CVE-2024-30172 - Bouncy Castle Ed25519 Infinite Loop Exploit Explained (with Code Examples)
*Published June 2024*
Bouncy Castle is a popular set of cryptography libraries in Java and other languages. But even the most trusted security tools sometimes
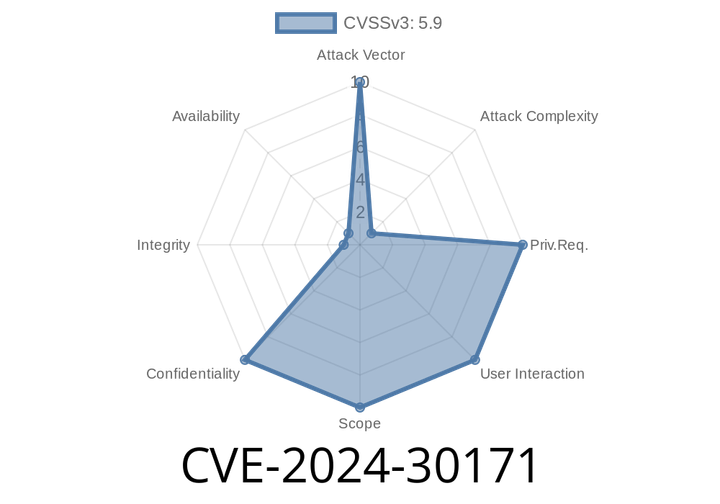
CVE-2024-30171 - Timing Attack Risk in Bouncy Castle’s Java TLS API and JSSE Provider – Explained, Exploited, and Patched
Bouncy Castle is one of the most trusted libraries for cryptographic operations in Java. Used by developers and organizations worldwide, its TLS API and JSSE
CVE-2024-29857 - Exploiting Excessive CPU Usage in Bouncy Castle ECCurve Certificate Parsing
CVE-2024-29857 is a recently disclosed vulnerability affecting a family of cryptographic libraries known as Bouncy Castle. This issue revolves around how the libraries handle certain
CVE-2024-23712 - Exploiting Android’s AppOpsService for Local Denial of Service
Android is celebrated for its balance between openness and security, but no operating system is immune from bugs. One of the recent discoveries, CVE-2024-23712, sheds
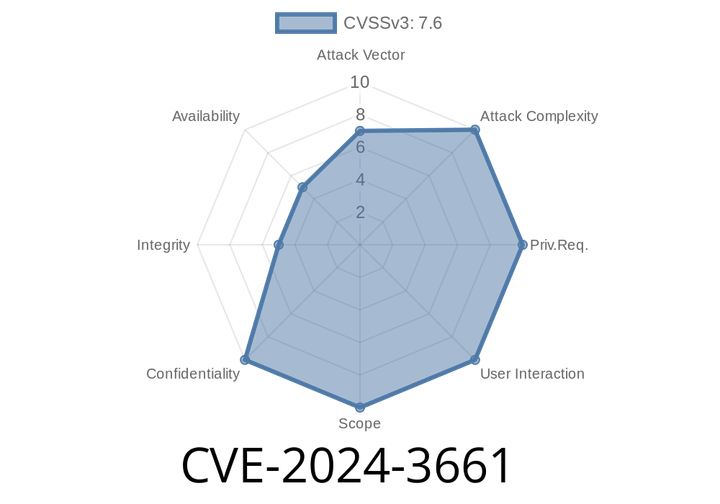
CVE-2024-3661 - How DHCP Route Injection Exposes VPN Traffic to Attackers (With Exploit Example)
Summary:
A new vulnerability, CVE-2024-3661, exposes a flaw in how VPNs rely on routing rules for security. By abusing DHCP’s _classless static route option_
Episode
00:00:00
00:00:00