Platform Temporary File Handling Led to Local Privilege Escalation Risk
---
Summary:
A recent vulnerability—CVE-2025-27148—impacts users of the Gradle build automation tool, specifically through its native-platform integration. Due to how temporary files were
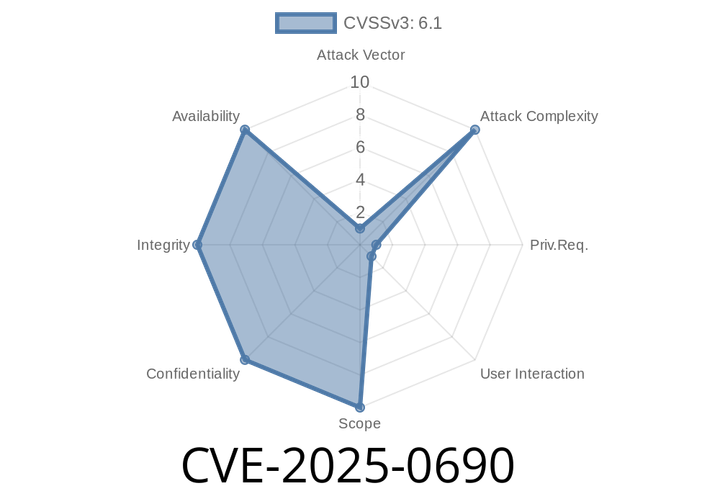
CVE-2025-0690 - GRUB2: Critical Out-of-Bounds Write Vulnerability
GRUB2 (the GRand Unified Bootloader version 2) plays an essential role in the boot process of any modern computer. It's the first software
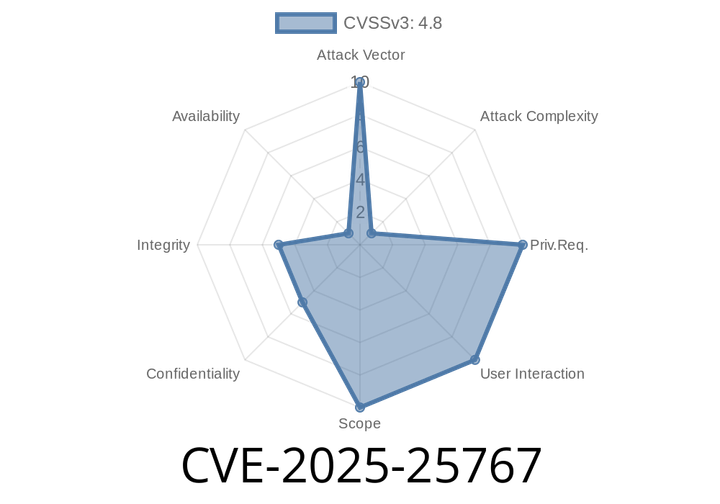
CVE-2025-25767 - Vertical Privilege Escalation in MRCMS 3.1.2 – Arbitrary User Deletion via /controller/UserController.java
A newly identified security flaw, CVE-2025-25767, puts the widely used MRCMS version 3.1.2 at risk. This vulnerability involves a vertical privilege escalation in
Episode
00:00:00
00:00:00