CVE-2024-53677 - How a Dangerous File Upload Bug in Apache Struts Can Lead to Remote Code Execution
TL;DR:
Apache Struts had a severe vulnerability (CVE-2024-53677) in its file upload logic, present from version 2.. up to (but not including) 6.4.
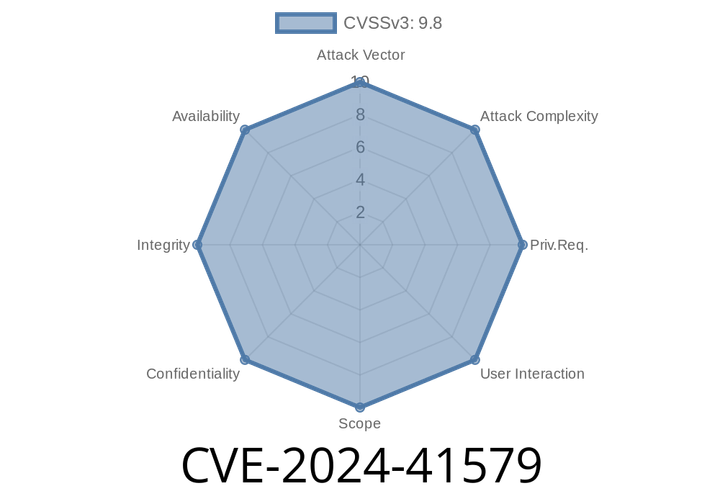
CVE-2024-41579 - Remote SQL Injection in DTStack Taier 1.4. Explained (With Exploit Details)
On May 2024, a critical SQL injection vulnerability was discovered in DTStack Taier version 1.4.. This flaw allows a remote attacker to execute arbitrary
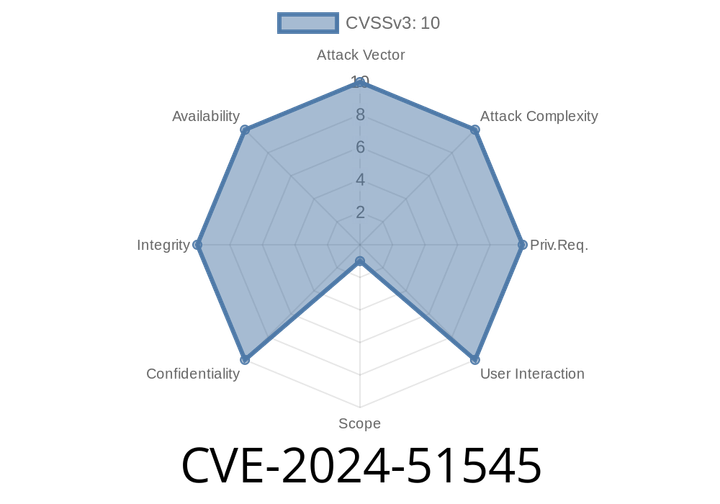
CVE-2024-51545 - Username Enumeration in ABB ASPECT, NEXUS Series, and MATRIX Series v3.08.02
Published: June 2024
Affected Products:
In Simple Terms: What’s the Issue?
CVE-2024-51545 describes a Username Enumeration vulnerability in ABB ASPECT - Enterprise, NEXUS Series,
CVE-2022-41137 - Practical Guide to Exploiting Apache Hive Metastore RCE via Unsafe Deserialization
In 2022, a severe vulnerability was discovered in Apache Hive Metastore (HMS): CVE-2022-41137. This security issue can allow an attacker to remotely execute code on
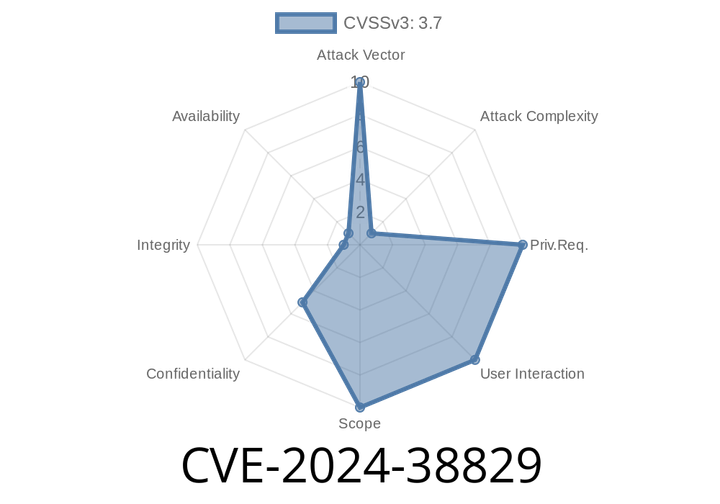
CVE-2024-38829 - Simple Breakdown and Exploit Details for Spring LDAP Case Sensitivity Flaw
In June 2024, a serious security issue was reported in Spring LDAP, a popular Java library used for LDAP (Lightweight Directory Access Protocol) integration. This
Episode
00:00:00
00:00:00