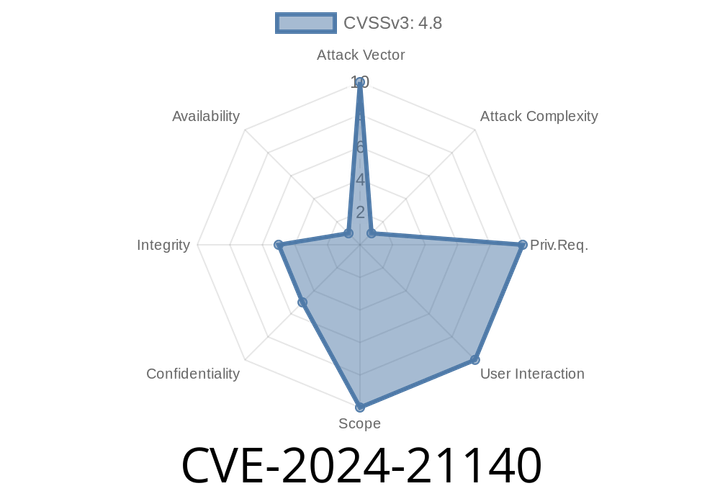
CVE-2024-21140 - Exploiting the HotSpot Vulnerability in Oracle Java SE and Oracle GraalVM
In April 2024, Oracle announced a new security vulnerability: CVE-2024-21140. This hard-to-exploit flaw affects multiple versions of Oracle Java SE, Oracle GraalVM for JDK, and
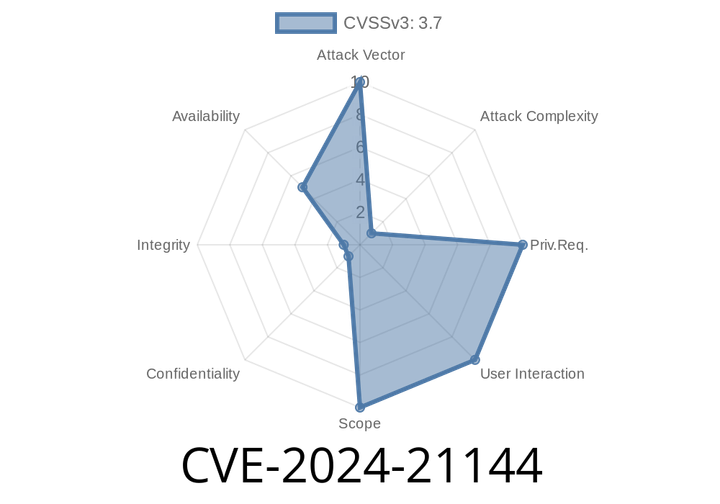
CVE-2024-21144 - Partial Denial of Service Vulnerability in Oracle Java SE and Oracle GraalVM Enterprise Edition
In June 2024, Oracle published a security advisory regarding CVE-2024-21144, a vulnerability found in the Concurrency component of Oracle Java SE and Oracle GraalVM Enterprise
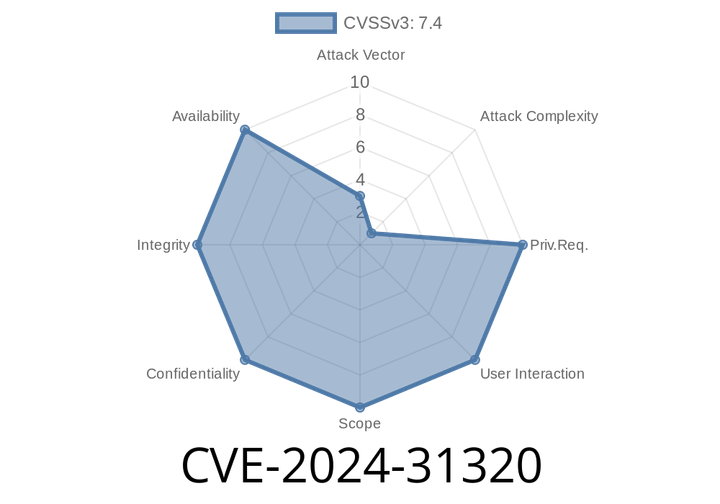
CVE-2024-31320 - How a Silent Companion Device Association Bug Can Escalate Privileges on Android
In early 2024, a new Android security vulnerability was discovered and tracked as CVE-2024-31320. It resides in the setSkipPrompt method of AssociationRequest.java. This flaw
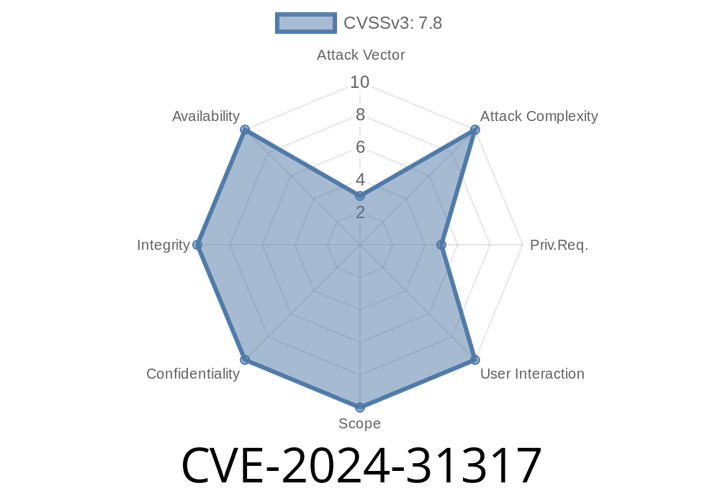
CVE-2024-31317 - Unsafe Deserialization in ZygoteProcess.java Leads to Local Privilege Escalation on Android
In April 2024, a critical security flaw—CVE-2024-31317—was uncovered in Android's system internals. This vulnerability lies in the way multiple functions in
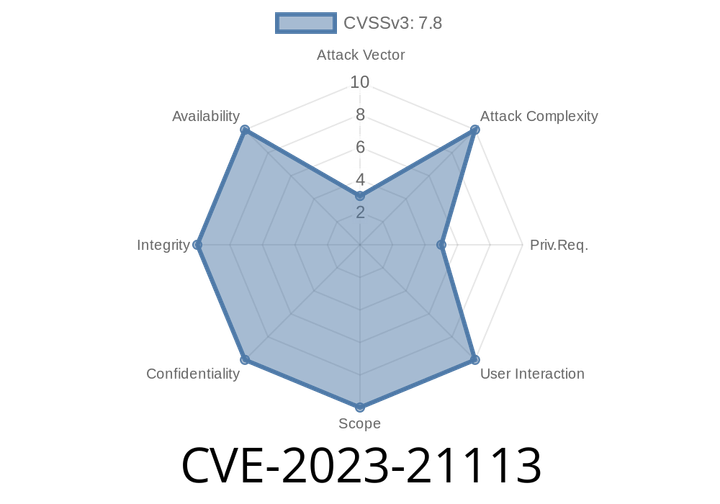
CVE-2023-21113 - Exploiting Android's Confused Deputy for Local Privilege Escalation
CVE-2023-21113 is a security vulnerability discovered in the Android platform. This flaw arises from a common security issue called a confused deputy problem, allowing local
Episode
00:00:00
00:00:00