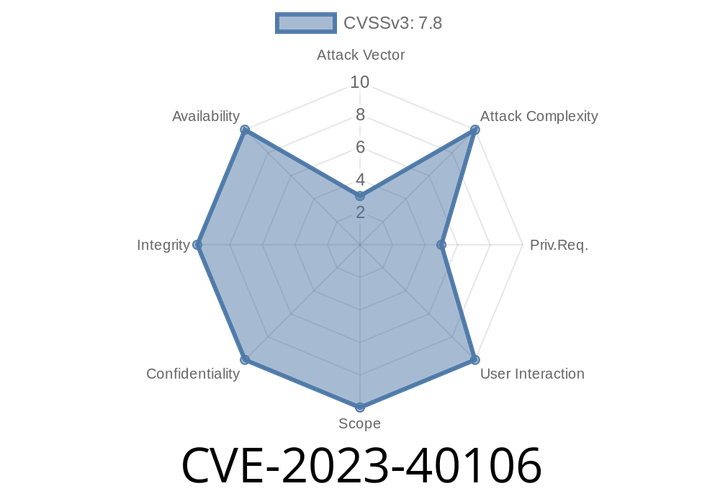
CVE-2023-40106 - Deep Dive Into Android NotificationManagerService BAL Bypass Exploit
Android security continues to be a cat-and-mouse game, with researchers and attackers constantly discovering new holes and methods to exploit them. Recently, a noteworthy vulnerability
CVE-2023-40113 - Exploiting Missing Permission Checks to Access Cross-User Messages in Android
In recent years, Android has worked hard to tighten permissions and keep user data secure. But even with these protections, sometimes small mistakes slip through.
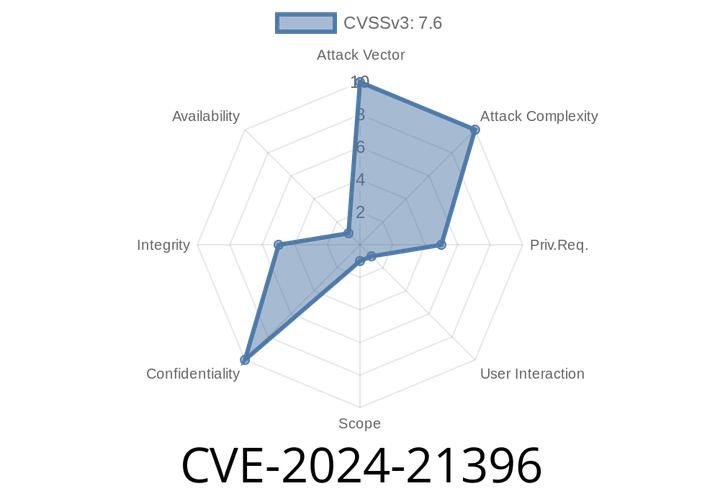
CVE-2024-21396 - Dynamics 365 Sales Spoofing Vulnerability Explained (With Example & Exploit)
CVE-2024-21396 is a serious spoofing vulnerability discovered in Microsoft Dynamics 365 Sales. It allows attackers to impersonate legitimate users through manipulated URLs and malicious requests.
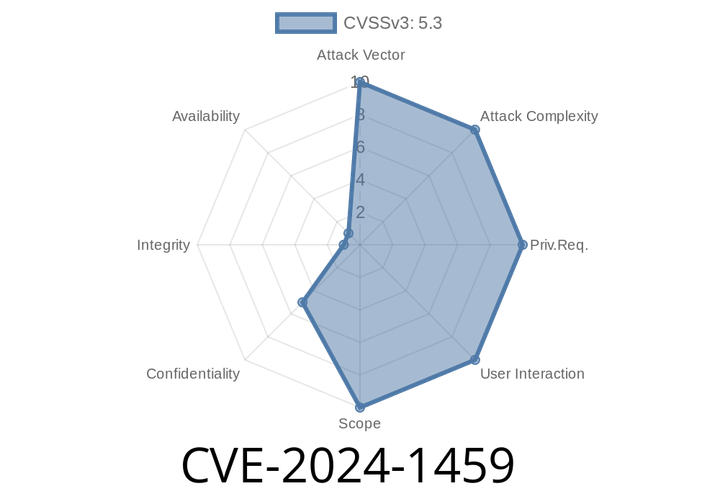
CVE-2024-1459 - Path Traversal Vulnerability in Undertow Explained (With Exploit Details)
In March 2024, a worrying path traversal vulnerability was discovered in Undertow — the popular Java web server used internally by JBoss EAP and WildFly app
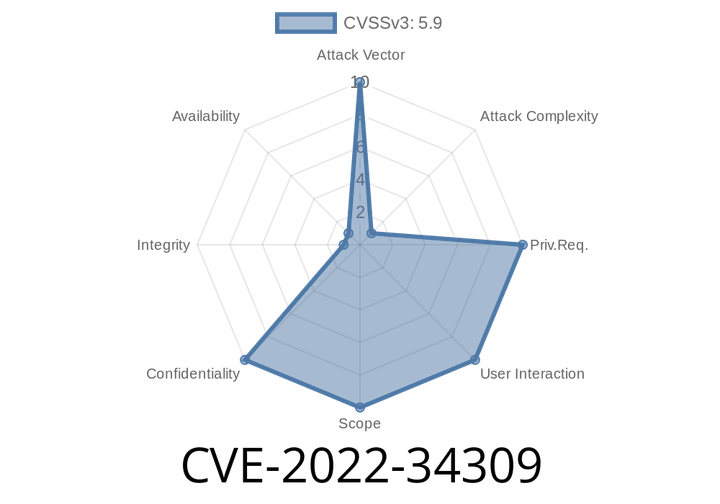
CVE-2022-34309 - How Weaker Encryption in IBM CICS TX 11.1 Could Expose Sensitive Data
In June 2022, researchers discovered a serious cryptography flaw in IBM CICS TX Standard and Advanced 11.1. Registered under CVE-2022-34309 and tracked by IBM
Episode
00:00:00
00:00:00