CVE-2024-34447 - How Bouncy Castle’s Java APIs Let DNS Poisoning Slip Through — Details, Code, and Exploitation
If you use Java for SSL communication, chances are you've bumped into Bouncy Castle, a popular library for cryptographic functions. But until version
CVE-2023-42119 - Exim dnsdb Out-Of-Bounds Read Allows Information Disclosure (With Exploit Example)
Exim is a popular mail transfer agent (MTA), and like many services running on the internet, its security is crucial. In September 2023, a security
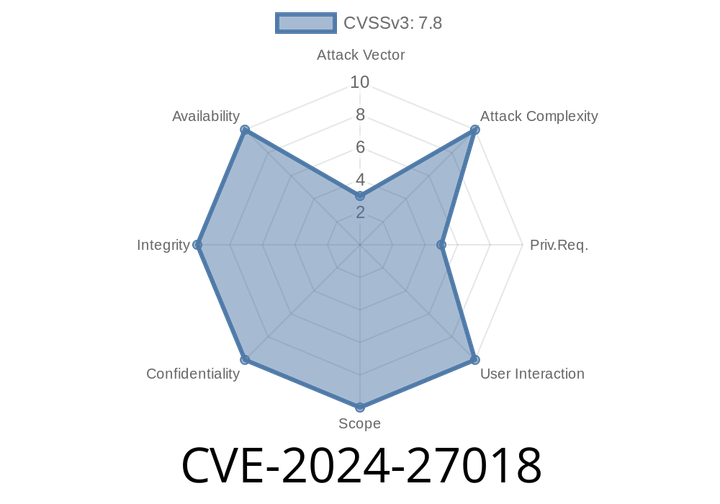
CVE-2024-27018 - Linux Kernel br_netfilter Promiscuous Conntrack Vulnerability Explained
- CVE: CVE-2024-27018
Component: Linux Kernel br_netfilter
- Bug: Conntrack input hook is wrongly triggered for promiscuous bridge packets, leading to kernel warnings and
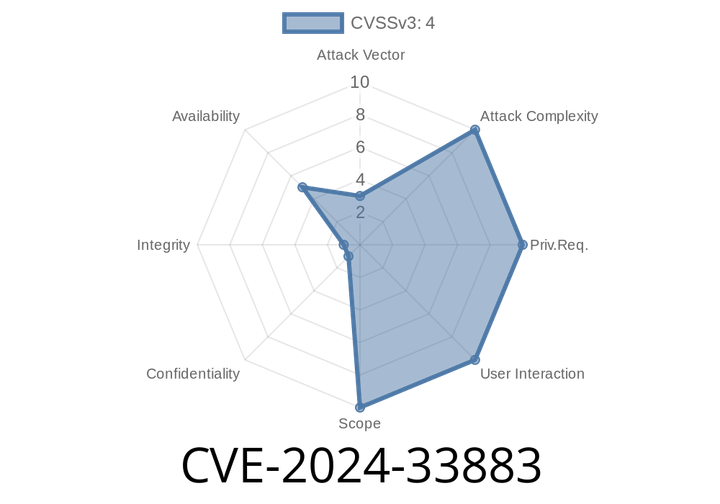
CVE-2024-33883 - Exploiting Prototype Pollution in EJS Before 3.1.10 — How Node.js Applications Got Vulnerable
Embedded JavaScript templates, better known as EJS, is a staple for countless Node.js web apps. It lets you combine JavaScript with HTML templates, making
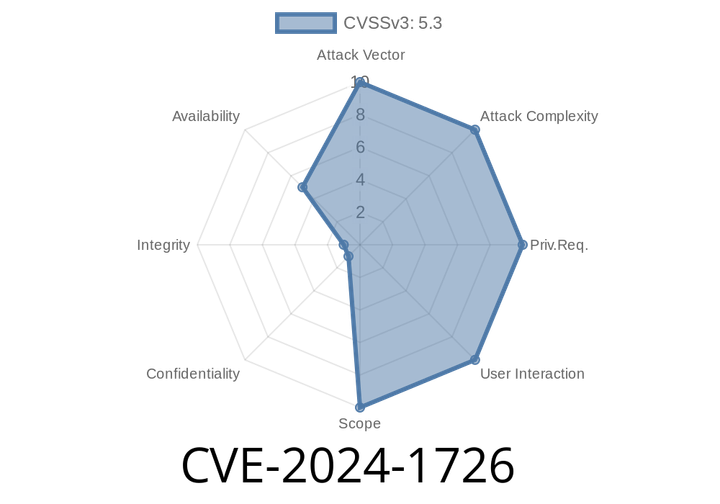
CVE-2024-1726 - Denial of Service Risk in Quarkus RESTEasy Reactive – Explained Step By Step
A recent security flaw, identified as CVE-2024-1726, has been discovered in the RESTEasy Reactive implementation within the popular Quarkus Java framework. The issue revolves around
Episode
00:00:00
00:00:00